Executive Summary
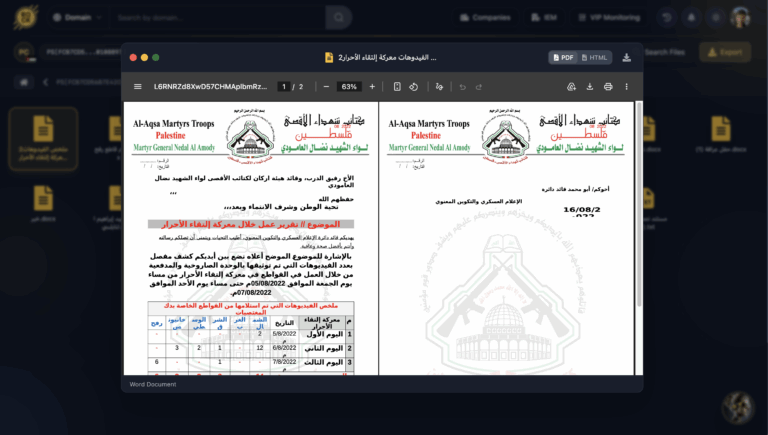
Analysis of a compromised machine in Deir al-Balah (Gaza Strip) has revealed a focused collection of documents attributed to Hamas’ Al-Qassam Brigades. The exfiltrated data reflects a structured relationship with the organization’s media and mobilization ecosystem, detailing how religious sermons, cultural competitions, and social media activists are weaponized to align public sentiment with militant objectives.
The Digital Context: Active Browser Sessions
The investigation pivoted from a standard infostealer log to high-fidelity intelligence after identifying active browser sessions and cookies for alqassam.ps (the official Al-Qassam Brigades website) and