De-anonymizing Threat Actors and Exposing Their Infrastructure Using Infostealer Intelligence
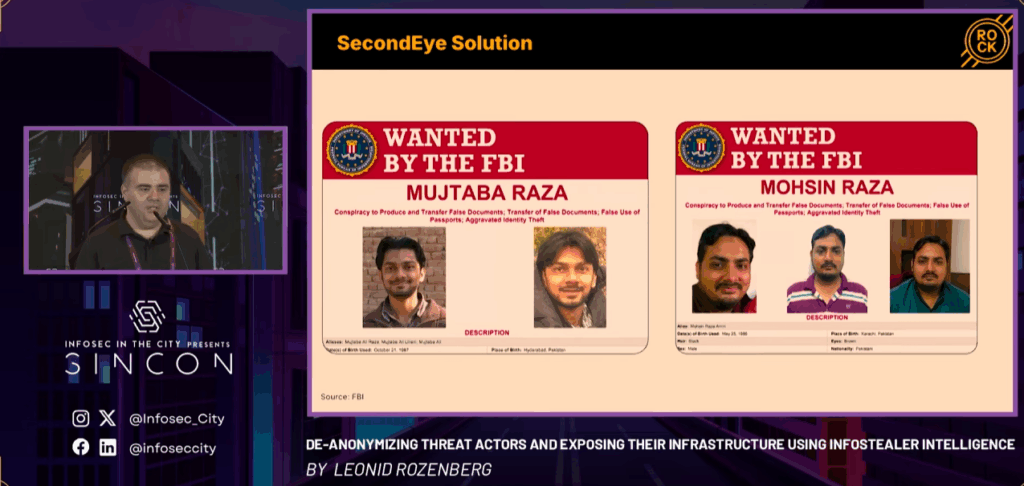
Speaker: Leonid Rozenberg, Cybercrime Researcher, Hudson Rock. Infostealing malware has become a near-perfect tool for cybercriminals, enabling the theft of sensitive data with remarkable efficiency. However, there are moments when the malware backfires, exposing the attackers themselves. This talk delves into cases where cybercriminals accidentally infected their own systems with Infostealer malware, providing Hudson Rock […]
Exclusive Look Inside a Compromised North Korean APT Machine Linked to The Biggest Heist in History
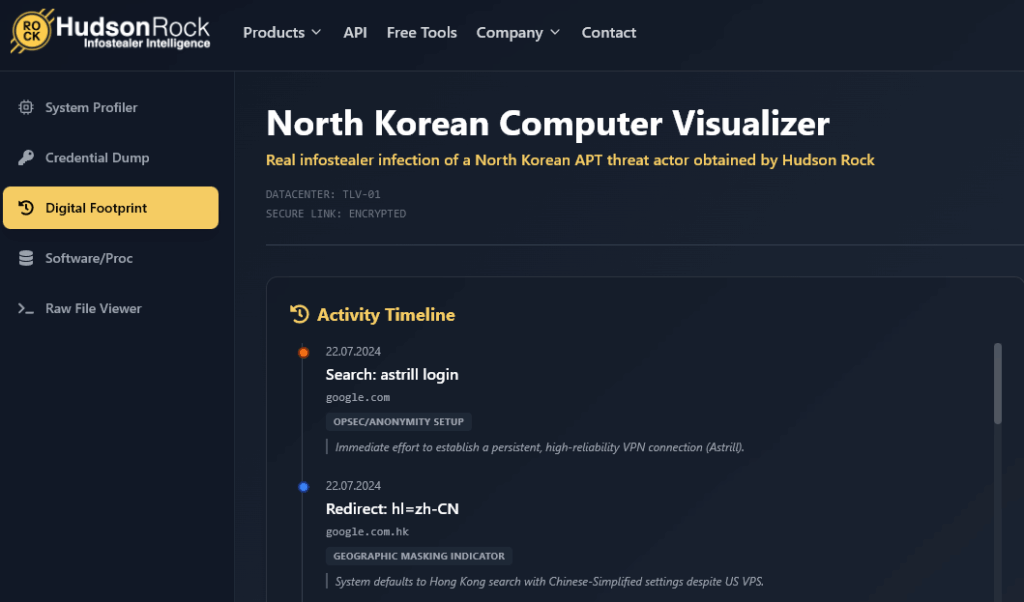
*Interactive simulator can be accessed via desktop – www.hudsonrock.com/northkorean In the world of Threat Intelligence, we are usually looking at the aftermath of an attack: the encrypted servers, the stolen databases, or the fraudulent transactions. Rarely do we get a look through the eyes of the attacker. But even state-sponsored hackers make mistakes. And sometimes, […]
The Infostealer to Government-Backed Hackers Pipeline

The Infostealer-to-APT Pipeline – Hudson Rock Infographic HUDSON ROCK THE INFOSTEALER TO APT PIPELINE How stolen diplomatic credentials fuel cyber-political power plays. The Dangerous Escalation Opportunistic Infection Random malware download Diplomat Compromised Valid MOFA credentials stolen APT Espionage State-sponsored attacks Global Diplomatic Exposure Hudson Rock detected infections exposing Ministry of Foreign Affairs (MOFA) credentials across […]
