Dozens of Global Companies Hacked via Cloud Credentials from Infostealer Infections & More at Risk
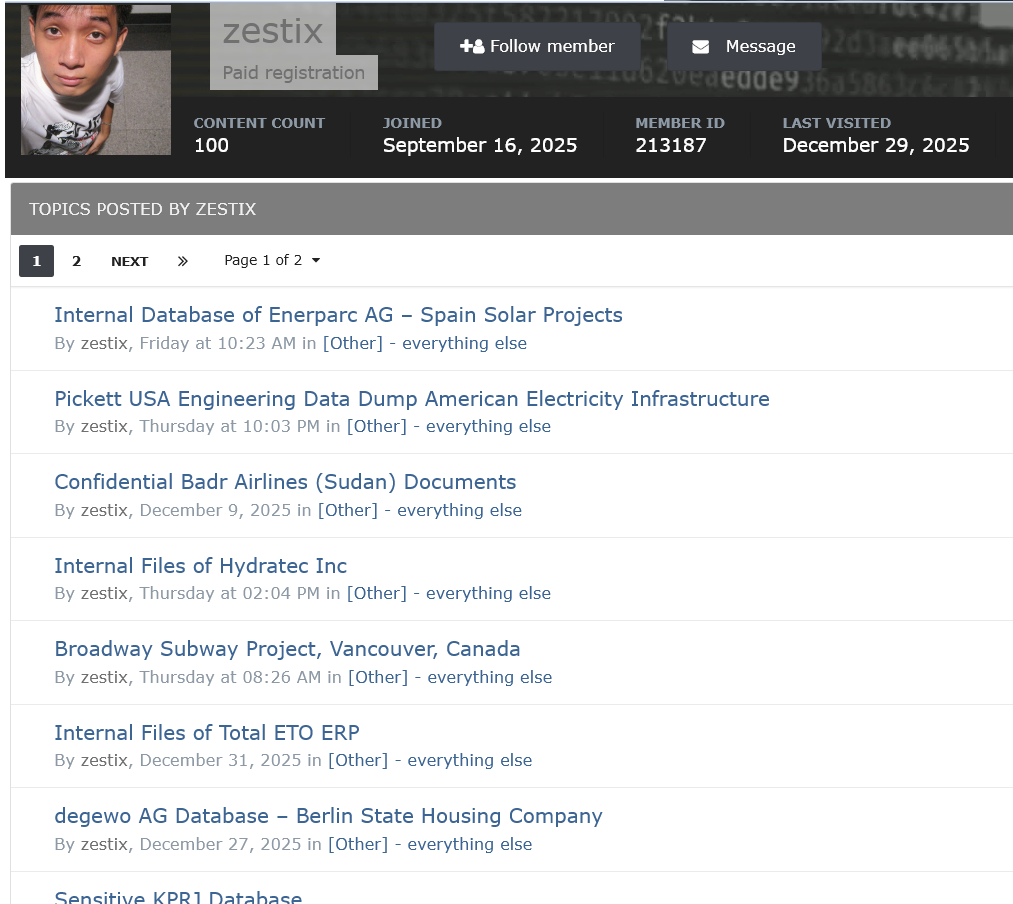
Table of Contents
- 1. Executive Summary
- 2. The Threat Landscape: Infostealers & 2FA
- 3. Platform Analysis: The Vulnerable Giants
- 4. Threat Actor Profile: Zestix & Sentap
- 5. Victim Analysis: The Portfolio
- 6. The Preventability: Intelligence Gap
- 7. Conclusion & Victim Tables
- 8. Beyond Zestix: A Global Epidemic (& Checking Your Own Company Exposure)
1. Executive Summary
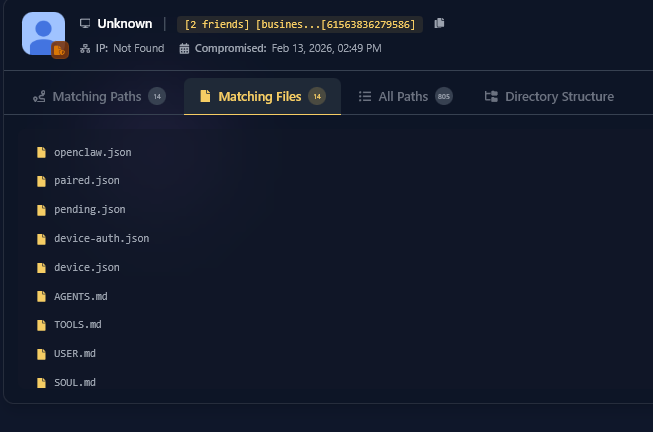
A high-profile threat actor, operating under the moniker “Zestix” (also operating under the alias “Sentap”), has been identified auctioning data exfiltrated from the corporate file-sharing portals of approximately 50 major global enterprises. This report serves as an exhaustive analysis of this campaign, offering direct evidence for key compromises, detailing the breach of ShareFile, OwnCloud, and Nextcloud instances belonging to critical entities across the aviation, robotics, housing, and government infrastructure sectors.
The following investigation, conducted exclusively for Infostealers.com by Hudson Rock, dissects the sale of credentials extracted from “Infostealer” logs for distinct victims including Pickett, Sekisui House, IFLUSAC, Iberia Airlines, K3G Solutions, CRRC MA, GreenBills, CiberC, and many others.
This report provides a granular reconstruction of the compromised assets. Furthermore, we demonstrate that these catastrophic security failures were not the result of zero-day exploits in the platform architecture, but rather the downstream effect of malware infections on employee devices combined with a critical failure to enforce Multi-Factor Authentication (MFA).
2. The Threat Landscape: The Ascendancy of Infostealers
To comprehend the severity of the breaches affecting giants like Sekisui House and Iberia, one must first dissect the evolving mechanism of initial access. The era where brute-force attacks reigned supreme is waning. In its place, the Infostealer ecosystem has risen to become the primary engine of modern cybercrime.
2.1 The Mechanics: Credential Abuse & Lack of 2FA
Contrary to attacks involving sophisticated cookie hijacking or session bypasses, the Zestix campaign highlights a far more pedestrian – yet equally devastating – oversight: The absence of Multi-Factor Authentication (2FA).
When an employee logs into corporate portals like hydratec.sharefile.com or fileshare.intecro.com.tr, they assume their password is enough. However, Zestix relies on the widespread distribution of Infostealer malware (such as RedLine, Lumma, or Vidar) to infect personal or professional devices.
A Time Bomb in the Logs: A critical finding in this investigation is the latency of the threat. While some credentials were harvested from recently infected machines, others had been sitting in logs for years, waiting for an actor like Zestix to exploit them. This highlights a pervasive failure in credential hygiene; passwords were not rotated, and sessions were never invalidated, turning a years-old infection into a present-day catastrophe.
The Attack Flow
- Infection: An employee inadvertently downloads a malicious file. The infostealer executes and harvests all saved credentials and browser history.
- Aggregation: These logs are aggregated in massive databases on the dark web. Zestix parses these logs specifically looking for corporate cloud URLs (ShareFile, Nextcloud).
- The Access: Zestix simply uses the valid username and password extracted from the logs. Because the organizations listed below did not enforce MFA, the attacker walks right in through the front door. No exploits, no cookies – just a password.
3. Platform Analysis: The Vulnerable Giants
The targets in this campaign utilize enterprise-grade file synchronization and sharing (EFSS) platforms – specifically ShareFile, Nextcloud, and OwnCloud. While these platforms support robust security, they are only as strong as their configuration.
- ShareFile (Progress Software): Used by legal and engineering firms. The breach points identified include domains like
wwhgd.sharefile.comandiberiaexpress.sharefile.com. - Nextcloud/OwnCloud: Used by entities like K3G and Maida. Vulnerable instances were identified at
owncloud.k3gsolutions.com.brandnextcloud.maida.net.