saraya.ps. These artifacts indicate direct access to Hamas-affiliated media platforms, which can belong to a range of users – from individuals with ideological or informational interest, to media operators, supporters, or affiliated digital assets – and therefore require careful contextual analysis rather than automatic attribution.
Religious Framing: Preachers of the Sword
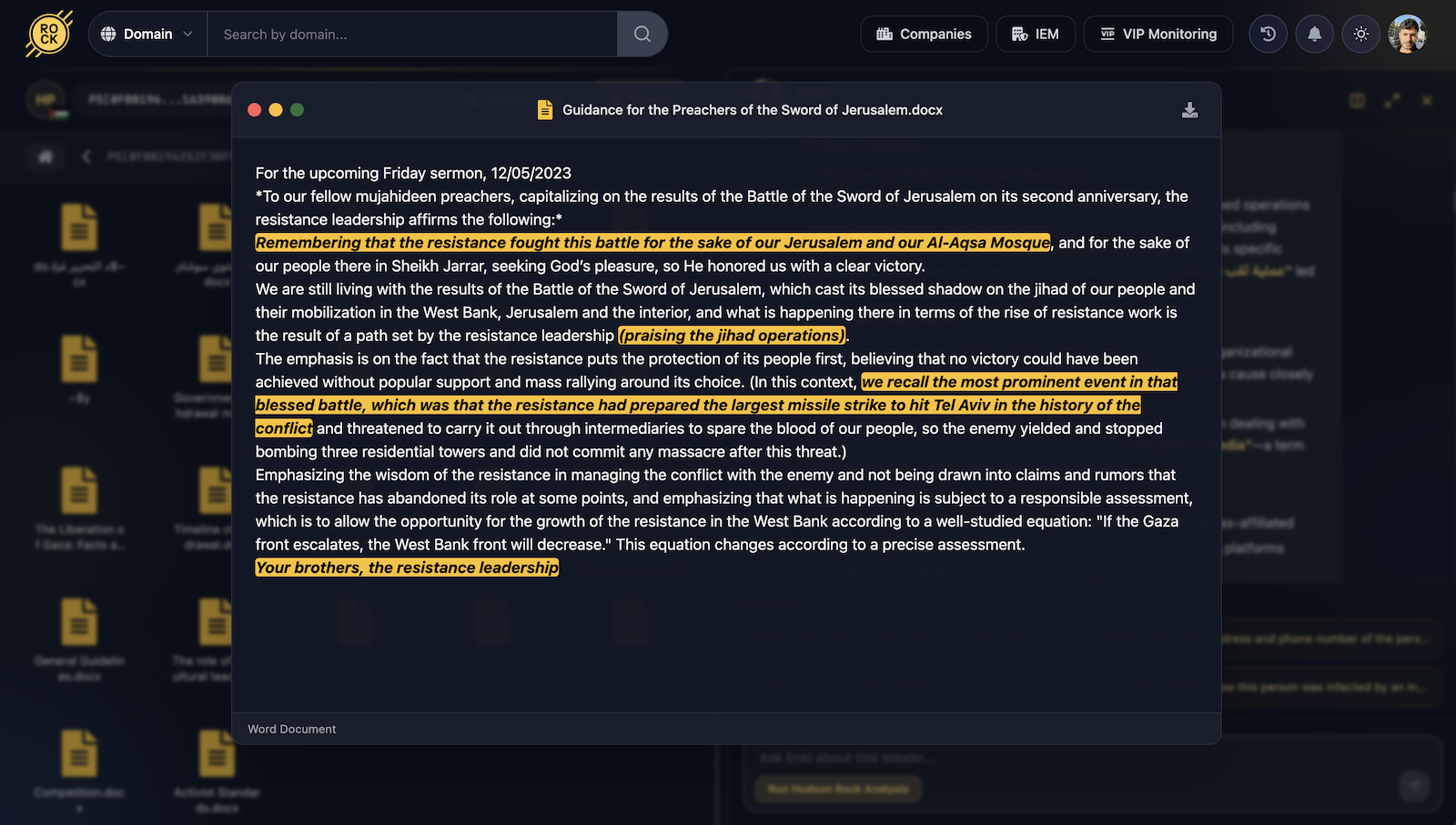
Among the most critical findings was a document titled “Guidance for the Preachers of the Sword of Jerusalem” (إرشادات لوعاظ سيف القدس). Signed by “Your brothers, the resistance leadership” – the file provides specific sermon guidance framing the 2021 Israel-Gaza conflict as a holy religious struggle for Jerusalem and Al-Aqsa.
