Executive Summary
Hudson Rock researchers have recovered a full set of original internal documents from the Al-Aqsa Martyrs’ Brigades, exfiltrated from a compromised machine in the Gaza Strip. Infected in January 2023, the machine contained sensitive files from the organization’s “Military Media and Moral Formation Department,” offering a rare look into advance operational planning, internal disciplinary fractures, and tactical media coordination during the August 2022 “Breaking Dawn” operation.
Operational Planning: Pre-authorized Intent
Among the exfiltrated data was a document predefining escalation triggers. It explicitly states that there is no scenario for restraint in the event of conflict, declaring: “We are obligated to respond, even if we are alone, regardless of the cost.”
This finding is significant because it represents pre-authorized operational intent rather than reactive propaganda. It proves that the organization’s military actions are governed by rigid, predetermined triggers that prioritize escalation over diplomacy.
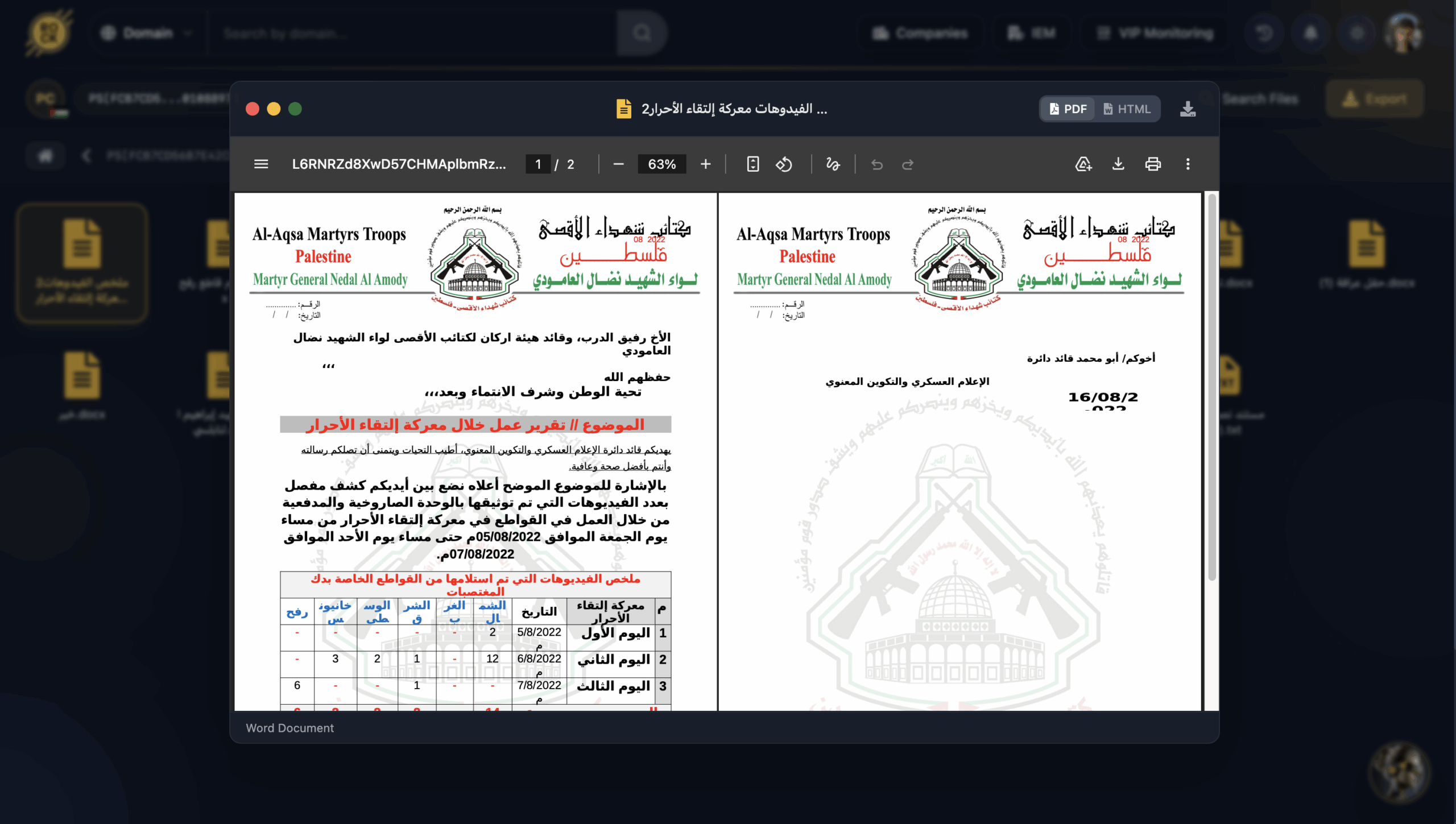
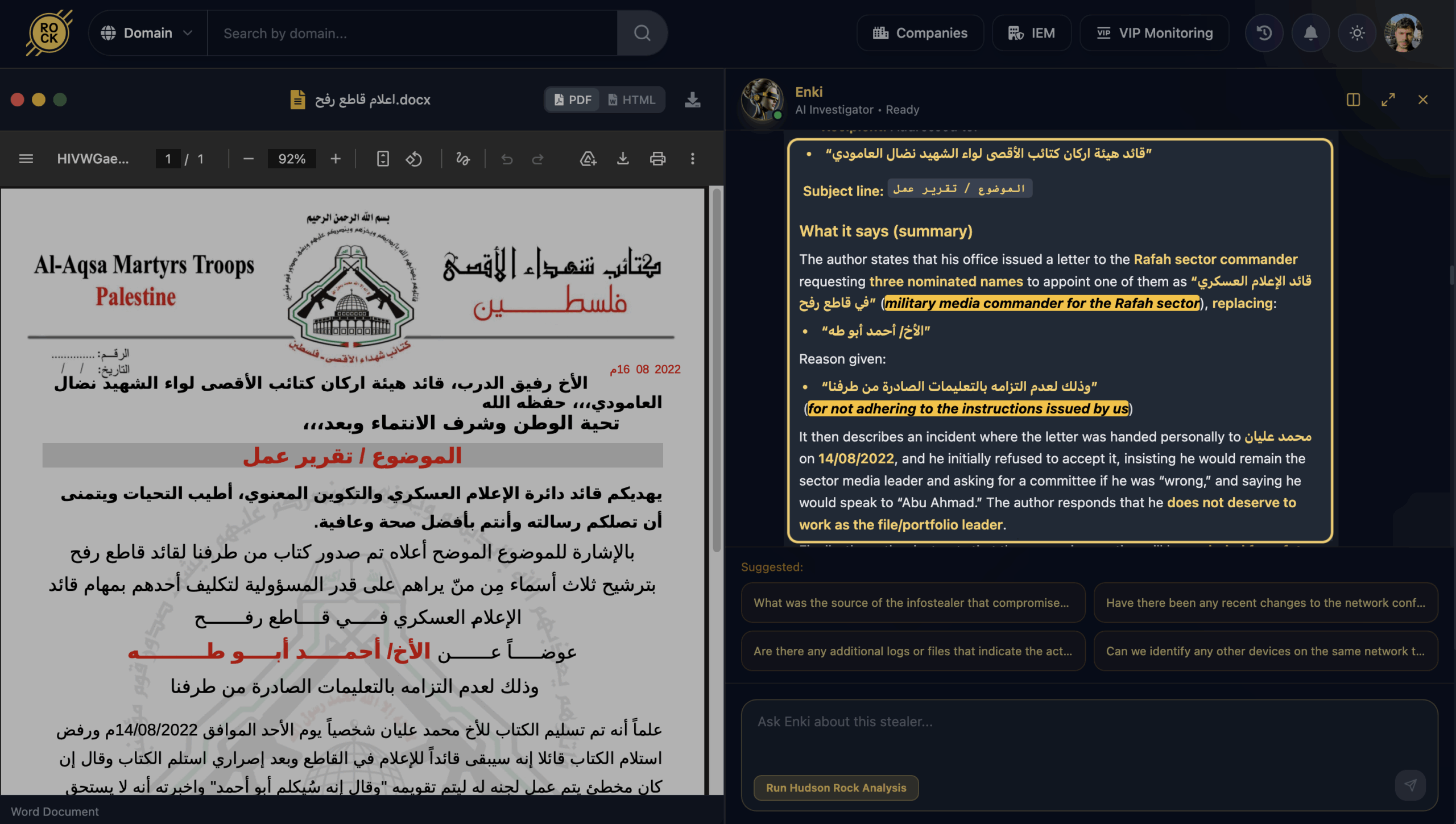
Internal Power Struggles: The Rafah Declaration
Beyond military tactics, the infostealer logs revealed the internal friction often hidden from public view. One document, titled the “Rafah Declaration,” records the removal of a Rafah-sector media commander for disobeying orders.
The file provides specific names, dates, and descriptions of the commander’s refusal to comply with leadership mandates. This offers investigators a rare look into the internal discipline, chain-of-command fractures, and administrative instability within the organization.