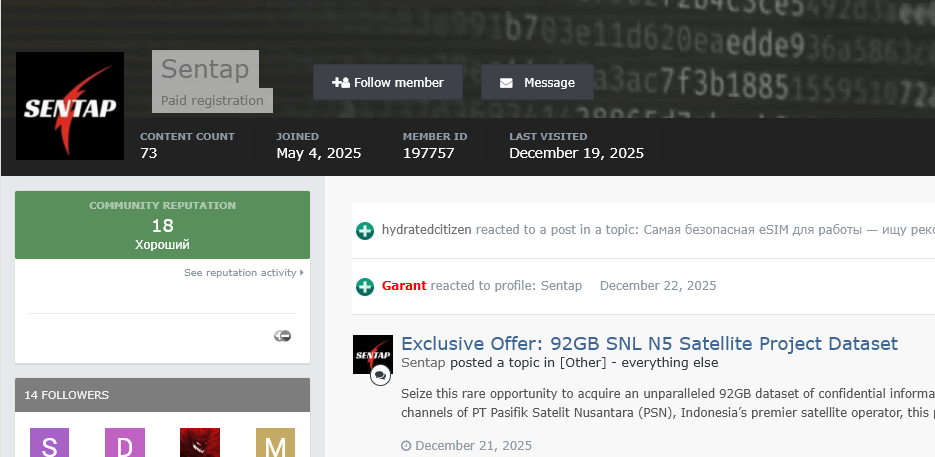
4. Threat Actor Profile: Zestix & Sentap
Intelligence derived from dark web monitoring paints a detailed picture of Zestix. First identified as a distinct entity around late 2024 to early 2025, Zestix has quickly established a reputation for reliability. The actor operates comfortably within Russian-language closed forums and is motivated purely by financial gain, selling access for Bitcoin as an Initial Access Broker (IAB).
Dual Identity Discovery: Further analysis has linked Zestix to another active handle, “Sentap,” on various forums. Under this alias, the actor has expanded their portfolio, listing dozens of additional companies traced back to similar Infostealer infections.
Attribution & Origins: Recent research by DarkSignal has linked the “Sentap” persona to an Iranian national. Active since at least 2021, the actor employs an opportunistic “Trust Abuse Model,” targeting exposed infrastructure and third-party access. Furthermore, Sentap has demonstrated clear affiliations with the Funksec cybercriminal group, aligning with their modus operandi of high-volume, opportunistic attacks.
5. Victim Analysis: The Zestix/Sentap Portfolio
The following sections detail the specific organizations identified in the Zestix and Sentap sales threads. By correlating the provided images and metadata with open-source intelligence (OSINT), we have reconstructed the likely breach points and operational impacts for each victim.
5.1 Pickett & Associates
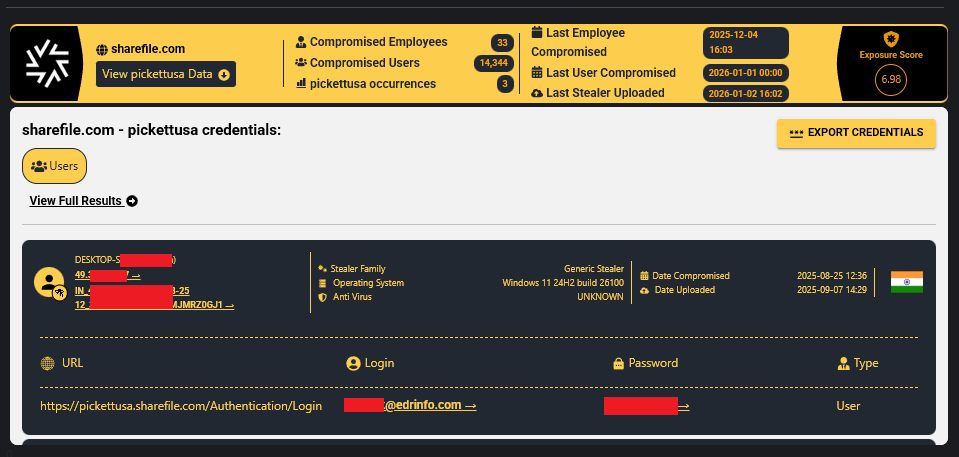
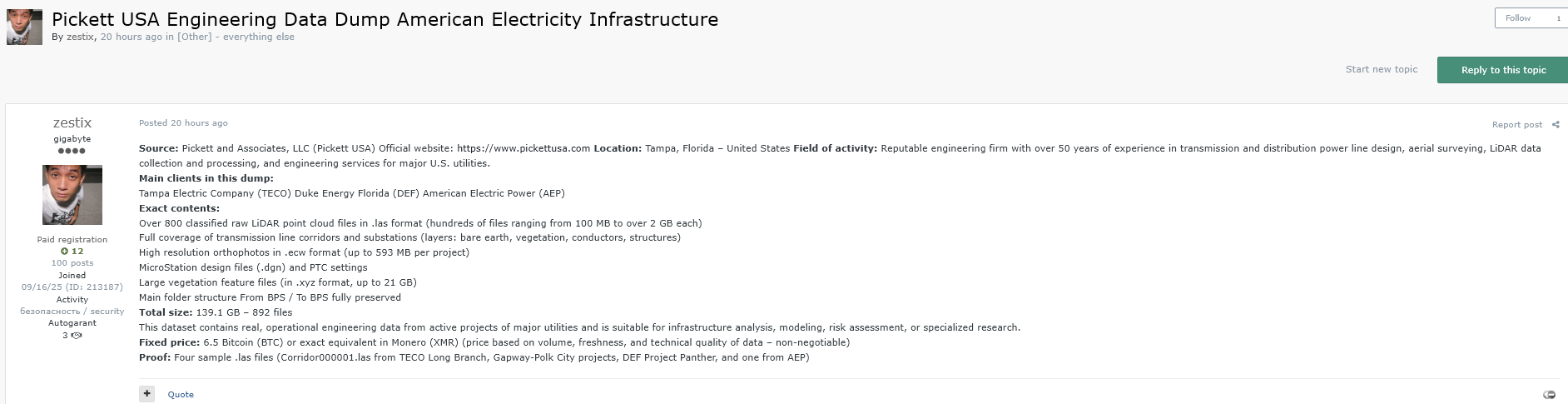
Access URL: pickettusa.sharefile.com
The Profile: Pickett & Associates is a reputable engineering firm with over 50 years of experience in transmission and distribution power line design, aerial surveying, and LiDAR data collection. Their major clients include Tampa Electric Company (TECO), Duke Energy Florida, and American Electric Power (AEP).
The Leak (139.1 GB): The compromised data is massive and highly sensitive.
- 800+ Classified LiDAR Files: Raw point cloud files (.las) ranging from 100MB to 2GB each, covering transmission line corridors and substations.
- Operational Blueprints: High-resolution orthophotos (.ecw), MicroStation design files (.dgn), and large vegetation feature files.
- Risk: This dataset is suitable for infrastructure analysis, risk assessment, or even physical sabotage planning against U.S. utilities.
