Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack
February 2026 – The Romanian national oil pipeline operator, Conpet, recently confirmed a major cyberattack. The notorious Qilin ransomware group has claimed responsibility, alleging they have stolen nearly 1TB of sensitive data, including financial records and internal documents.
While the company and authorities investigate, Hudson Rock has identified the likely “Patient Zero.” Our analysis reveals that the breach almost certainly originated from a single Infostealer infection on a computer belonging to a Conpet IT employee.
Key Findings:
- Infection Date: January 11, 2026 (Weeks before the ransomware deployment).
- Detection Date: January 12, 2026 (Identified by Hudson Rock one day later).
- Source: A personal/side-business computer used by a Conpet IT administrator.
- Impact: The infection leaked critical credentials for VPNs, Network Monitoring (Cacti), and Update Services (WSUS), handing Qilin the keys to the entire network.
The “Smoking Gun”: A Jan 11th Infection
Through Hudson Rock’s Cavalier platform, we identified a computer infected with an Infostealer malware on January 11, 2026. Crucially, this data was intercepted and indexed by Hudson Rock on January 12, providing early visibility into the threat.
The infected machine, named DESKTOP-TCR5GQM, was logged in under the user GadgetFix. At first glance, this appears to be a personal computer, likely used for a side business involving electronics repair (based on the “GadgetFix” name and associated gadgetfix.ro credentials found in the logs).
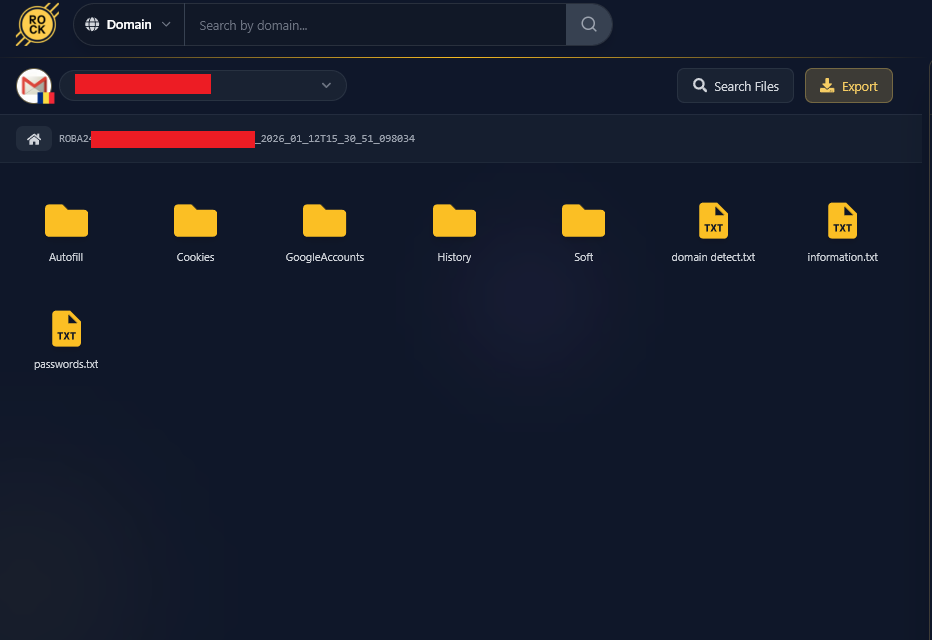
Figure 1: The raw files retrieved from the infostealer infection.