How Hackers Are Actually Using Infostealers (Top 4 Real Methods)
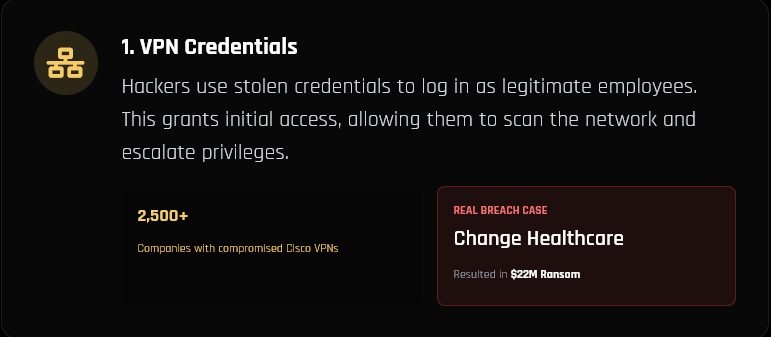
How Hackers Really Use Infostealers – Hudson Rock Infographic HUDSON ROCK HOW HACKERS REALLY USE INFOSTEALERS An analysis of the specific tactics used in the biggest recent cyber breaches. 30,000,000+ Infected Computers Monitored Major Victims AT&T, Uber, EA, Ticketmaster Top Tactics VPNs, Webmail, Slack, Cloud 1. VPN Credentials Hackers use stolen credentials to log in […]
Microsoft’s New Update Creates an Agentic OS Infostealer Attack Vector
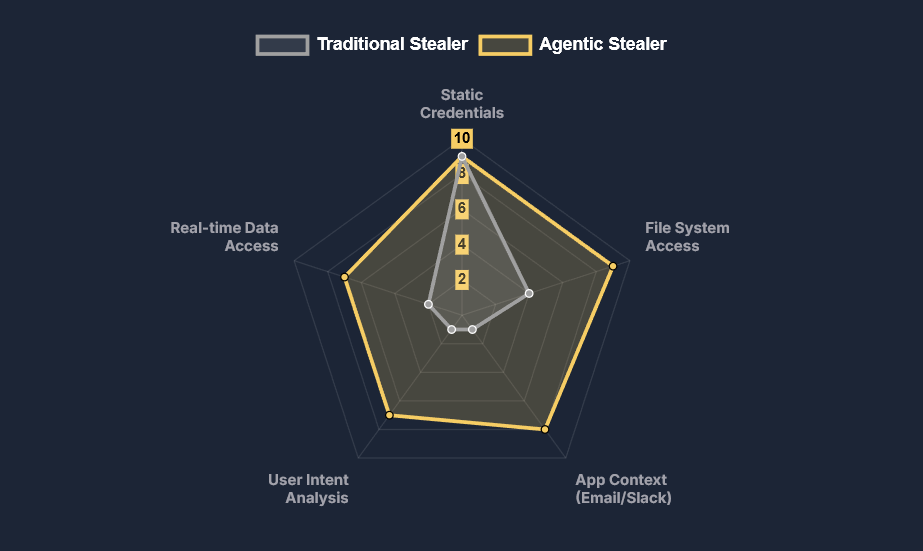
Infographic: The Agentic OS & Hudson Rock Defense HUDSON ROCK Threat Intelligence Report The Agentic OS Attack Vector Microsoft’s new Windows 11 update centralizes data for AI agents. It’s the ultimate convenience for users and the ultimate shortcut for Infostealers. A Analyst Get insights or trends R Researcher Generate a report @| Tools Search The […]
Nikkei Breached: Infostealer Infection Grants Access to 17K+ Employee Slack Chat Histories

Over 17,000 employees and partners now face the fallout from a breach that started with a single infostealer infection on a Japanese computer in August 2025, ultimately handing attackers the keys to Nikkei’s Slack at nikkeidevs.slack.com. Hudson Rock‘s deep dive into stolen credential logs reveals the mechanics behind this intrusion, the incident spotlights how Infostealers […]
Approaching Infostealer Devs: a Brief Interview with AURA

To completely understand what’s going on in a market that has been growing in the last years I found mandatory to know which players are dominating it. Always remember that behind every user of the Internet there is another human like you, so if you can be kind enough to reach them and they agree, […]
Russian Authorities Bust Meduza Infostealer Developers: Young Hackers Detained in Major Cybercrime Crackdown

In a swift operation that underscores Russia’s growing crackdown on domestic cyber threats, the Ministry of Internal Affairs (MВД) has arrested a group of young IT specialists accused of creating and distributing the Meduza Infostealer malware. This credential-harvesting tool, which has been circulating on underground forums since mid-2023, specializes in siphoning login details, cryptocurrency wallet […]
Logins.zip Leverages Chromium Zero-Day: Stealthy Infostealer Builder Promises 99% Credential Theft in Under 12 Seconds
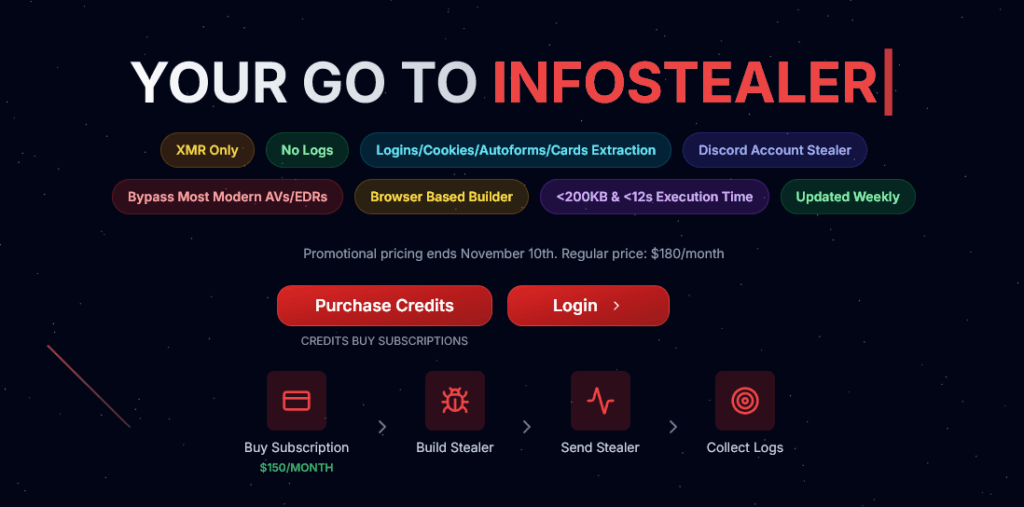
In the ever-evolving landscape of cyber threats, Hudson Rock‘s research team has uncovered a potent new Infostealer builder: Logins(.)zip. Marketed as the “go-to infostealer” on underground forums, this web-based tool exploits Chromium browser vulnerabilities to achieve near-total credential extraction – up to 99% of saved logins, cookies, and autofills, in just 12 seconds post-infection. This […]
Infostealers Disguised as Free Video Game Cheats
It is human nature to be competitive, to try your best when competing against others. It is no different when it comes to video games. Major E-Sports tournament prize pools regularly reach the multi millions. Last year the CS2 PGL Major hosted in Copenhagen had a prize pool of $1.25M. Esports along with normal sports […]
Email Leaked Credentials Search
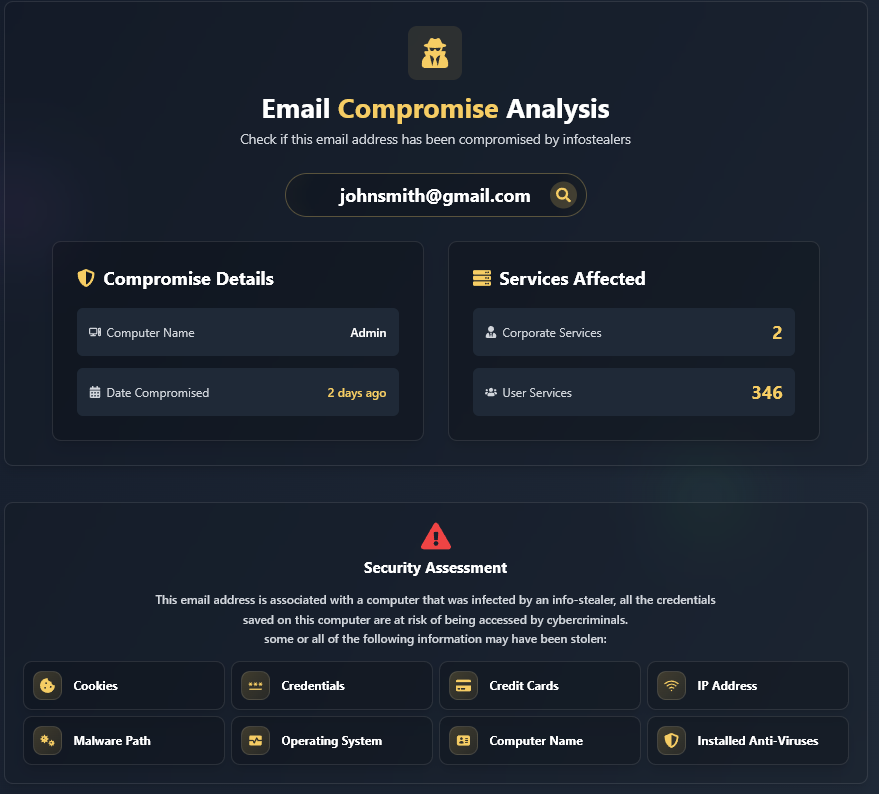
How to Check if an Email Address Has Been Compromised To determine if an email address has been affected by an Infostealer infection and has leaked credentials involved, you can use the free tool provided by Hudson Rock, our cybersecurity firm that specializes in cybercrime intelligence. Here are the steps: * You can receive a one-time […]
Username Leaked Credentials Search
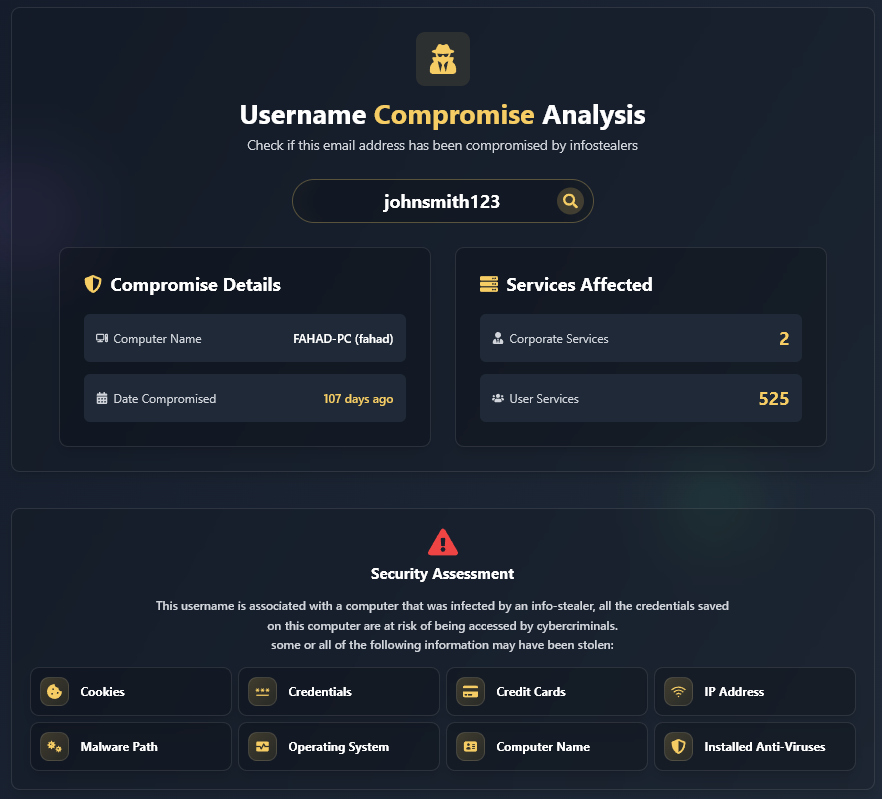
How to Check if a Username Has Been Compromised To determine if a username has been affected by an Infostealer infection and has leaked credentials involved, you can use the free tool provided by Hudson Rock, our cybersecurity firm that specializes in cybercrime intelligence. Here are the steps: * You can receive a one-time historical ethical […]