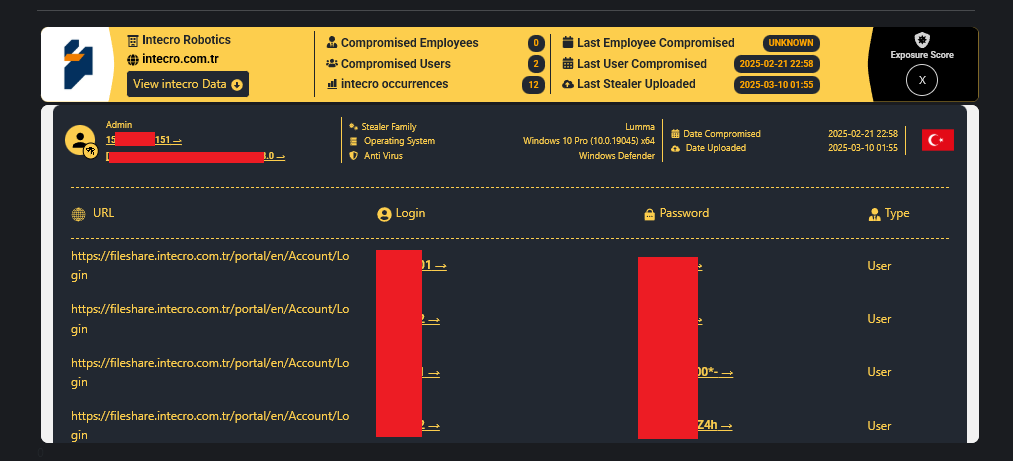
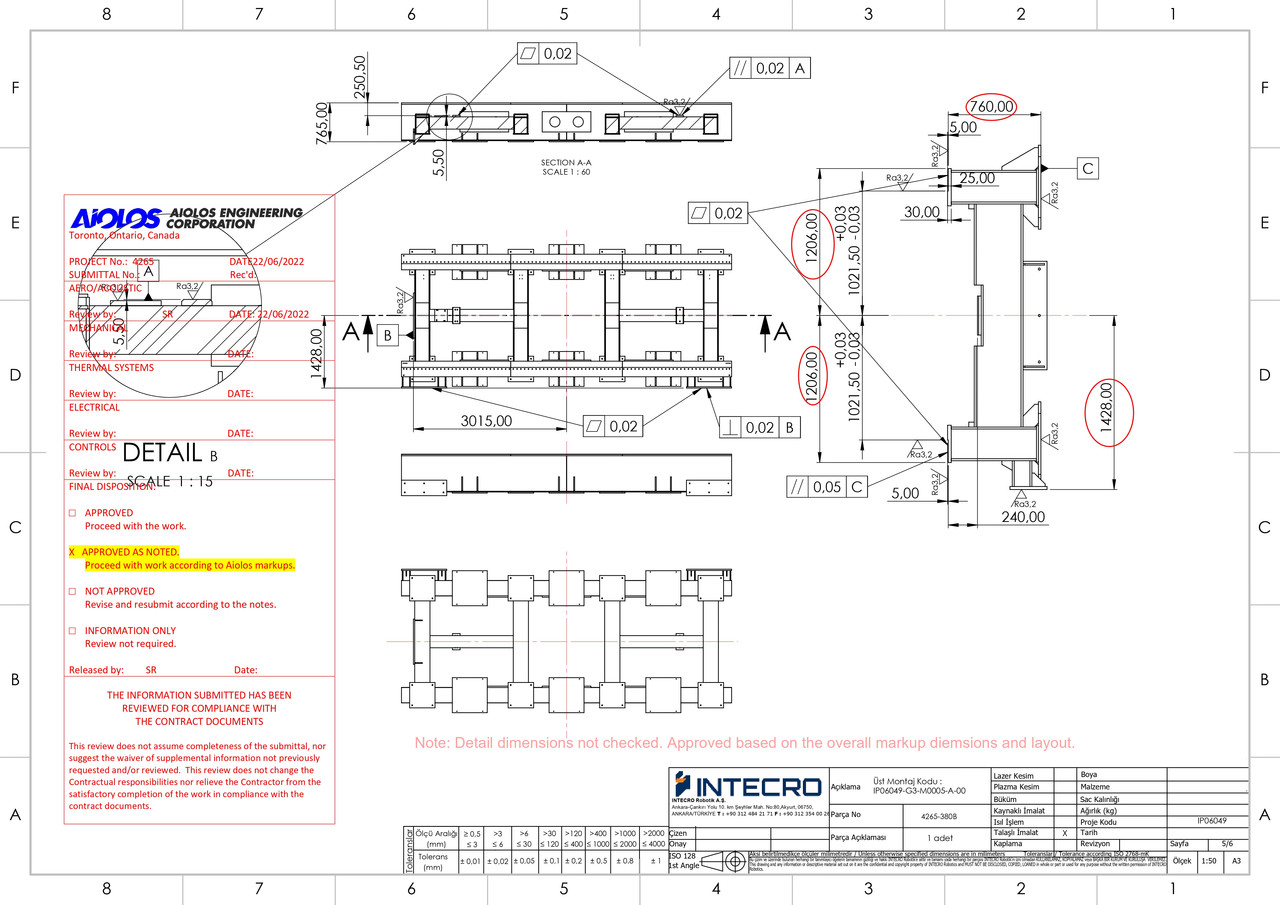
5.2 Intecro Robotics (Turkey)
Access URL: fileshare.intecro.com.tr
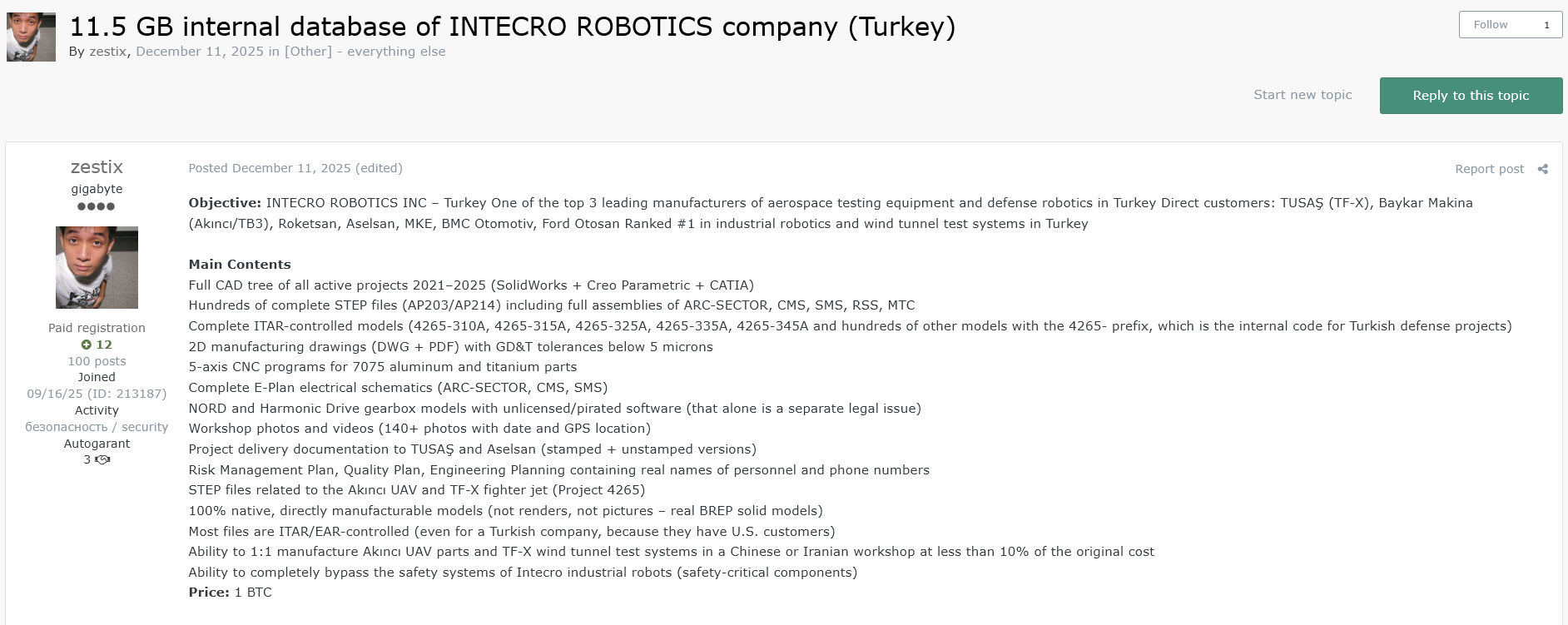
The Profile: Intecro is a top manufacturer of aerospace testing equipment and defense robotics in Turkey. Their direct customers include TUSAŞ (TF-X fighter jet), Baykar Makina (Akıncı/TB3 UAVs), Roketsan, and Aselsan.
The Leak (11.5 GB): This breach contains critical military intellectual property.
- Defense Projects: STEP files related to the Akıncı UAV and TF-X fighter jet (Project 4265).
- ITAR Controlled Data: Complete ITAR-controlled models (4265-prefix codes), 2D manufacturing drawings with high-precision tolerances, and 5-axis CNC programs for titanium parts.
- Impact: The actor claims this data allows for the 1:1 manufacture of safety-critical components and wind tunnel test systems in unlicensed workshops.
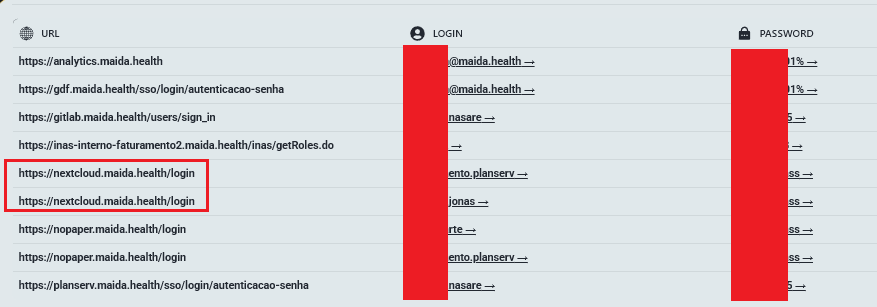
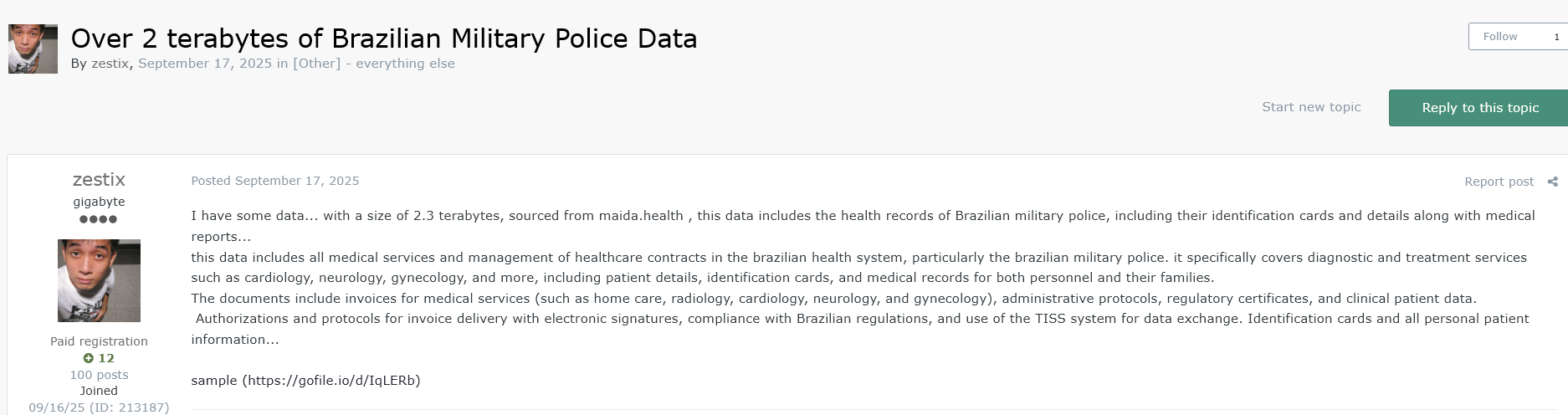
5.3 Maida Health (Brazil)
Access URL: nextcloud.maida.net
The Leak (2.3 TB): One of the largest datasets in the portfolio, this breach covers the health records of the Brazilian Military Police.
