FIN7 Hosting Honeypot Domains with Malicious AI DeepNude Generators – New Silent Push Research

Key findings Executive summary Silent Push Threat Analysts have observed the FIN7 group (aka Sangria Tempest) using new tactics in their malware and phishing attacks. We found that FIN7 has created at least seven websites serving malware to visitors looking to use an “AI Deepnude generator.” The threat group is also continuing to use browser […]
Does the New Infostealer CAPTCHA Infection Actually Work?
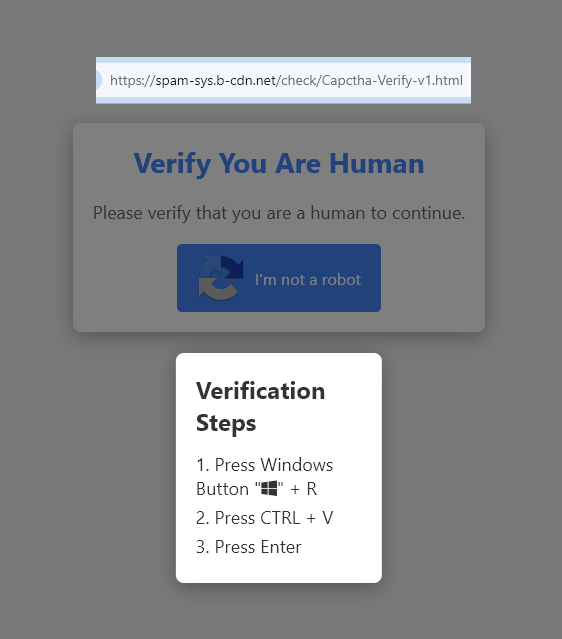
In case you missed it, hackers have been utilizing a new technique to infect victims with Infostealers, it is done by setting a fake Captcha page that prompts the victim to paste a powershell command into their Windows Run which causes a Lumma Infostealer infection. But does it actually work? In reality, the Infostealer infection […]
Actor Uses Compromised Accounts, Customized Social Engineering to Target Transport and Logistics Firms with Malware
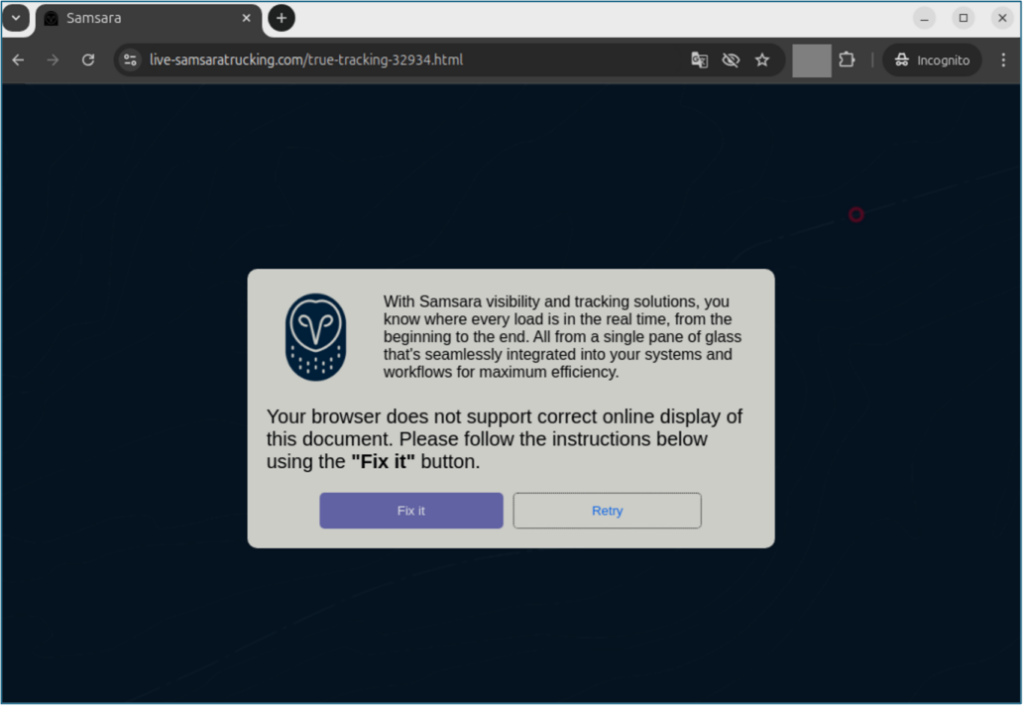
What happened Proofpoint researchers are tracking a cluster of activity targeting transportation and logistics companies in North America to deliver a variety of different malware payloads. Notably, this activity leverages compromised legitimate email accounts that belong to transportation and shipping companies. At this time, it is unclear how the actor achieves access to the compromised […]
