Hackers Steal Text and Call Records of ‘Nearly All’ AT&T Customers

In one of the most significant data breaches in recent history, hackers stole AT&T customers’ call and text metadata spanning several months. Hackers broke into a cloud platform used by AT&T and downloaded call and text records of “nearly all” of AT&T’s cellular customers across a several month period, AT&T announced early on Friday. The […]
Re-Infected: The Persistent Threat of Infostealers
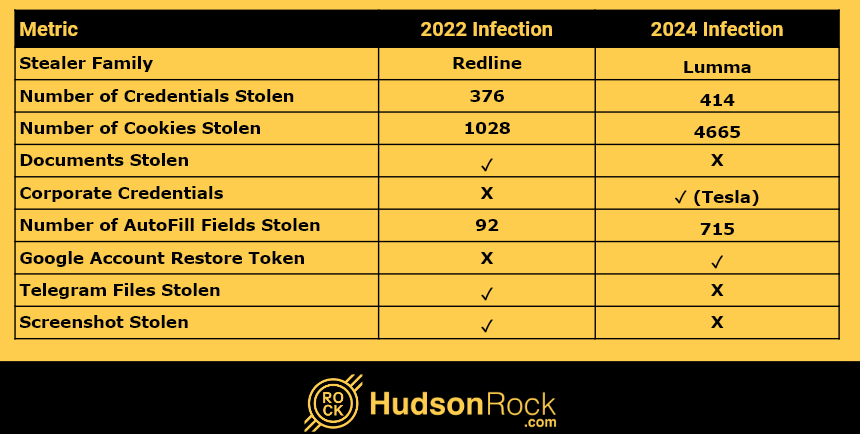
Having your data stolen once is bad enough, but for some people, it happens repeatedly. Infostealer infections are not a new phenomenon in the cybersecurity world, in fact, Hudson Rock has been collecting threat intelligence data from computers infected by Infostealers going back to 2018. With almost 30,000,000 computers infected in total by July 2024, it comes […]
Supply Chain Compromise Leads to Trojanized Installers for Notezilla, RecentX, Copywhiz

Executive Summary On Tuesday, June 18th, 2024, Rapid7 initiated an investigation into suspicious activity in a customer environment. Our investigation identified that the suspicious behavior was emanating from the installation of Notezilla, a program that allows for the creation of sticky notes on a Windows desktop. Installers for Notezilla, along with tools called RecentX and […]
Open-Sourced Infostealers About to Fuel New Wave of Computer Infections

A potential shift in Infostealers might be happening again. Traditionally, teams of cybercriminals develop an Infostealer family (variant) such as Redline, Lumma, Raccoon, etc., and rent the capabilities of that variant to other cybercriminals, typically costing a few hundred dollars per month. However, a new trend is emerging that could significantly alter the landscape of […]
ID Verification Service for X & TikTok Breached due to an Infostealer Infection
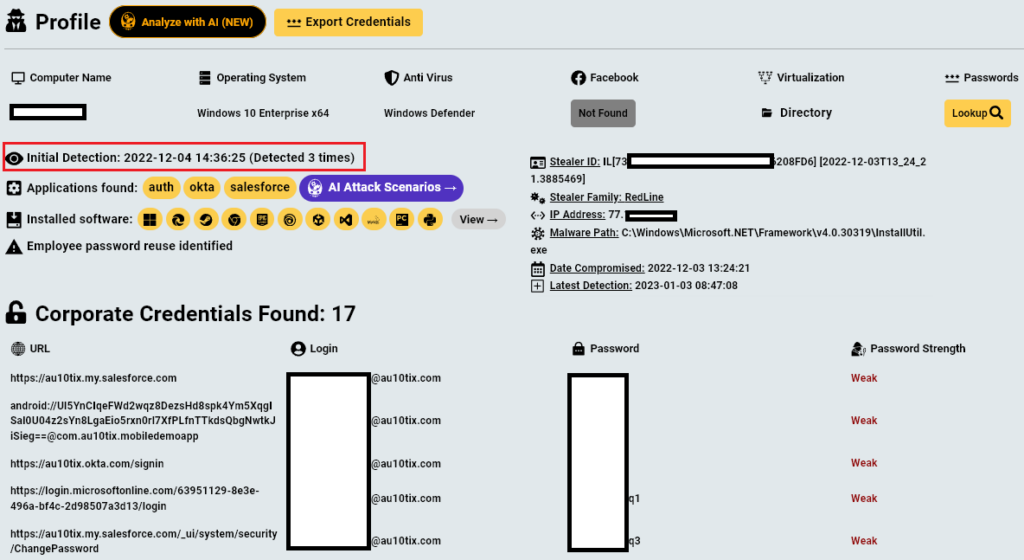
AU10TIX, a company that verifies the identities of TikTok, Uber, and X users, sometimes by processing photographs of their faces and pictures of their drivers’ licenses, exposed a set of administrative credentials online for more than a year, potentially allowing hackers to access sensitive data. This information comes from screenshots and data obtained by 404 […]
Fickle Stealer Distributed via Multiple Attack Chain
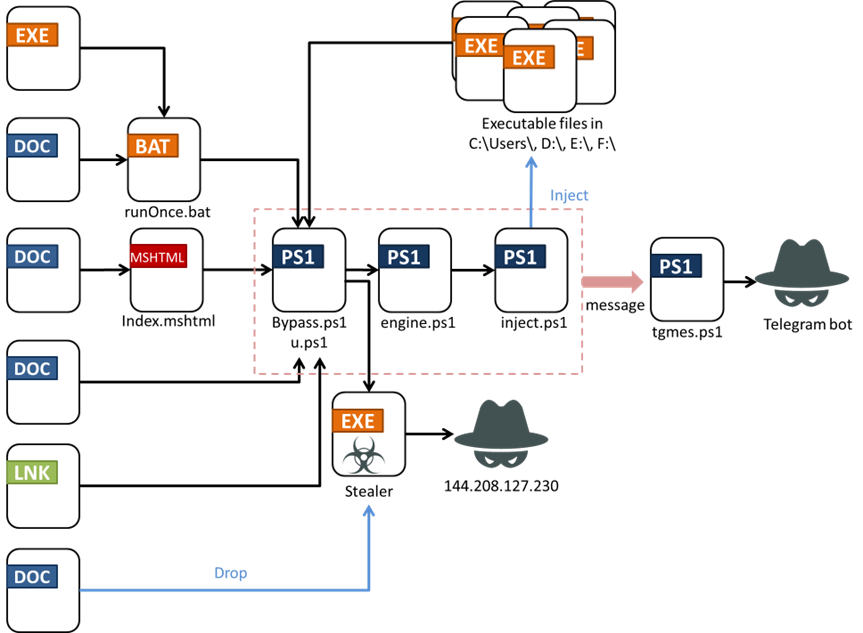
Affected Platforms: Microsoft WindowsImpacted Users: Microsoft WindowsImpact: The stolen information can be used for future attackSeverity Level: High The past few years have seen a significant increase in the number of Rust developers. Rust is a programming language focused on performance and reliability. However, for an attacker, its complicated assembly code is a significant merit. In May 2024, FortiGuard […]
Info Stealing Campaign Uses DLL Sideloading Through Legitimate Cisco Webex’s Binaries for Initial Execution and Defense Evasion
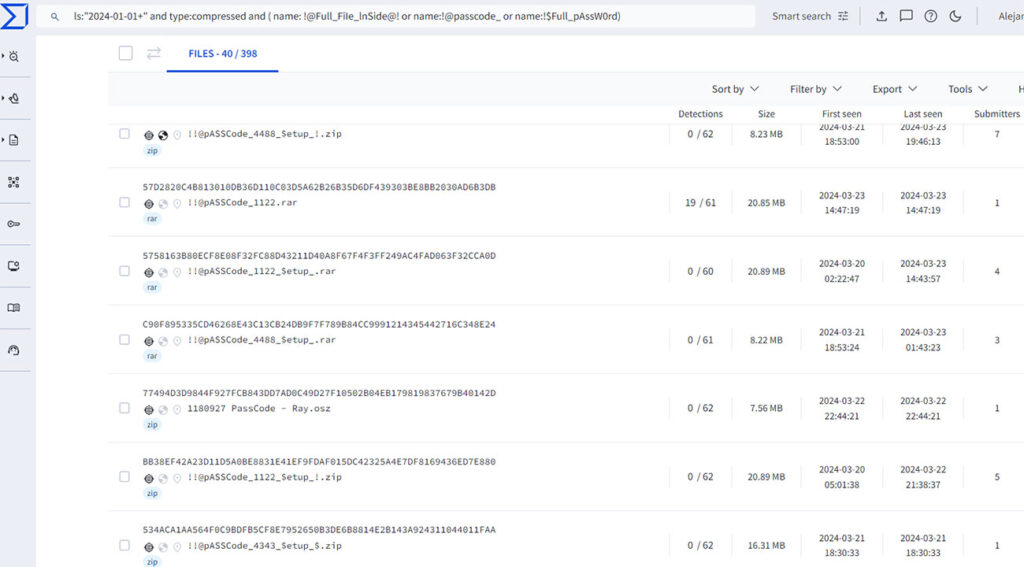
Case Summary It was a quiet Monday morning in March 2024 when the EDR researchers with our Trellix Advanced Research Center identified an interesting sequence of High Confidence detections in Trellix EDR telemetry. Trellix researchers dove right into the opportunity and uncovered what appeared to be a fresh and evasive attack campaign affecting customers in […]
Infostealers Webinar – Hudson Rock

Learn about Infostealers with actual real life breaches caused by Infostealer infections with Leonid Rozenberg, Hudson Rock’s Head of Partnerships & Integrations. To discover how your organization is impacted by Infostealer infections & get a free ethical disclosure, use Hudson Rock’s free tools – www.hudsonrock.com/are-you-compromised
Almost every cyber attack begins at a key ingredient: an Infostealer

Infostealers commit close to the perfect crime. They sneak into your computer, grab your logins, passwords, and anything of value, and then delete themselves on the way out — victims don’t even know they’ve been robbed. We talk to the alleged co-founder of the Meduza infostealer and to some of the people intent on stopping […]
Stealing everything you’ve ever typed or viewed on your own Windows PC is now possible with two lines of code — inside the Copilot+ Recall disaster.
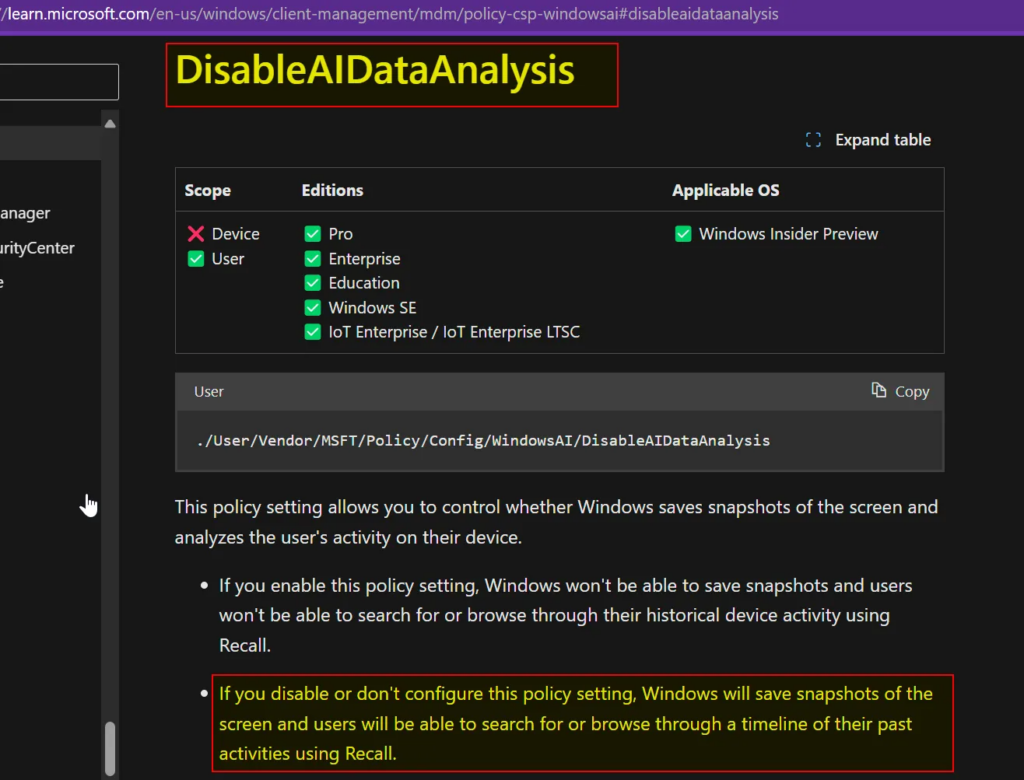
I wrote a piece recently about Copilot+ Recall, a new Microsoft Windows 11 feature which — in the words of Microsoft CEO Satya Nadella- takes “screenshots” of your PC constantly, and makes it into an instantly searchable database of everything you’ve ever seen. As he says, it is photographic memory of your PC life. I got […]
Iluria Stealer; a Variant of Another Discord Stealer

EXECUTIVE SUMMARY At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors who target organizations and individuals. The ‘Iluria Stealer’ is a new malware variant created by the same developer behind the Nikki Stealer, who uses the alias ‘Ykg”. Both share similar code with SonicGlyde; a discord […]
Sapphire Werewolf polishes Amethyst stealer to attack over 300 companies

The adversaries use the open-source SapphireStealer to create their own Infostealer malware for collecting employee authentication data from Russian companies. Since March 2024, the BI.ZONE Threat Intelligence team has been tracking the cluster of activity dubbed Sapphire Werewolf. The threat actor targets Russia’s industries, such as education, manufacturing, IT, defense, and aerospace engineering. Over 300 attacks were […]