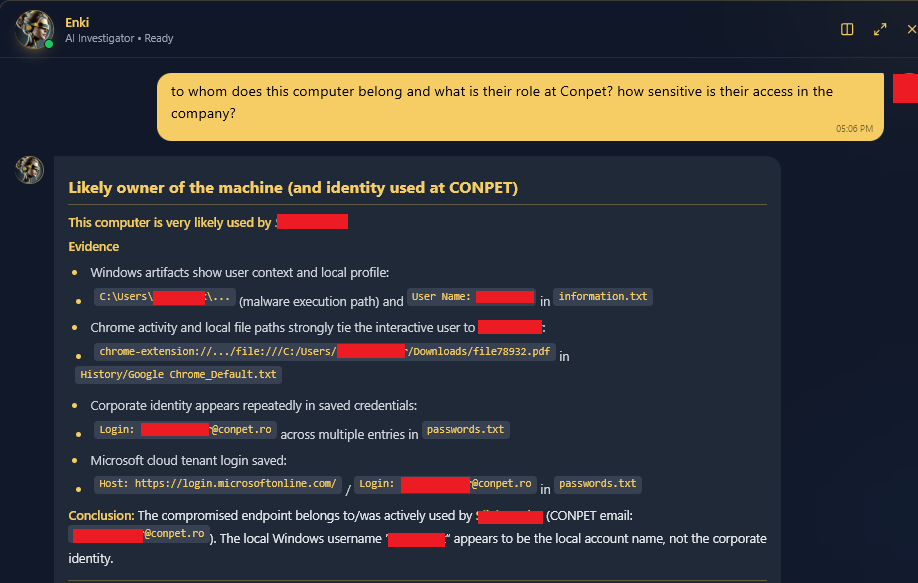
Figure 2: Hudson Rock’s Infostealer Intelligence identifying the Conpet employee behind the infected machine.
However, a deeper look at the 268 credentials exfiltrated from this single machine reveals its true significance. The user, identified as ******.****** (an IT employee at Conpet), was using this same machine to log into critical Conpet infrastructure.
The Attack Path: From Infostealer to Ransomware
Ransomware groups like Qilin rarely “break in” using sophisticated zero-day exploits anymore; they simply log in. The logs from this infection provided a perfect roadmap for a full-scale domain takeover.
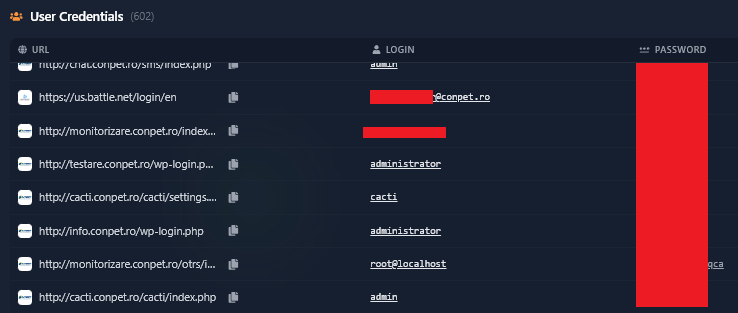
Figure 3: Overview of the critical Conpet credentials identified by Hudson Rock (Part 1).
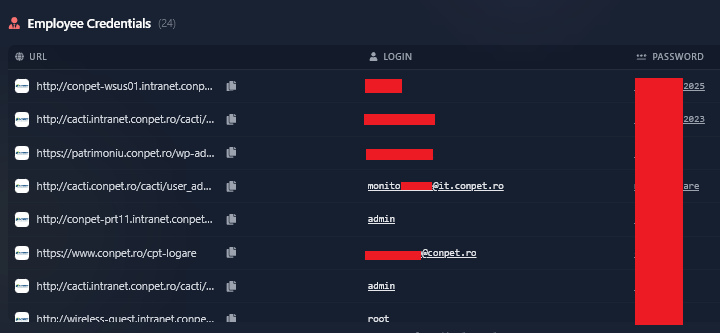
Figure 4: Overview of the critical Conpet credentials identified by Hudson Rock (Part 2).
Note: While we cannot forensically confirm the exact commands executed by the attackers, the presence of these specific credentials creates a highly probable “kill chain.” The following visualization demonstrates how an attacker could leverage these stolen logins to move from initial entry to total network compromise.
1. Initial Access
User: ******.******@conpet.ro
2. Reconnaissance
User: monitorizare@it…
3. Lateral Movement
User: ****** / R******
The most critical find in the logs was access to the WSUS (Windows Server Update Services) server. In a Windows environment, the WSUS server is trusted by all other computers to provide system updates. If an attacker controls WSUS, they can push a “fake update” – which is actually the Qilin ransomware payload – to every server and workstation in the company simultaneously.
| Critical System | URL / Host | Login Found |
|---|---|---|
| Update Server (WSUS) | conpet-wsus01.intranet.conpet.ro |
****** / R****** |
| Infrastructure/DB | wireless-guest.intranet.conpet.ro |
root / r****** |
| Asset Management | patrimoniu.conpet.ro |
******.****** |
| Printer Admin | conpet-prt11...:8080 |
admin |
Figure 5: The Qilin ransomware group listing Conpet on their dark web leak site.