The document serves as a psychological operations (PSYOP) manual, instructing preachers to emphasize mass support for jihad operations and referencing a planned large-scale missile strike on Tel Aviv to maintain domestic morale and pressure.
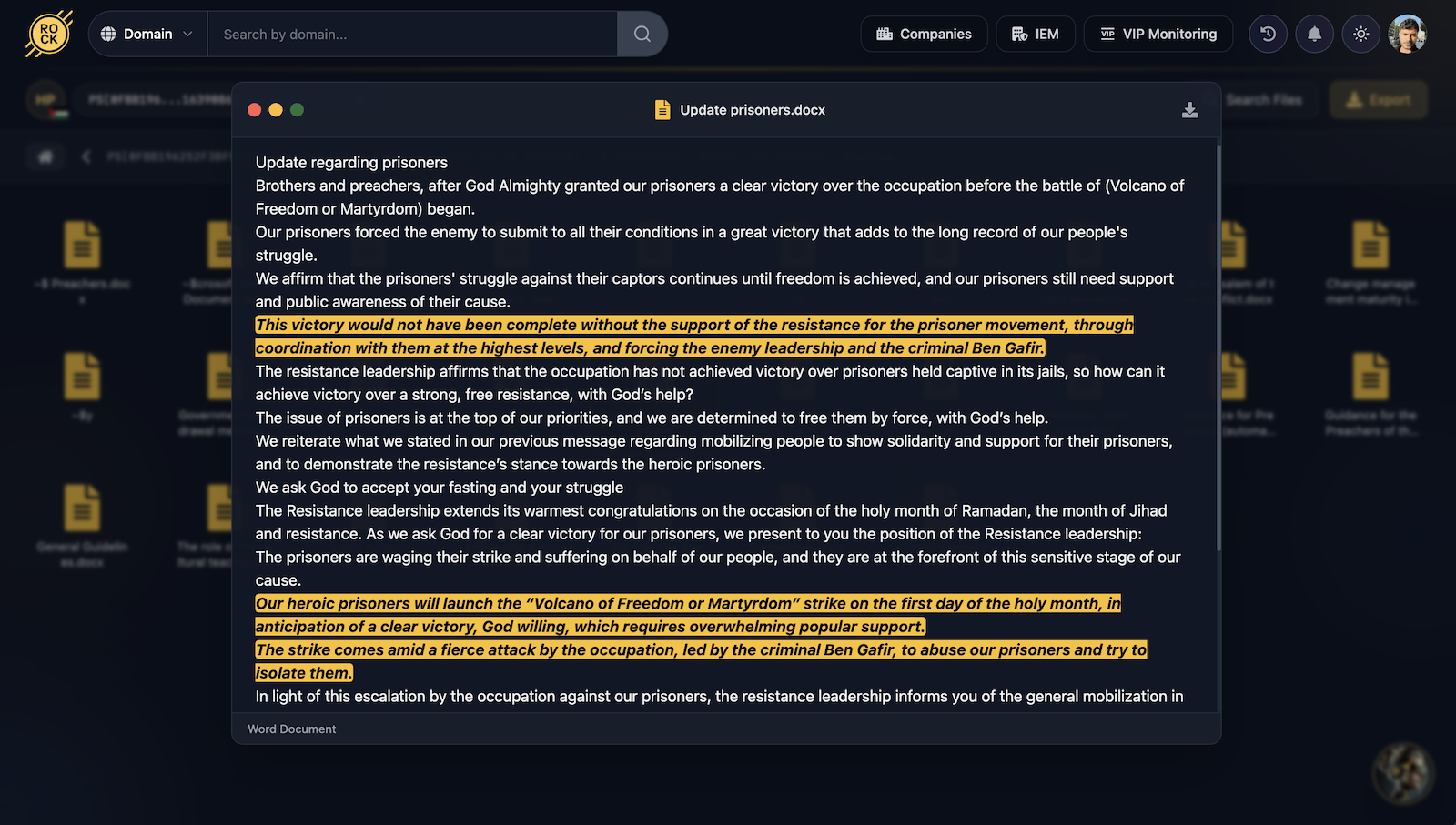
Operational Escalation: Prisoner Updates
We also identified a “Prisoner Update” (تحديث اسرى) file that reveals the coordinated lead-up to the “Volcano of Freedom or Martyrdom” – a massive hunger strike launched in March 2023. This file is not merely a record; it is an instruction set for communicators to synchronize messaging with resistance objectives, using the plight of prisoners to spark civilian escalation.
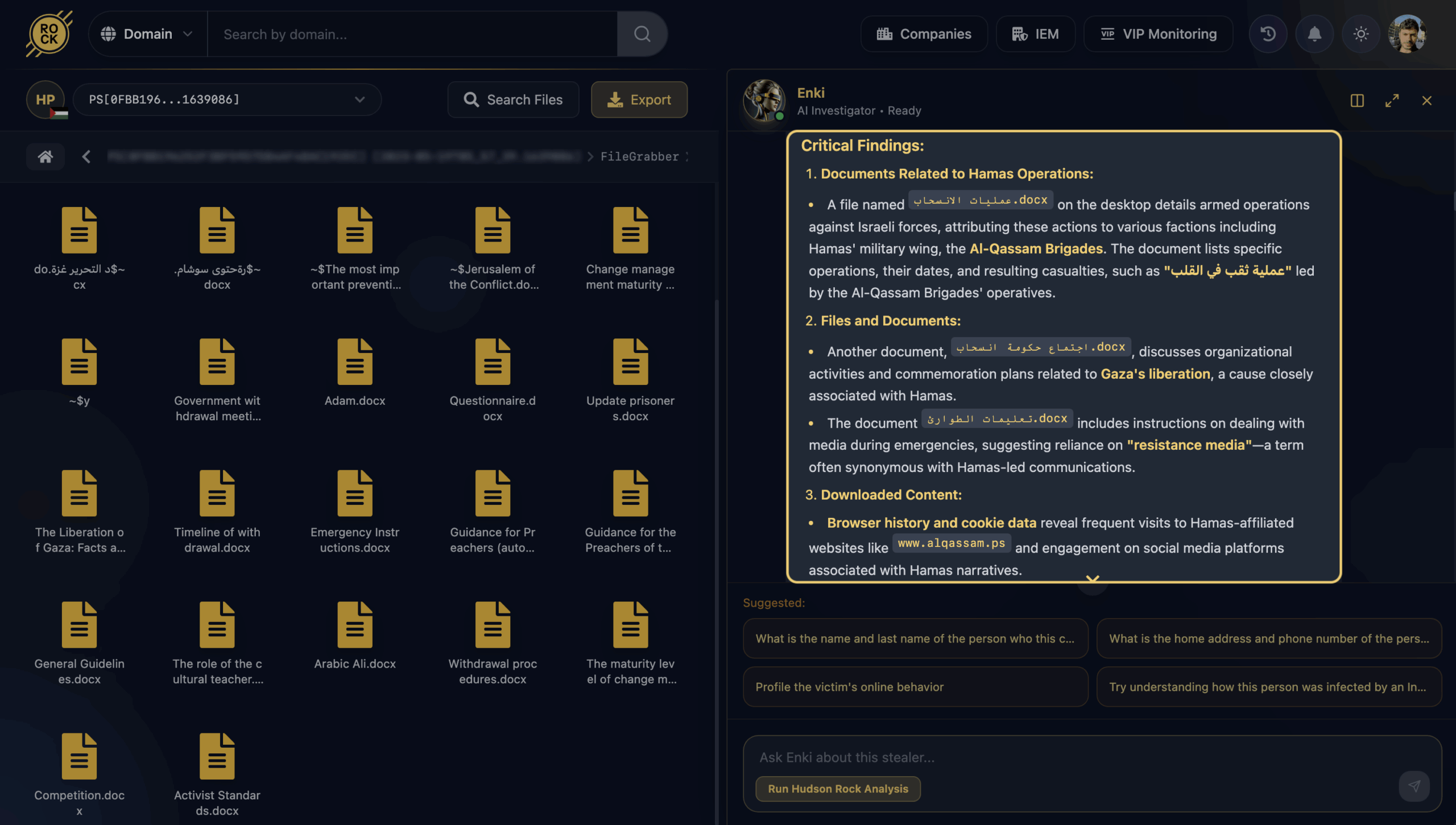
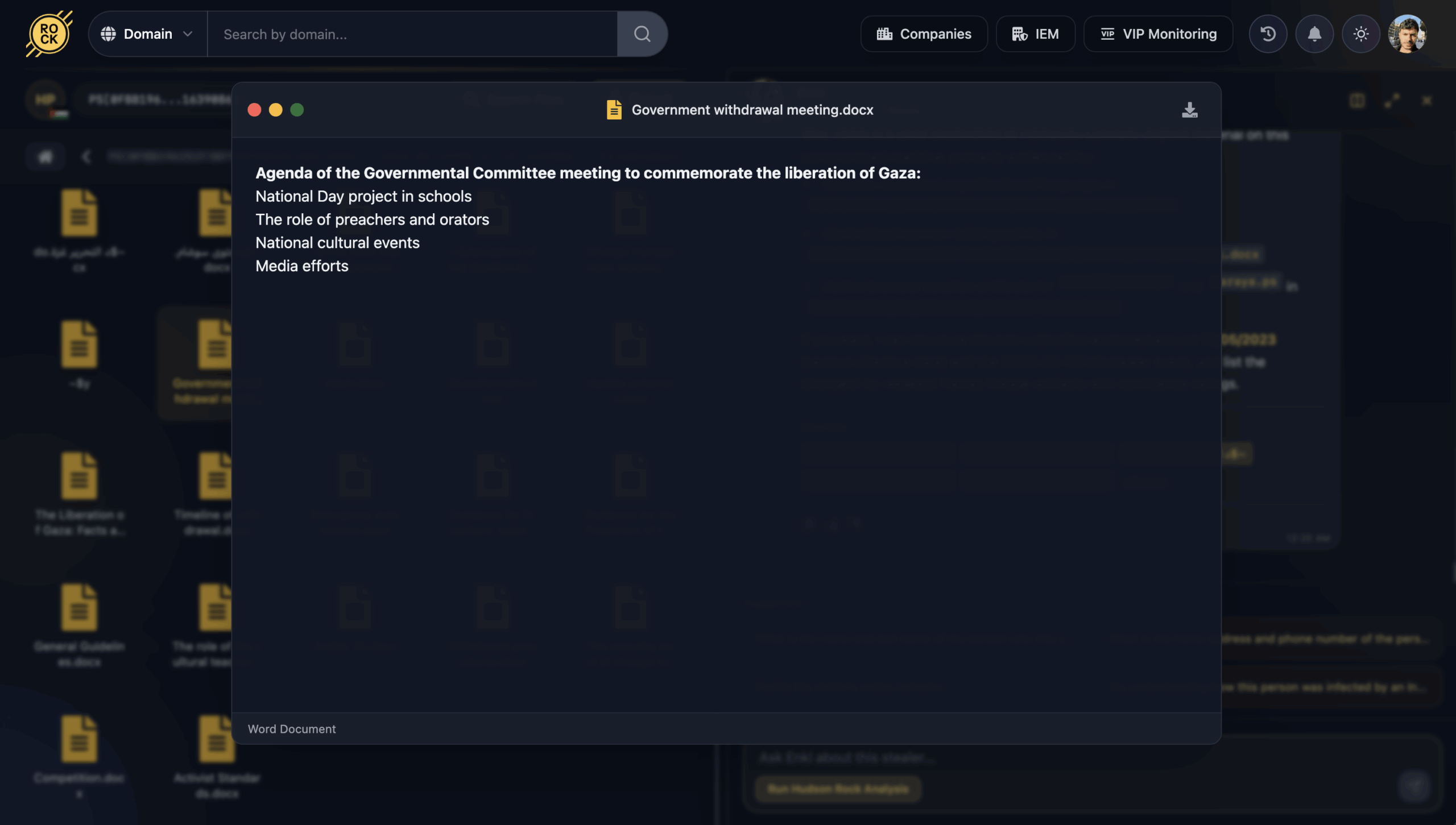
Cultural Mobilization & Activist Standards
The exfiltrated data highlights how Hamas treats education, religion, culture, and media as a single, interconnected toolset. Two documents in particular showcase this “soft power” weaponization:
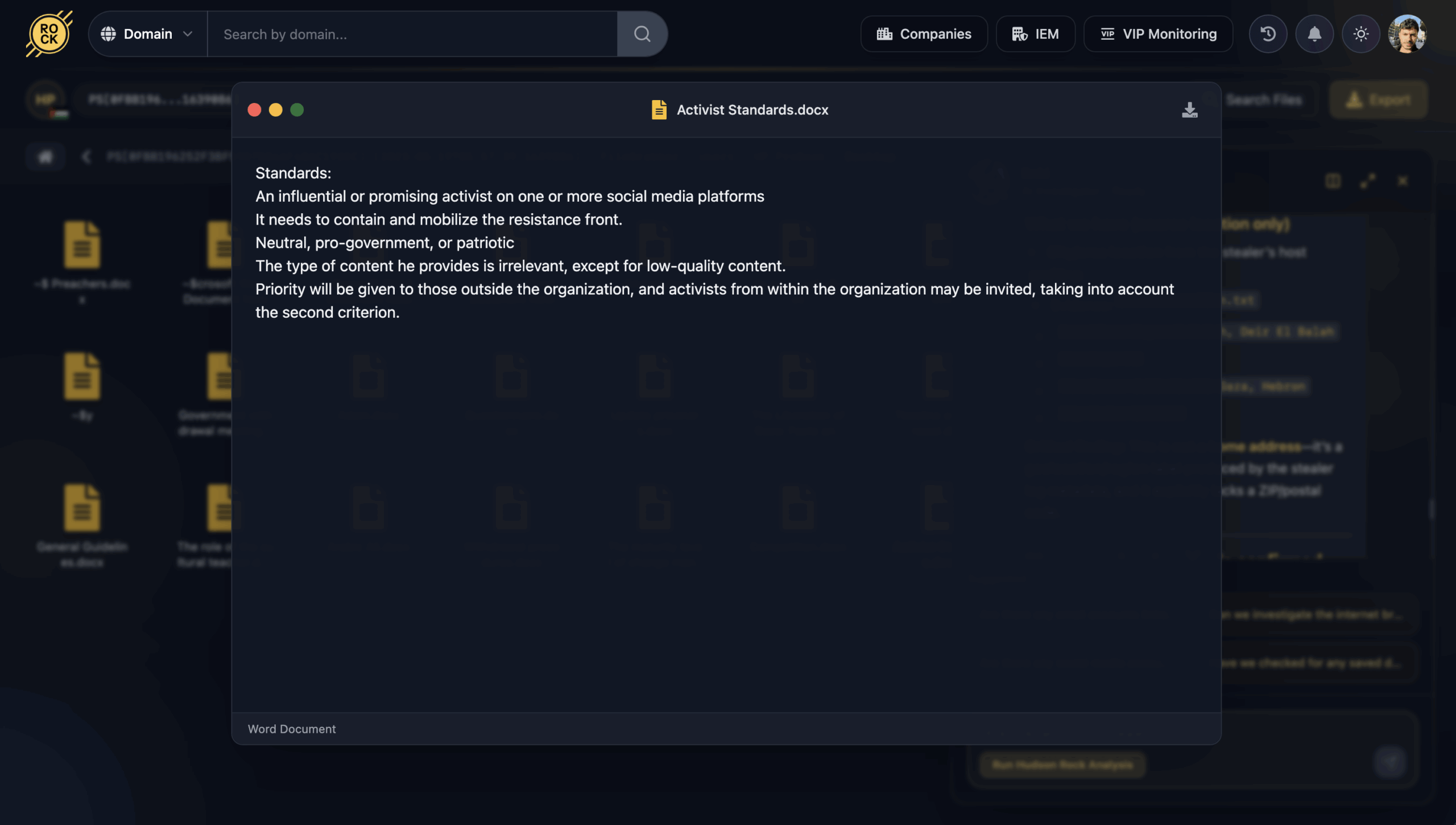
1. Activist Standards (معايير نشطاء): This file details Hamas’ strategy for social media influencers. They deliberately prioritize “semi-independent” voices to expand their reach while minimizing visible organizational attribution, creating an illusion of organic grassroots support.
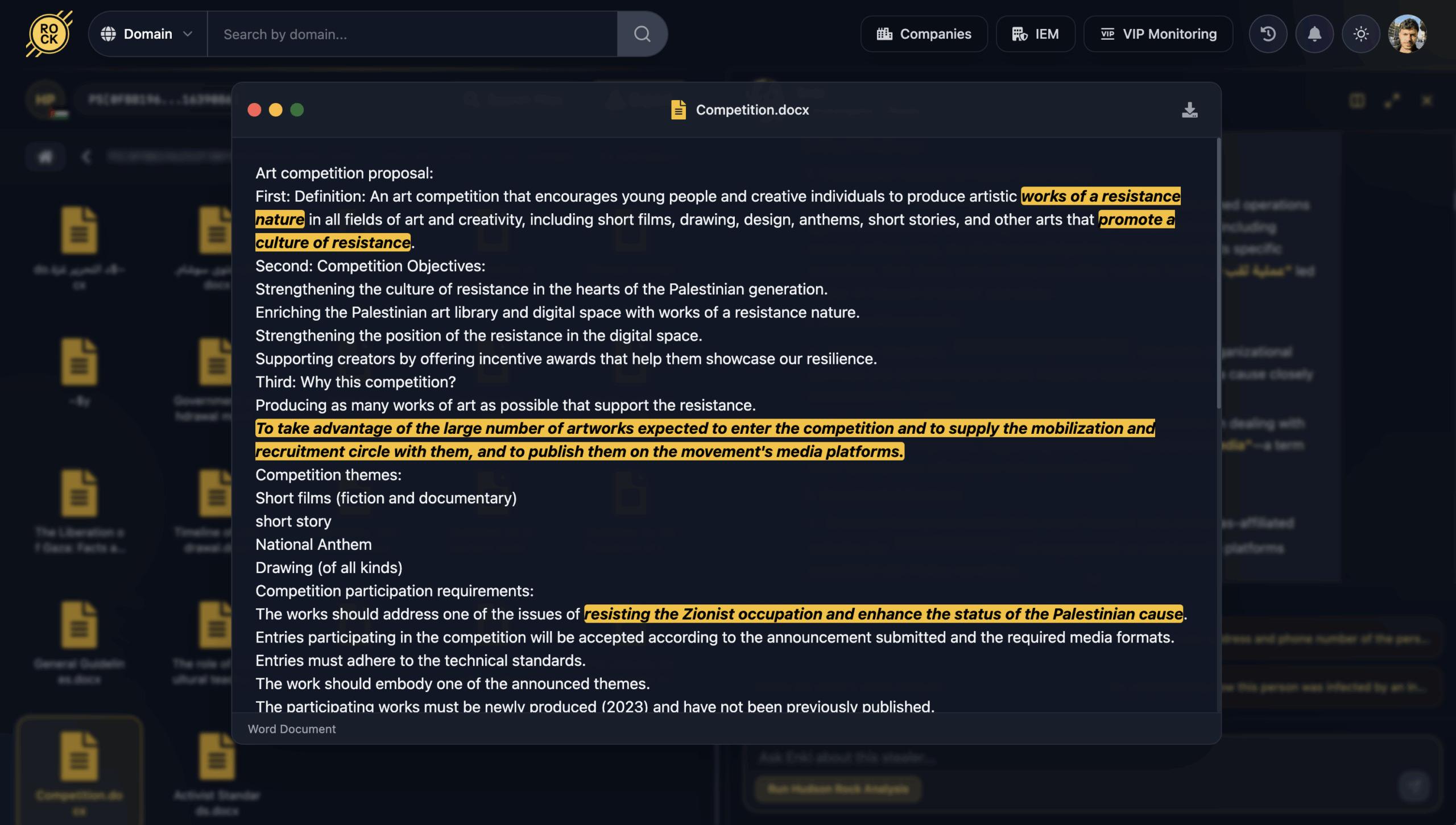
2. Art Competition Proposal: A proposal encouraging young creators to produce films, anthems, and short stories that “promote a culture of resistance.” This underscores how the organization builds a mobilization pipeline by targeting the creative output of the youth.
Conclusion
Infostealers are more than just a source of passwords; they offer a rare window into the operational heartbeat of terror organizations. This investigation shows how the “media and mobilization ecosystem” of the Al-Qassam Brigades functions in real time.
For law enforcement and counter-terror investigators, infostealer-sourced data can provide critical early signals: what platforms are accessed, what material is stored, and how individuals interact with extremist content online. By using Hudson Rock’s intelligence platforms, investigators can move beyond isolated indicators and build real operational context – turning fragmented technical artifacts into actionable counter-terrorism intelligence.
To learn more about how Hudson Rock supports investigations and intelligence work, visit hudsonrock.com.