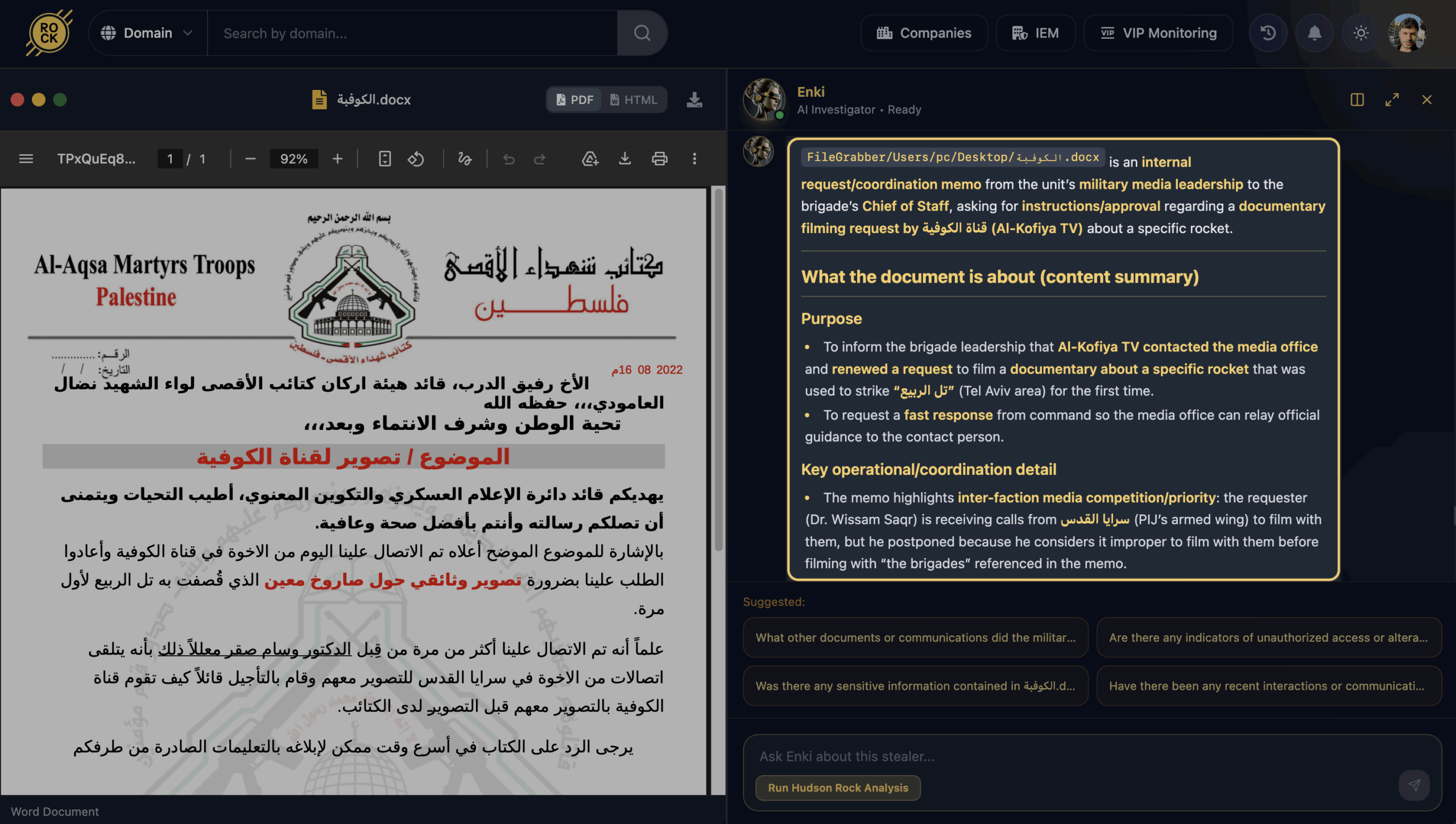
Media Coordination & Rocket Attacks
The investigation also uncovered memos detailing the strategic delay of information to preserve media priority. One specific memo discusses coordination with Al-Kofiya TV to film a documentary about a rocket used to strike the Tel Aviv area.
Crucially, the memo instructs handlers to deliberately delay cooperation with other armed factions. This suggests that “Military Media” is not just about reporting; it is a competitive arena where factions vie for media dominance and public credit for attacks.