- Sensitive PII: Identification cards, medical reports, and family details of military personnel.
- Medical Records: Invoices and records for cardiology, neurology, and gynecology services.
- Risk: A massive privacy violation and potential national security risk for Brazil, exposing the personal lives of security forces.
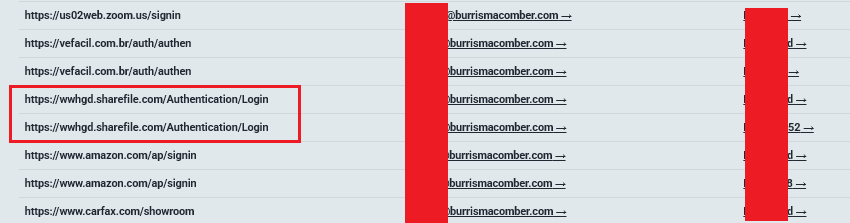
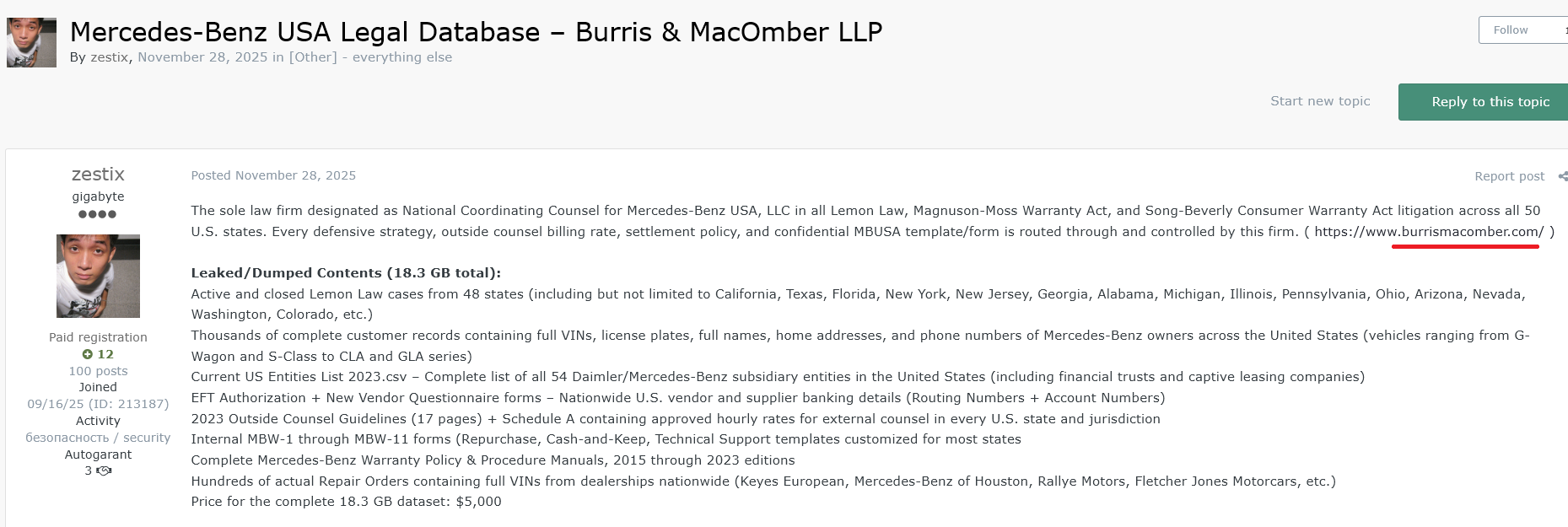
5.4 Burris & Macomber (Mercedes-Benz Counsel)
Access URL: wwhgd.sharefile.com
The Profile: This law firm acts as the National Coordinating Counsel for Mercedes-Benz USA in Lemon Law and warranty litigation.
The Leak (18.3 GB):
- Litigation Strategy: Active Lemon Law cases from 48 states, defense strategies, and settlement policies.
- Customer Data: Thousands of records containing VINs, license plates, home addresses, and phone numbers of Mercedes-Benz owners (G-Wagon, S-Class, etc.).
- Corporate secrets: 2023 Outside Counsel Guidelines and approved billing rates.
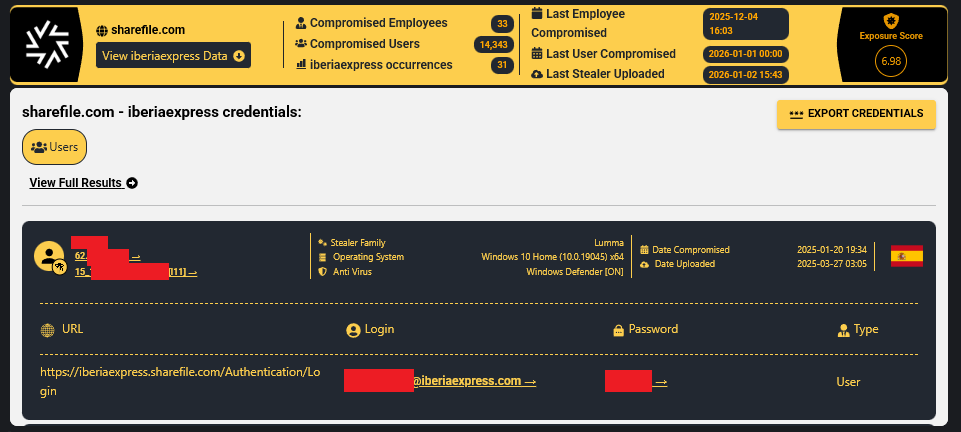
5.5 Iberia Airlines
Access URL: iberiaexpress.sharefile.com
The Profile: Iberia is the flag carrier of Spain. The breach point was identified via an employee login.
The Leak (77 GB):
- Technical Safety Data: AMP maintenance programs for A320/A321, Airworthiness Limitation Sections (ALS), and aircraft damage charts.
- Confidential Fleet Data: AOC (Air Operator Certificate) details, database dumps from the Airbus ACDATA system, and CSV files containing mappings for critical parts.
- Risk: Industrial espionage and potential extortion. The data includes digital signatures and proprietary configuration variations valuable to competitors or state actors.

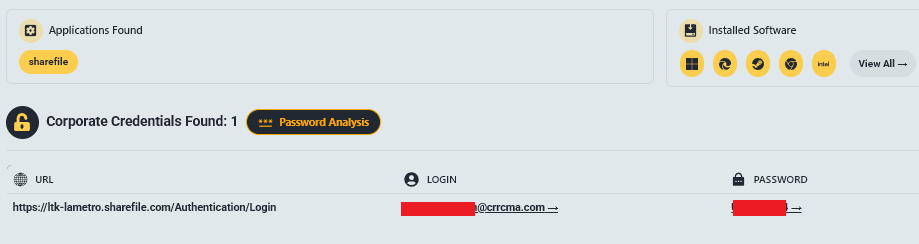
5.6 CRRC MA (Mass Transit)
Access URL: ltk-lametro.sharefile.com
The Profile: CRRC MA is the Massachusetts subsidiary of the world’s largest rolling stock manufacturer, building trains for LA Metro and MBTA.
The Leak (100% of Engineering Servers):
- LA Metro HR4000: Complete signaling drawings, SCADA RTU lists, and “deliberately withheld” test reports regarding doors, HVAC, and propulsion systems.
- Security Info: Precise GPS coordinates of control rooms and battery rooms (Sensitive Security Information).
- Blueprint Exposure: Full carbody, bogie, and brake system drawings (2D + 3D STEP), wiring schematics, and software firmware lists.

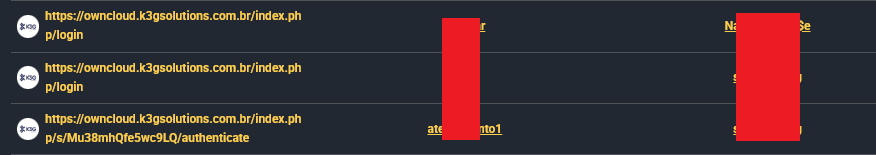
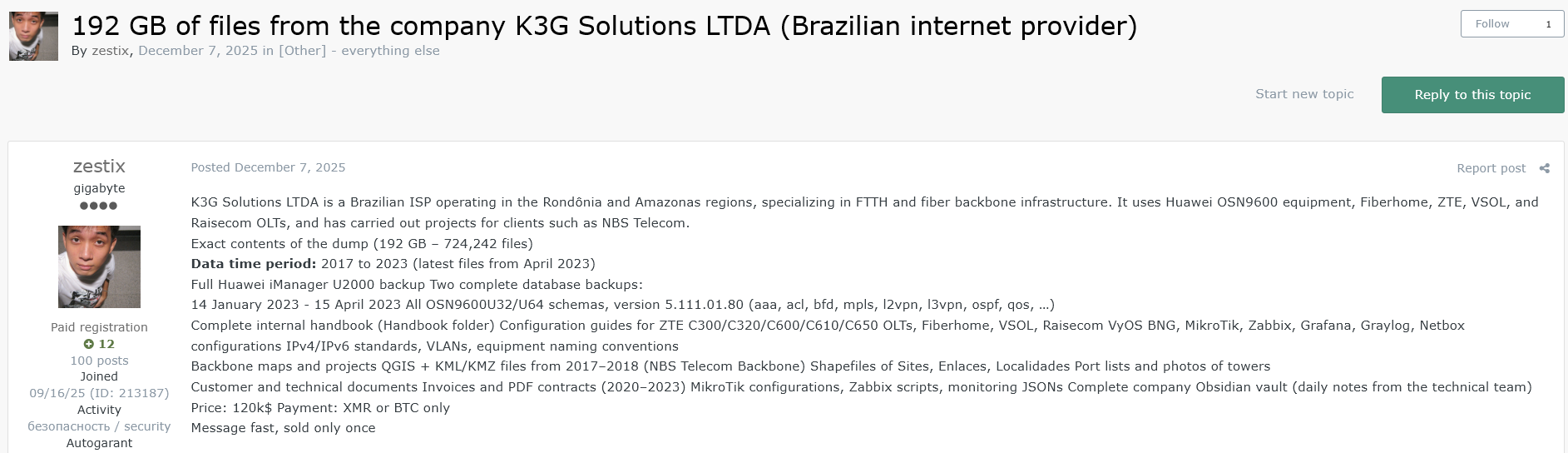
5.7 K3G Solutions
Access URL: owncloud.k3gsolutions.com.br
The Profile: A Brazilian ISP and software agency specializing in FTTH and fiber backbone infrastructure.
The Leak (192 GB): Over 724,000 files covering the period from 2017 to 2023.
- Network Configs: Full Huawei iManager U2000 backups, OLT configurations (ZTE, Fiberhome), and backbone maps (QGIS/KML).
- Security Risk: Includes port lists, tower photos, and complete internal handbooks for network management.
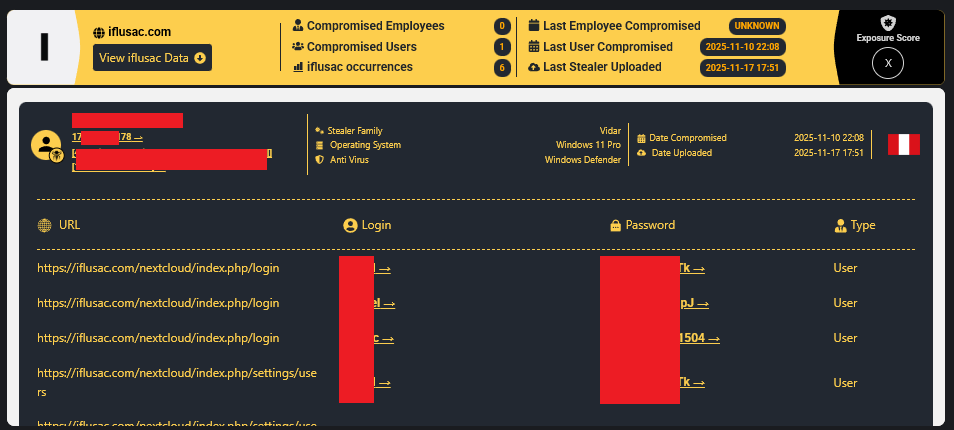
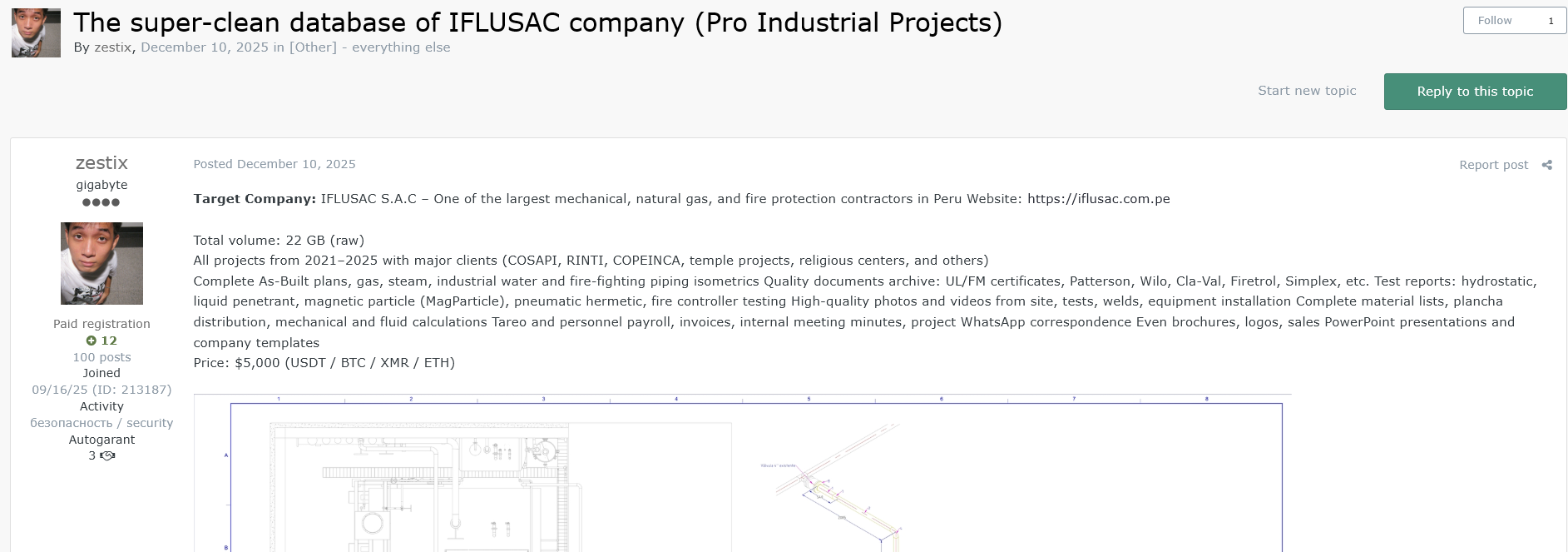
5.8 IFLUSAC
Access URL: iflusac.com/nextcloud
The Profile: One of the largest mechanical and fire protection contractors in Peru.
The Leak (22 GB): Includes all projects from 2021–2025 with major clients like COSAPI.
- Engineering Data: As-Built plans, piping isometrics, and quality documents (UL/FM certificates).
- Business Data: Payroll, invoices, and internal meeting minutes.
5.9 GreenBills
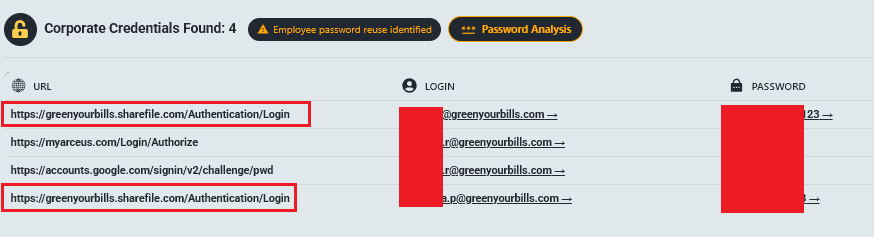
Access URL: greenyourbills.sharefile.com
The Leak (39.52 GB): Over 111,000 PDF files pertaining to real patients (2020-2023).
- HIPAA Violation: Complete intake forms, medical reports (IE/FU/Final), and signed assignment of benefits.
- Sensitive Data: Full names, DOBS, incident details, and treatment descriptions for workers’ comp and injury claims.
5.10 CiberC
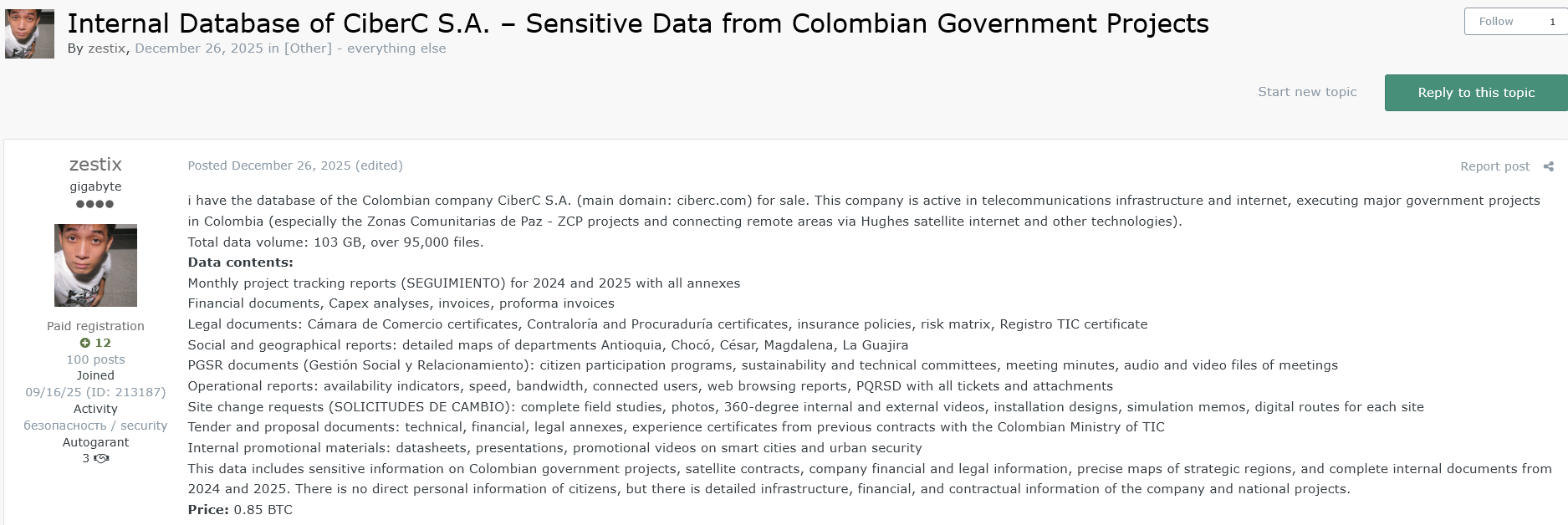
Access URL: ciberc.sharefile.com
The Profile: A major technology integrator and Cisco Gold Partner in Colombia.
The Leak (103 GB): 95,000+ files including monthly project tracking reports for government contracts (Zonas Comunitarias de Paz). Includes detailed maps of strategic regions, site change requests, and 360-degree videos of infrastructure.
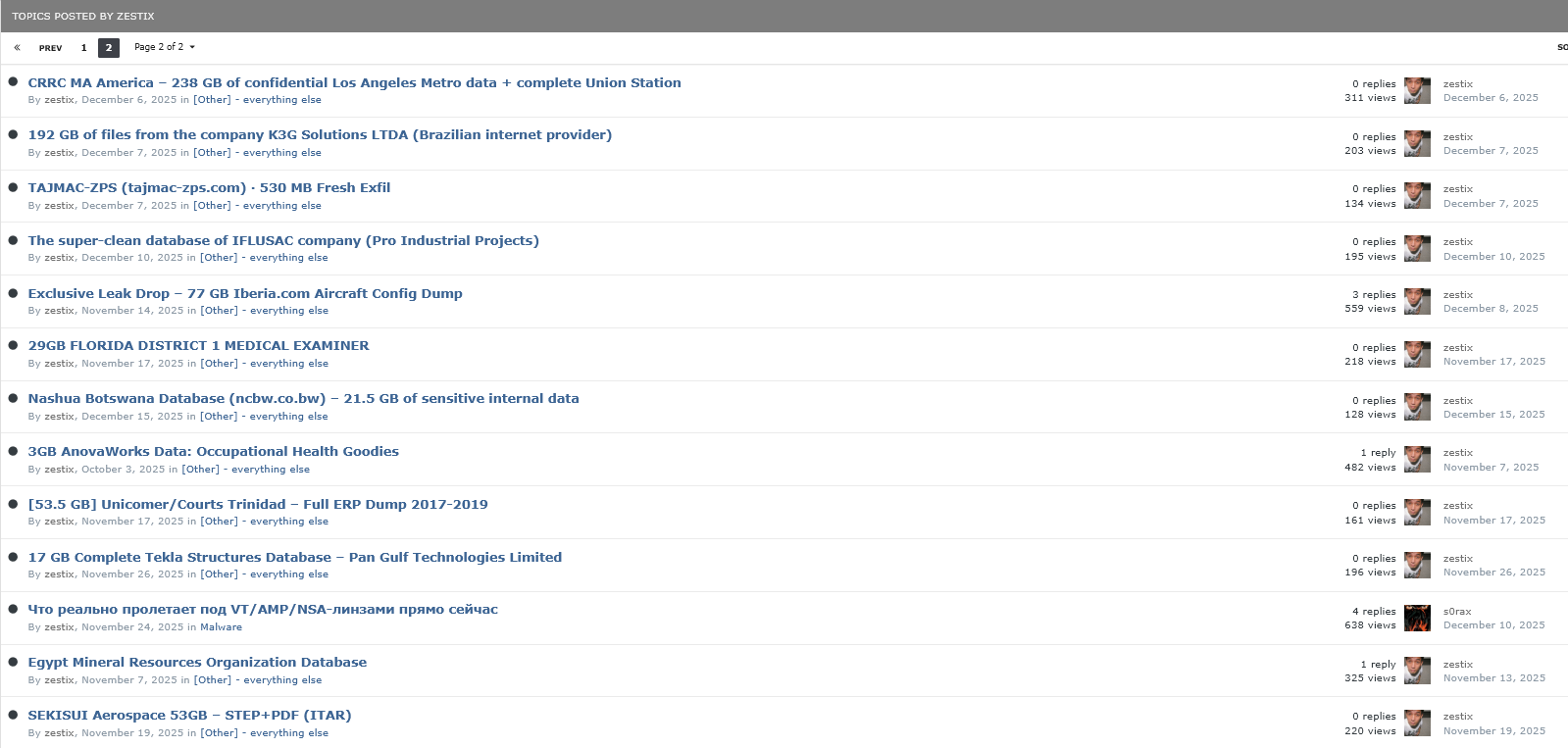
5.11 Other Notable Compromises
The Zestix portfolio extends to numerous other entities, all breached via the same dual failure: an employee downloading Infostealer malware, and the organization failing to enforce MFA.
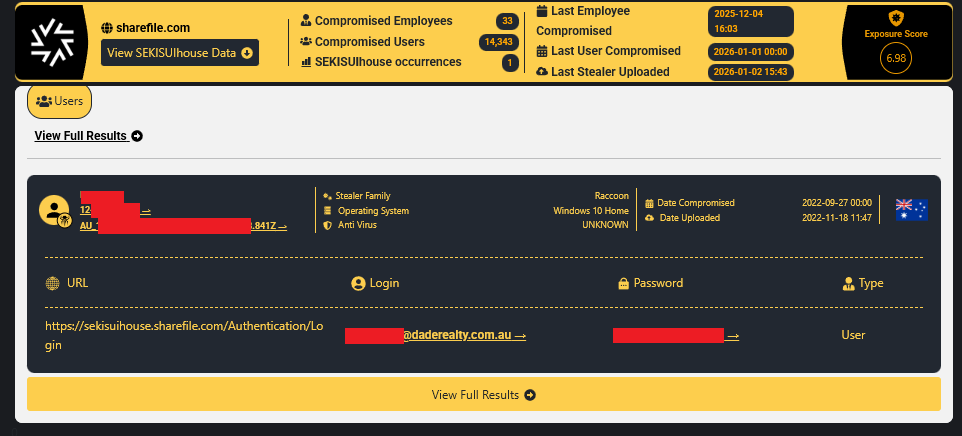
- Sekisui House:
sekisuihouse.sharefile.com(Access marked as SOLD). - Hydratec Inc.:
hydratec.sharefile.com(81 GB of Fire Protection CAD software builds and training videos). - Total ETO:
totaleto.sharefile.com(28.95 GB of ERP software source code and customer database backups). - Degewo AG:
dagewo.sharefile.eu(5.5 GB of architectural plans for Berlin state housing). - ThermoEx:
nextcloud.themoex.com(170 GB of heat exchanger designs and financial POs from Thailand). - Voltras:
nextcloud.voltras.net(Complete internal financial archive of a major Indonesian travel aggregator).