Sextortion Is About to Get Much Worse with Infostealers – A Red Flag for Victims
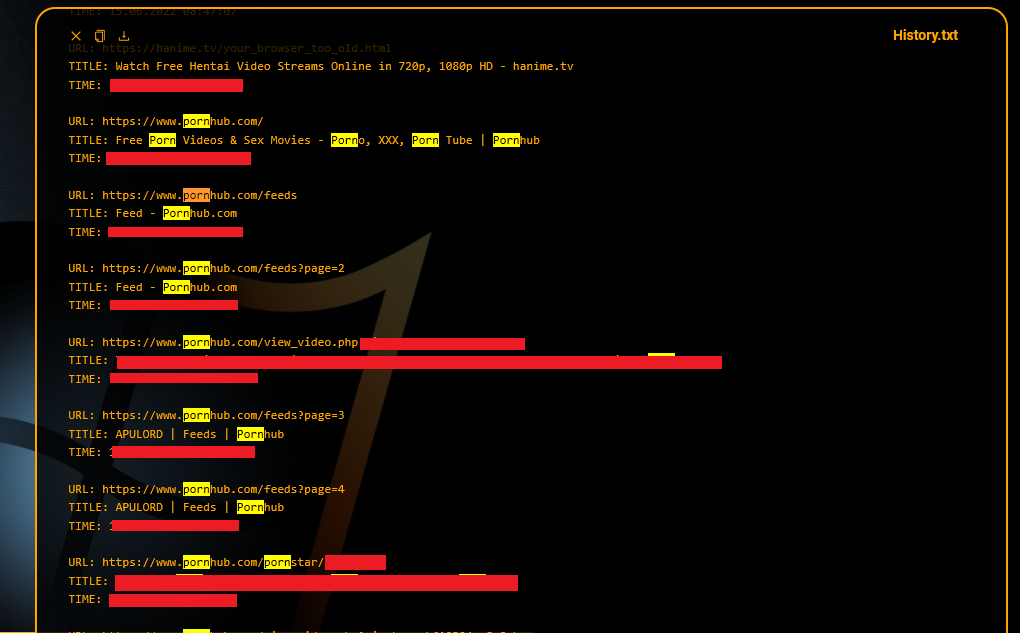
Sextortion schemes are about to take a much darker turn. With the rise of Infostealer malware, the game is changing. Hackers will no longer rely on fake threats or generic scare tactics like Google Street View images. Instead, they now have access to real victim data pulled straight from infected computers—data that includes sensitive browsing […]
Infostealer Infected Computers Could Lead to Cybercriminal Arrests After Exchanges Takedown

German authorities recently took down 47 cryptocurrency exchanges used by ransomware groups, money launderers, and botnet operators. Although the domains have been seized, no arrests have been made so far. The real impact, however, might come from what was left behind by these ransomware groups. By examining the data from these domains through Hudson Rock’s […]
Dissecting Lumma Malware: Analyzing the Fake CAPTCHA and Obfuscation Techniques – Part 2

In Part 1 of our series on Lumma Stealer, we explored the initial attack vector through a fake CAPTCHA page. We observed how the malware deceives users into downloading and executing malicious payloads. In this second series, we delve deeper into the technical details of the Lumma Stealer’s loader, focusing on its obfuscation techniques and how it […]
The journey into Mac OS infostealers
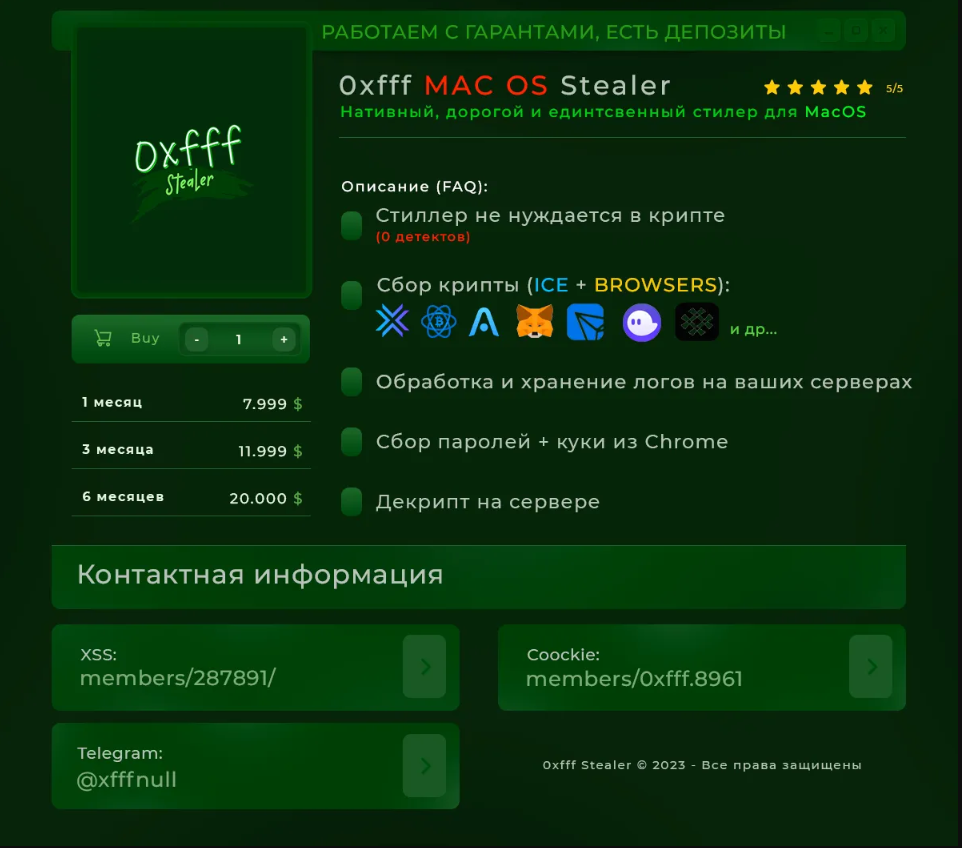
In the past weeks I interviewed some of the Mac OS malware operators that are most known in the wild. Mac OS infostealers are still a trend and a to-be-known thing that I started investigating thanks to the honest words of the people around these products, this couldn’t be possible without the insights of the […]
Cybersecurity Researcher Loses £10,000 in Infostealer Financial DDoS Attack
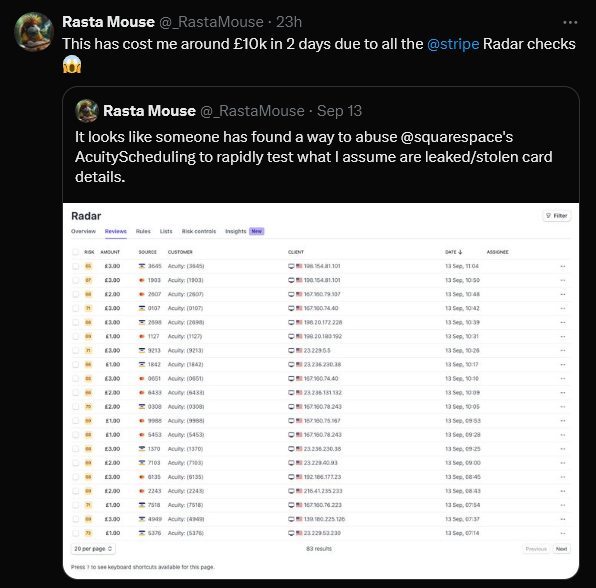
Recently, Rasta Mouse, a well-known cybersecurity researcher and founder of Zero-Point Security Ltd, became the target of an alarming attack that resulted in a staggering loss of £10,000. This incident, which took place while he was selling cybersecurity courses through his company’s website, highlights a new dimension of financial DDoS attacks that combine elements of […]
Infostealer Infections Shed Light on FBI’s Most Wanted Criminals

According to the FBI’s most wanted list — Mujtaba Raza and Mohsin Raza are wanted for allegedly operating a fraudulent online business based in Karachi, Pakistan. Since at least 2011, the business known as SecondEye Solution (SecondEye), aka Forwarderz, allegedly sold digital images in false identity documents including passports, driver’s licenses, bank statements, and national identity cards […]
The silent heist: cybercriminals use information stealer malware to compromise corporate networks