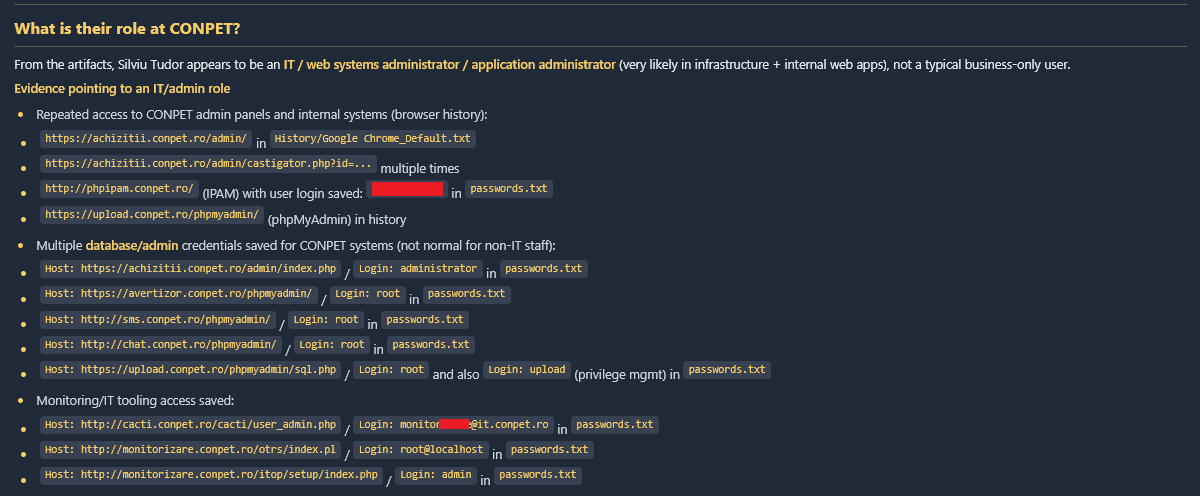
Figure 6: Mapping the specific sensitive accesses revealed in the infection logs.
The Human Element
This breach highlights a critical failure in “Shadow IT” and device policy. The machine DESKTOP-TCR5GQM was clearly used for personal projects – the logs show administrative access to side businesses like gadgetfix.ro and compascoffee.ro.
By logging into highly sensitive work accounts (like the Conpet WSUS server) from an unsecured personal device used for downloading random software, the employee inadvertently bridged the air gap between the criminal underground and Romania’s critical energy infrastructure.
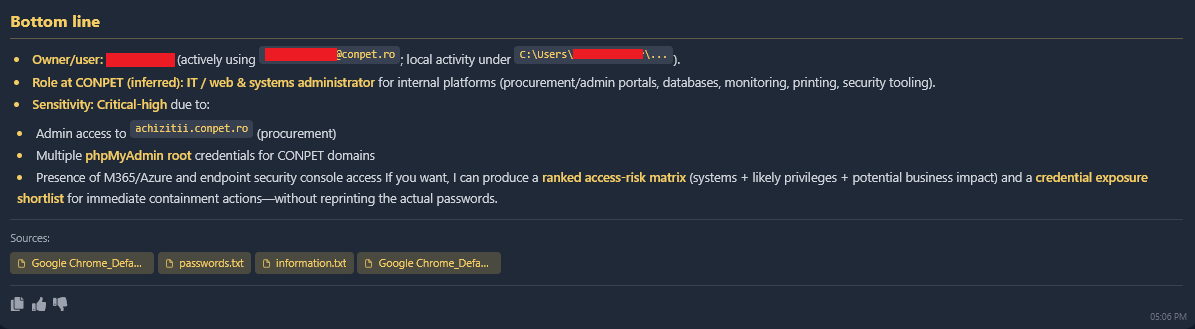
Figure 7: AI Analysis confirming the severity of the identified breach vector.
Conclusion
The Conpet breach serves as a stark reminder: Infostealers are the precursor to Ransomware.
The gap between the initial infection (Jan 11) and the public disclosure of the ransomware attack (Feb 6) suggests that Qilin had weeks to explore the network using these stolen credentials. Organizations must monitor for compromised credentials of their employees before they are used to deploy ransomware.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock