*Interactive simulator can be accessed via desktop – www.hudsonrock.com/northkorean
In the world of Threat Intelligence, we are usually looking at the aftermath of an attack: the encrypted servers, the stolen databases, or the fraudulent transactions. Rarely do we get a look through the eyes of the attacker.
But even state-sponsored hackers make mistakes. And sometimes, they get infected by the very same commodity malware they deploy against others.
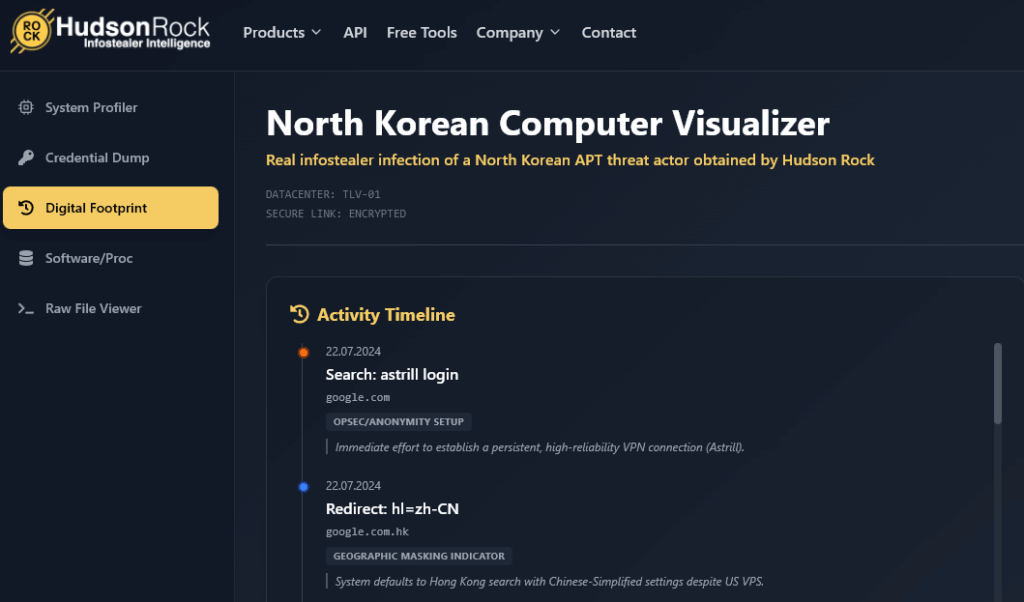
Recently, Hudson Rock analyzed a unique infection from a LummaC2 infostealer log. The victim wasn’t a corporate employee or an unsuspecting consumer. The victim was a high-level North Korean threat actor operating a sophisticated malware development rig.
Thanks to cross-referencing our data with a recent Silent Push research, we can confirm this machine is directly linked to the broader North Korean threat ecosystem and infrastructure associated with the historic $1.4 Billion ByBit Heist.
The Smoking Gun: trevorgreer9312
Embedded deep within the stolen credentials of this infected machine was a specific email address: [email protected].
According to new research from Silent Push, this exact email address was used to register the domain bybit-assessment[.]com just hours before the massive theft of crypto assets from ByBit.
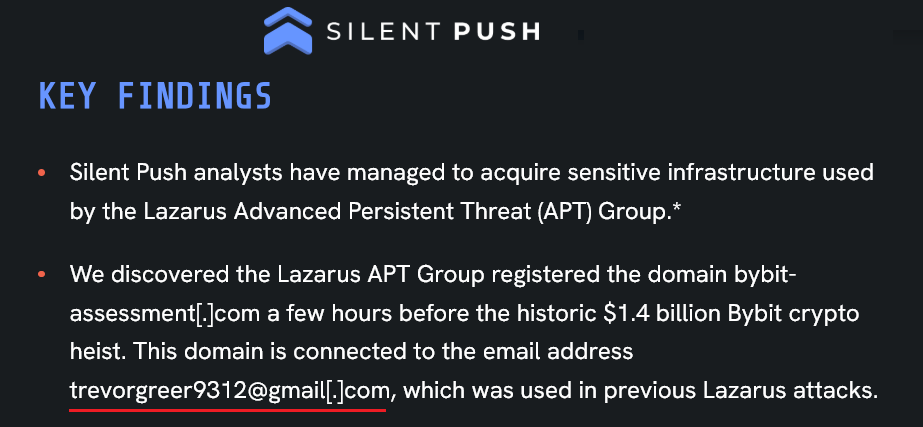
While our analysis suggests the operator of this machine is likely part of a separate subgroup within the DPRK cyber-offensive apparatus, the use of identical credentials connects this developer rig directly to the infrastructure used in one of the largest financial cyber-attacks in history. This highlights the resource sharing common among state-sponsored actors, where developers, infrastructure managers, and heist operators often rely on the same pools of digital assets.
What the Data Reveals
To help the research community visualize this rare find, we have constructed an interactive forensic dashboard that recreates the state of this compromised machine. The visualization allows you to explore the same artifacts our analysts discovered:
- The Infrastructure Link: You can personally verify the presence of the
trevorgreer9312credential in the simulated data, the thread that connects this machine to the broader Lazarus ecosystem. - The MalDev Pipeline: The machine was loaded with commercial-grade tools like Visual Studio Professional 2019 and The Enigma Protector v7.40. The presence of Enigma Protector is particularly damning, as it is a professional tool used to pack executables and evade antivirus detection.
- The Attribution Paradox: The actor utilized Astrill VPN to route traffic through a US IP address (104.223.97.2). However, the browser data betrayed them: specific settings were forced to Chinese-Simplified, while translation history showed direct queries converting text into Korean.
- Financial Motives: Consistent with known DPRK objectives, the logs reveal an obsession with cryptocurrency. From setting up MetaMask wallets to troubleshooting blocked funds on BitPay, the operator was actively building the infrastructure that facilitates illicit financial operations.
- The use of Dropbox for file uploads/storage (
upload_vpsapp folder, multiple IP sub-folders) strongly suggests it was used for data exfiltration (uploading stolen wallet files) and potentially as a C2 channel. Use of Slack and Telegram is consistent with APT activity for communications and C2 infrastructure. - The purchase of domains like
callapp.usandcallservice.uson Namecheap and subsequent setup of subdomains likezoom.callapp.usandzoom.callservice.uspoint to the creation of phishing/spoofed websites to host their malware and trick users into downloading what they believe is a legitimate Zoom installer or link. The local host IP forzoom.callapp.usfurther ties to this spoofing effort.
Explore the Simulation
Understanding the mindset and environment of an APT actor is crucial for defense. We have made this data available through an interactive simulator that lets you “boot up” the compromised machine and inspect the artifacts yourself, from the software list to the browser history & credentials that exposed their operation.