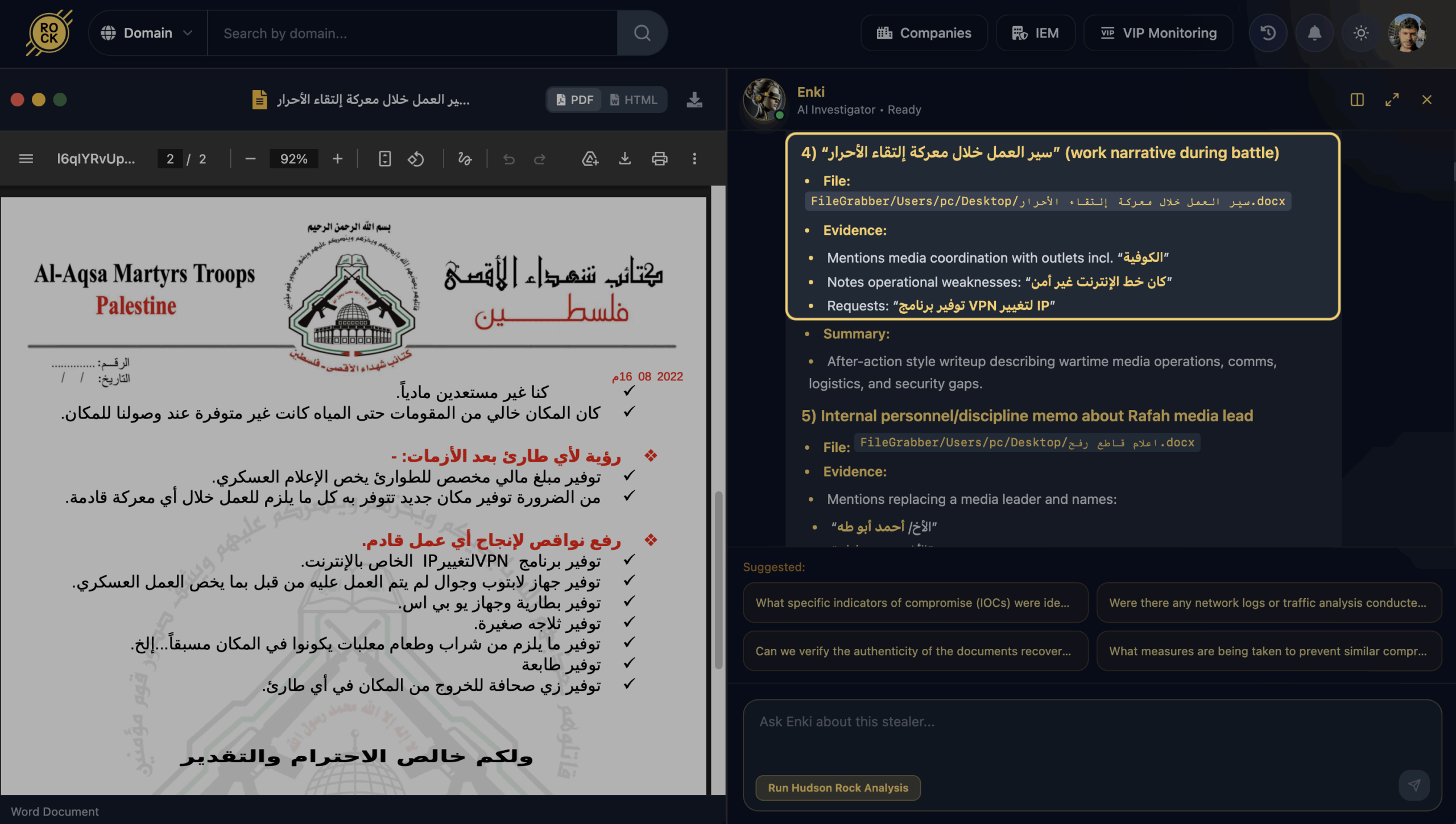
Explicit OPSEC Awareness & Requirements
Perhaps most telling for counter-terrorism investigators is the organization’s own assessment of its digital vulnerabilities. The exfiltrated files openly mention the risks of “insecure internet lines.”
The documents include explicit requests for VPNs, “clean” laptops, and unused burner phones specifically for “military media” work. This high level of OPSEC awareness indicates that the organization is actively attempting to harden its digital infrastructure against surveillance, even as their own personnel remain vulnerable to infostealer malware.
Conclusion
These documents, signed by “Abu Muhammad” (the official spokesman), provide an unprecedented view into the internal communications and advance operational planning of a terrorist organization.
By analyzing infostealer-exfiltrated data, Hudson Rock continues to demonstrate that the true value of cyber intelligence lies in these deep, structural insights. We move beyond simple credential recovery to provide investigators with the actual blueprints of organizational behavior and intent.
To learn more about Hudson Rock’s intelligence capabilities, visit hudsonrock.com.