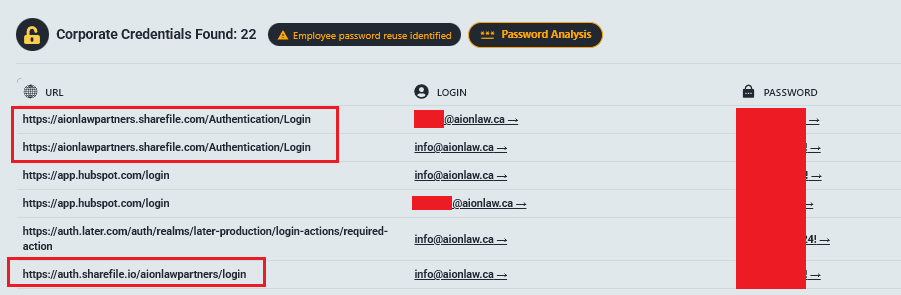
5.12 Aion Law Partners LLP
Access URL: aionlawpartners.sharefile.com
The Profile: A reputable law firm based in Ontario, Canada, specializing in family law, real estate, immigration, and corporate governance.
The Leak (38 GB): Legal, financial, immigration, and corporate documents.
- Sensitive Client Data: Affidavits, judicial forms, retainer agreements, and rulings from the Ontario Superior Court.
- Financials: Bank statements (2019-2021) with account numbers, transaction details, and client addresses.

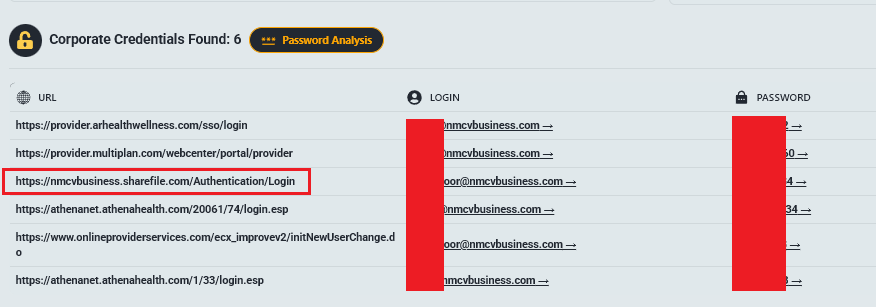
5.13 NMCV Business LLC
Access URL: nmcvbusiness.sharefile.com
The Profile: A platform managing medical and financial data for U.S. healthcare facilities like First US Clinic PA and Jefferson Regional Medical Center.
The Leak (47 GB): A massive archive of raw medical and financial data from 2017-2025.
- PHI Exposure: Patient admission forms, advance eligibility reports, and handwritten vital sign monitoring tables.
- Financial Data: Medical payment records based on CPT codes and Medicaid benefit renewal forms.
5.14 PT Pasifik Satelit Nusantara (PSN)
Access URL: nextcloud.psn.co.id
The Profile: Indonesia’s premier satellite operator, providing critical connectivity for governments and military.
The Leak (92 GB): Confidential data from the SNL N5 satellite project.
- Aerospace Secrets: Technical documents from Boeing, SpaceX, and Kratos regarding satellite manufacturing and launch services.
- Operational Risks: Anomaly reports, TT&C ground system data, and C-band antenna schematics.
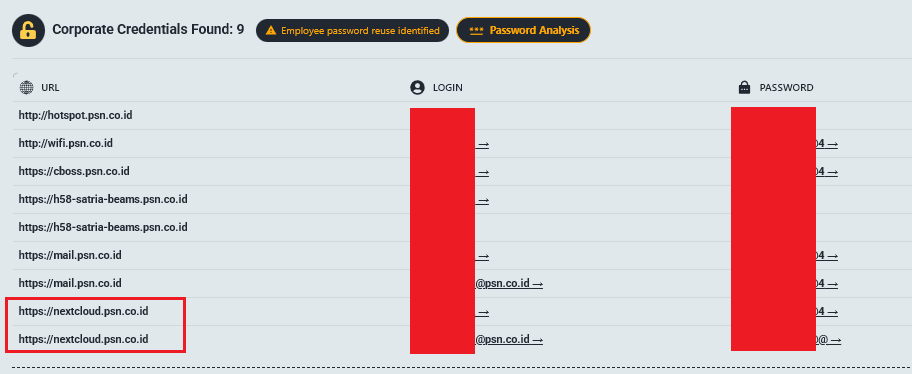

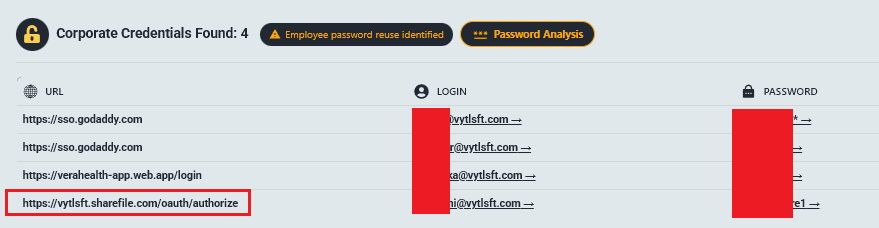
5.15 VYTL-SFT (Verahealth)
Access URL: vyslsft.sharefile.com
The Profile: An advanced healthcare software platform used by U.S. clinics for automating clinical processes.
The Leak (3.65 GB): Raw data extracted from the platform’s database.
- Highly Sensitive PHI: Full patient information including SSNs, insurance details, and medical codes (ICD-10/CPT).
- Clinical Notes: Diagnoses and treatment plans for athletes and general patients, including psychiatric conditions.

6. The Preventability of the Breach: The Hudson Rock Advantage
The tragedy of the Zestix portfolio is not the sophistication of the attack, but its banality. These companies were not hacked by a quantum computer cracking encryption; they were hacked because an employee infected their device with an Infostealer, and the organization failed to turn on 2-Factor Authentication.
6.1 The Intelligence Gap
Traditional cybersecurity tools (Firewalls, EDR, SIEM) are designed to defend the perimeter and the endpoint. They can stop malware executing on a corporate laptop, but they are blind to the “Third Space”: The personal devices of employees and contractors.
6.2 Hudson Rock’s Solution
Hudson Rock operates a unique intelligence platform (Cavalier) that bridges this gap. By meticulously tracking the global spread of infostealers and indexing the logs exfiltrated to criminal C2 servers, Hudson Rock identifies compromised credentials before they are weaponized.
“Long before Zestix listed ‘Iberia’ for sale, Hudson Rock’s system would have detected the compromised computer. In some instances, we observe credentials sitting in these logs for years before an actor like Zestix exploits them – a window of opportunity for remediation that was missed.”
7. Conclusion
The Zestix campaign is a wake-up call for the corporate world. The enemies are no longer just at the gates; they are walking through them with stolen keys. The breaches of Pickett, Intecro, Maida, Iberia, and others demonstrate that no sector is immune.
In the digital age, access is the only currency that matters. It is time for organizations to enforce MFA and monitor their employees’ compromised credentials.