Context Information stealer malware steals user credentials and system information that cybercriminals exploit, predominantly for monetary gain. Information stealers have been observed in cybercrime attacks against multiple organisations and sectors worldwide, including Australia. This publication provides readers with cyber security guidance on information stealer malware, including threat activity and mitigation advice for organisations and their […]
Malicious mods: the Sims 4 infostealer threatens gamers’ security

Overview At the end of January 2024, a newly registered profile with a name very similar to that of a famous modder (PimpMySims4) uploaded a mod file to a mod community platform (ModTheSims). This mod was claimed to be an updated version of a The Sims 4 game mod. A few days later, a newly […]
Ransomware in the Cloud: Scattered Spider Targeting Insurance and Financial Industries
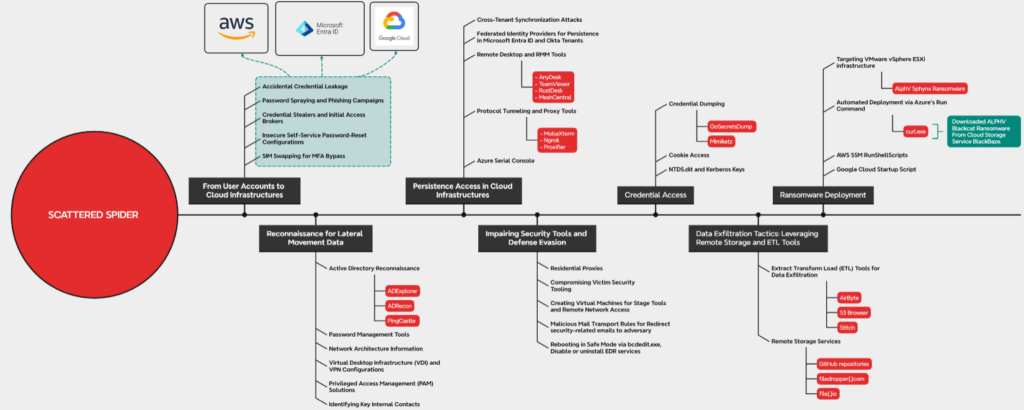
Executive Summary EclecticIQ analysts have conducted in-depth research on ransomware operations, focusing on attacks targeting cloud infrastructures within the insurance and financial sectors. Based on the analysis, the infrastructure and methodologies observed—particularly the automated generation of phishing pages—strongly align with the SCATTERED SPIDER activity cluster [1]. SCATTERED SPIDER frequently uses phone-based social engineering techniques like […]

