Hy-Vee Hacked: Infostealers Enable Stormous Group’s 53GB Atlassian Data Heist

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach courtesy of the Stormous ransomware group. The attackers claim they’ve infiltrated Hy-Vee’s Atlassian accounts, specifically Confluence and Jira, using stolen credentials, Hudson Rock traced back these credentials to various Infostealer […]
Paraguay’s Biggest Data Breach: Infostealers Fuel Massive 7.4M Citizen Data Leak
In a cybersecurity catastrophe that’s rocked Paraguay to its core, a staggering 7.4 million citizen records, nearly the entire population’s personally identifiable information (PII), have been leaked on the dark web. Evidence for the initial access which enabled this hack point to an Infostealer infection that compromised a government employee’s credentials, granting cybercriminals access to […]
16 Billion Credentials Leak: A Closer Look at the Hype and Reality Behind the “Massive” Data Dump
Recent reports of a 16 billion credentials leak have sparked widespread concern, with claims it’s one of the largest breaches ever. However, Hudson Rock’s analysis shows this “leak” is far less significant than suggested, consisting of recycled, outdated, and potentially fabricated data rather than a new breach. Here’s a clear breakdown of the incident and […]
Nobitex Breach: Infostealers Expose Critical Employee Credentials in Latest Crypto Exchange Hack
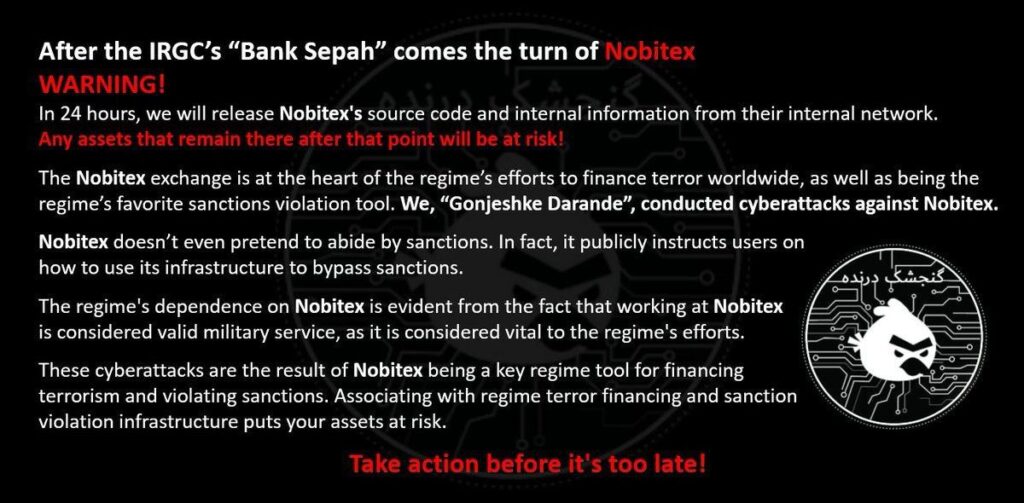
The cryptocurrency world has been rocked yet again, this time with the Nobitex exchange finding itself in the crosshairs of a sophisticated cyberattack. Reported earlier today, the Iranian crypto platform suffered a massive $81.7 million loss due to a hack claimed by the group “Gonjeshke Darande”, allegedly linked to Israel, which claims affiliation with Israel […]
20,000 malicious IPs and domains taken down in INTERPOL infostealer crackdown
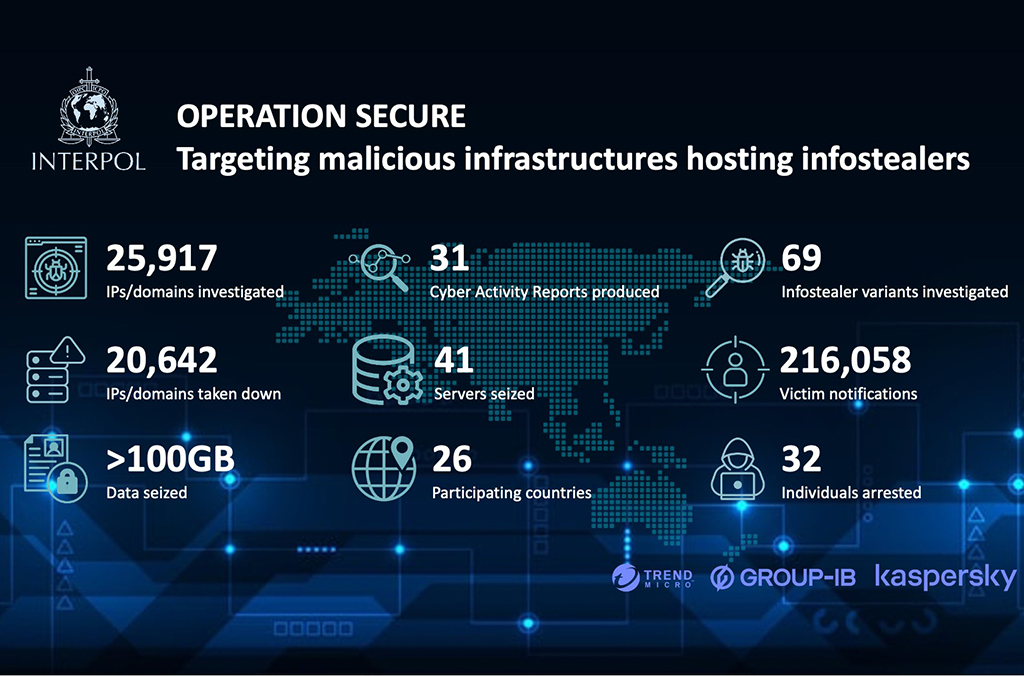
SINGAPORE – More than 20,000 malicious IP addresses or domains linked to information stealers have been taken down in an INTERPOL-coordinated operation against cybercriminal infrastructure. During Operation Secure (January – April 2025) law enforcement agencies from 26 countries worked to locate servers, map physical networks and execute targeted takedowns. Ahead of the operation, INTERPOL cooperated […]
Mandiant Exposes Salesforce Phishing Campaign as Infostealer Malware Emerges as a Parallel Threat
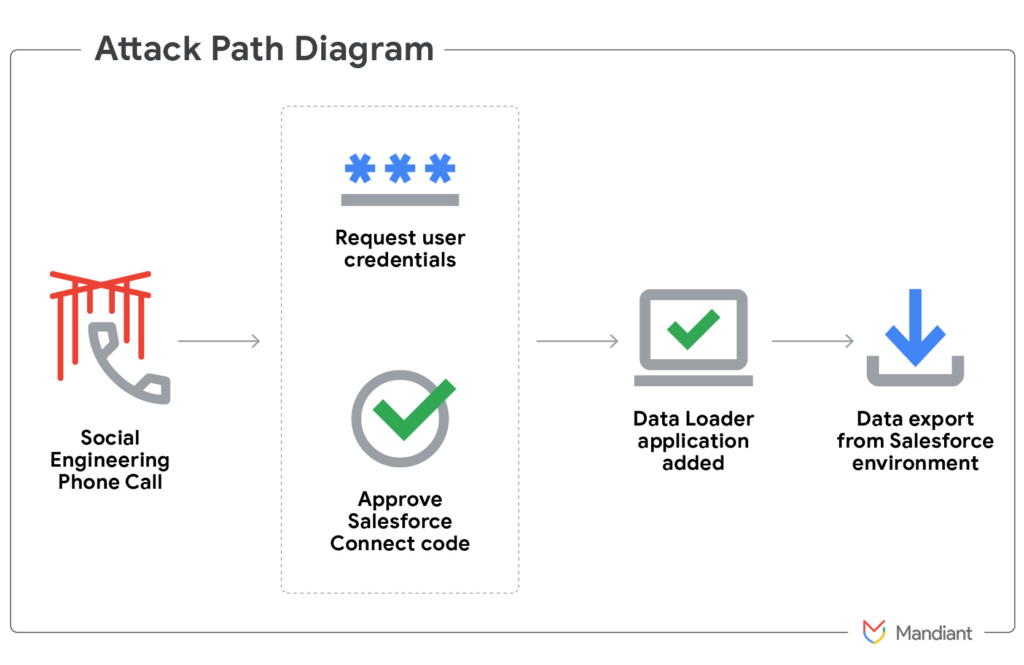
Mandiant has exposed a sophisticated campaign using voice phishing to gain access to Salesforce accounts. Attackers impersonated IT support staff over the phone to trick victims into providing multi-factor authentication codes, allowing access to sensitive Salesforce environments. Once inside, the actors exfiltrated data and used it for extortion purposes. This operation highlights a growing trend […]
Pakistan Telecommunication Company (PTCL) Targeted by Bitter APT During Heightened Regional Conflict
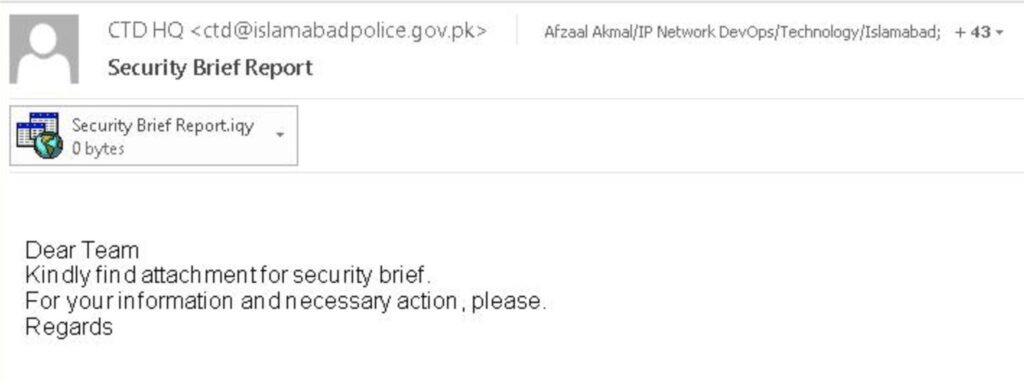
Executive Summary On May 7, 2025, during the active military escalation between Pakistan and India—specifically in the context of India’s military campaign ‘Operation Sindoor’—, EclecticIQ analysts observed that Bitter APT (also known as TA397) [1] very likely targeted the Pakistan Telecommunication Company Limited (PTCL) workers [2] in a spear phishing campaign very likely to deliver malware. Analysts assess that, […]
Russian ‘Laundry Bear’ Hackers Breach Dutch Police Using Infostealers

A new Russian hacking group, “Laundry Bear” (aka “Void Blizzard”), breached the Dutch police in October 2024, stealing contact details of thousands of officers. The attack, highly likely linked to a September 12, 2024, infostealer infection of a police employee, compromised VPN credentials and politie.nl session cookies, enabling a pass-the-cookie attack. Hudson Rock data confirms […]
Void Blizzard’s Infostealer Tactics Target Critical Sectors for Russian Espionage

Executive summary: Void Blizzard is a new threat actor Microsoft Threat Intelligence has observed conducting espionage operations primarily targeting organizations that are important to Russian government objectives. These include organizations in government, defense, transportation, media, NGOs, and healthcare, especially in Europe and North America. They often use stolen sign-in details that they likely buy from […]
Meet Enki: Hudson Rock’s AI Breakthrough for Infostealer Analysis
We’re excited to announce a game-changing addition to Hudson Rock’s capabilities: our innovative AI agent, Enki, engineered to transform how you tackle Infostealer infections. With Enki, you can ask any question about an infection and receive precise, actionable insights in seconds, saving hours of manual analysis. Infostealer infections generate vast amounts of data, from browsing […]
Lumma infostealer malware operation disrupted, 2,300 domains seized

Earlier this month, a coordinated disruption action targeting the Lumma malware-as-a-service (MaaS) information stealer operation seized thousands of domains and part of its infrastructure backbone worldwide. This effort involved multiple tech companies and law enforcement authorities, resulting in Microsoft’s seizure of approximately 2,300 domains after legal action against the malware on May 13, 2025. At the […]
Stealing the Future: Infostealers Power Cybercrime in 2025

By [Alon Gal] | April 2025 Infostealers have become a cornerstone of cybercrime in 2025, infiltrating systems to steal credentials and sensitive data, enabling devastating follow-on attacks. This article for Infostealers.com synthesizes insights from Verizon’s 2025 Data Breach Investigations Report (DBIR), IBM’s X-Force Threat Intelligence Index 2025, and perspectives from cybersecurity leaders like Check Point, Hudson Rock, Huntress, Recorded Future, CrowdStrike, SpyCloud, Sophos, and Mandiant. It […]