7.1 Analyzed Victims
The table below summarizes the key victims detailed in this report.
| Victim Entity | Data Volume | Risk |
|---|---|---|
| Pickett | 139.1 GB | Critical Utility Maps & LiDAR |
| Maida Health | 2.3 TB | Military Police Health Records |
| Intecro | 11.5 GB | Defense/ITAR Robotics Data |
| Iberia | 77 GB | Aircraft Manuals (AMP/ALS) |
| K3G | 192 GB | ISP Network Topology |
| CRRC MA | Complete Server | Mass Transit Schematics & Security |
| Burris Macomber | 18.3 GB | Mercedes-Benz Litigation & Customer PII |
| ThermoEx | 170 GB | Industrial Heat Exchanger Designs |
| CiberC | 103 GB | Government Contract Data |
| GreenBills | 39.5 GB | Patient Health (PHI) |
| Total ETO | 28.95 GB | ERP Source Code & Customer DBs |
| Hydratec | 81 GB | Fire Protection CAD Software |
| Degewo AG | 5.5 GB | Berlin Housing Architectural Plans |
| Voltras | Internal Archive | Financial Data & Airline Invoices |
| IFLUSAC | 22 GB | Engineering Plans & Payroll |
| Aion Law Partners | 38 GB | Legal/Financial/Immigration Docs |
| NMCV Business | 47 GB | Medical Records & PHI |
| PT Pasifik Satelit (PSN) | 92 GB | Satellite/Aerospace Data |
| VYTL-SFT (Verahealth) | 3.65 GB | Clinical Notes & Patient SSNs |
7.2 Additional Confirmed Victims (Sentap Portfolio)
Beyond the detailed case studies above, Zestix (under the alias “Sentap”) has listed data from numerous other organizations. Although Hudson Rock was not able to identify specific credentials to Sharefile, Owncloud and Nextcloud for these victims, it is possible that they still stem from similar Infostealer credentials based on the high amount of victims we did identify to have infostealer credentials to those services, but we do not rule out access via another initial access. The table below summarizes the additional victims identified in this campaign.
| Victim Entity | Sector | Data Volume | Critical Assets Exposed |
|---|---|---|---|
| Navee Teknoloji | Maritime | 195 GB | Vessel details, Satellite comms, Technical blueprints |
| La Esperanza Fuel | Energy/Retail | 5 GB | Government contracts, Financial sales data |
| Esenboğa Airport | Aviation | 75 GB | Expansion blueprints, Security systems, Personnel data |
| Injaro Investments | Investment | 156 GB | Portfolio financials, Loan restructuring, Strategic plans |
| Industrial CMMS | Industrial | Access | Maintenance schedules, Equipment details |
| UrbanX.io | Real Estate | 275 GB | Property listings, Contracts, Employee data |
| Bradley R Tyer | Real Estate | 1.02 TB | Title search reports, Deeds, Tax data (1990-2025) |
| Lex Logos Romania | Legal | 68 GB | Passports, Medical diplomas, Criminal records |
| Australian NBN | Telecom | 306 GB | Network maps, Cable routes, Infrastructure defects |
| Hutchinson Builders | Construction | 71 GB | Blueprints, Geotechnical reports, Safety plans |
| imss-consultores | Mining | 105 GB | Mineral block models, Drill hole data, Feasibility studies |
| GTD System | Defense | 2.71 GB | Military optoelectronics, Combat management systems |
| Clevertech S.p.A. | Automation | 17.8 GB | PLC diagrams, Industrial schematics, HMI software |
| New Glasgow/Canuck | Real Estate | 3 GB | Rent rolls, Lease agreements, Financial analysis |
| PetroAndina S.R.L. | Oil & Gas | 136 GB | Fuel distribution logistics, YPF contracts |
| Kimia Farma | Pharma | 40 GB | Pharmaceutical inventory, Sales transactions |
| Telecall Brazil | Telecom | 70 GB | Call Detail Records (CDR), Network configs, SIP data |
| GreenHills Ventures | VC | 34 GB | Term sheets, Cap tables, Due diligence reports |
| Pan-Pacific Mechanical | Engineering | 1.04 TB | HVAC/Plumbing drawings, Hospital infrastructure plans |
| Cloisall / WSP | Construction | 24 GB | Luxury project Revit models, Shop drawings |
| Schrödinger GmbH | Biotech | 9 GB | Financial invoices, Scientific collaboration docs |
| The Providence Group | Real Estate | 1 TB | Architectural plans, CAD files, Purchase contracts |
| THESAVVYACCOUNTANT | Financial | 2.1 GB | Client ledgers, Tax returns, Bank statements |
| Albany Physical Therapy | Medical | 1 GB | Patient records, Insurance payments, MRI scans |
| EXPRO-YPF | Oil & Gas | 1.5 GB | Well integrity logs, Vaca Muerta field data |
| Treasure Coast Cardiology | Medical | 3.5 GB | EKG reports, Patient PHI, Medicare claims |
| Lebanese ISP | Telecom | Access | Radius admin access, User traffic monitoring |
| Bluefire/Old American | Insurance | 10 GB | Policy cancellations, Renewals, Customer debts |
| Saudi Arabia Customs | Govt/Trade | 42 GB | Import/Export records, Commercial invoices |
| Erga Group | Architecture | 5 GB | Royal villa plans, Structural analyses, MEP systems |
8. Beyond Zestix: A Global Epidemic of Cloud Exposure
While Zestix is a prominent actor capitalizing on this specific vector, the scope of the problem is far larger. Hudson Rock’s threat intelligence platform, Cavalier, has identified thousands of organizations using ShareFile, OwnCloud, and Nextcloud that currently have compromised credentials circulating in Infostealer logs.
This exposure affects some of the world’s largest and most security-conscious entities, including Deloitte, KPMG, Samsung, Honeywell, Walmart, the CDC, and many others. These organizations have employees or partners who have been infected, leaving valid sessions or credentials to sensitive file repositories exposed to actors like Zestix.
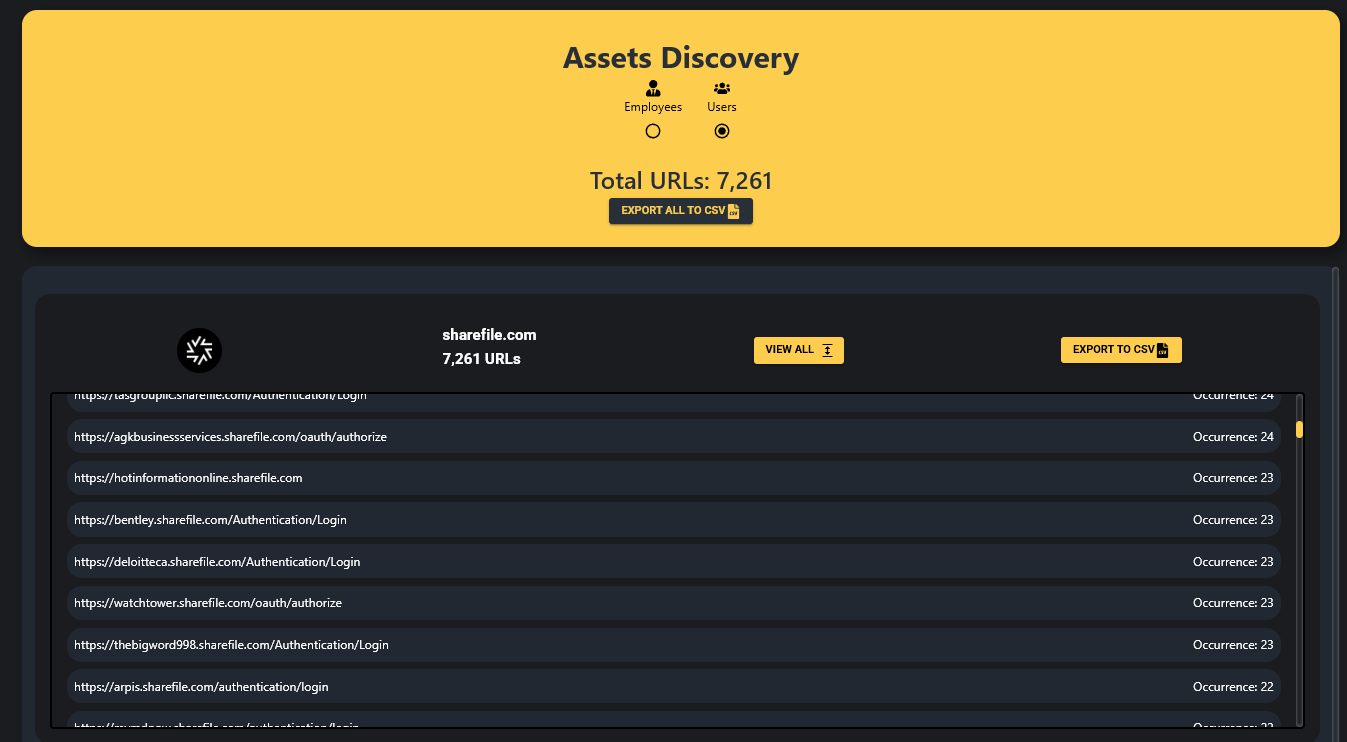
Take Action: Check Your Exposure
Companies can immediately check if their domains are affected by Infostealer infections using our free cybercrime intelligence tools. We also encourage security teams to contact us for an ethical disclosure to verify if they have exposed credentials to ShareFile, Nextcloud, or other critical services due to infected employees or third-party partners.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us here: https://www.hudsonrock.com/schedule-demo
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
Learn more about us: https://en.wikipedia.org/wiki/Hudson_Rock