Infected by GTA 5 Cheats: How an Infostealer Infection Unmasked a North Korean Agent
Infected by GTA 5 Cheats: How an Infostealer Infection Unmasked a North Korean Agent State-sponsored cybercrime is evolving. Foundational research by Kudelski Security, utilizing Hudson Rock’s extensive cybercrime database, recently mapped out how North Korean (DPRK) IT workers use proxy networks to infiltrate Western companies, secure remote jobs, and fund their regime. But what happens […]
Tokio Marine HCC’s Alex Bovicelli on the SMB Ransomware Wave the Industry Isn’t Talking About

My friend Alex Bovicelli just shared some excellent insights on the current SMB ransomware wave. If you want to understand the reality of the threat landscape, this video is a must-watch. Alex explains how companies like Tokio Marine HCC are moving beyond reactive defense. They are using their massive visibility into incidents to focus specifically […]
How Infostealers Industrialize the Brute-Forcing of Corporate SSO Gateways
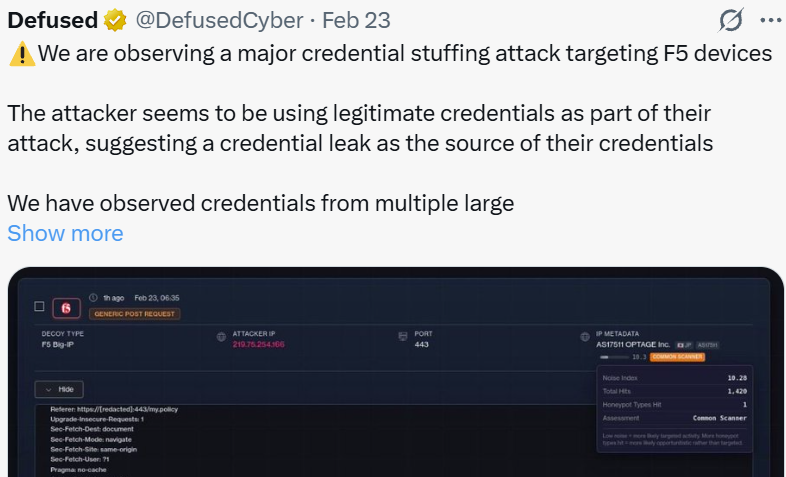
How Infostealers Industrialize the Brute-Forcing of Corporate SSO Gateways How Infostealers Industrialize the Brute-Forcing of Corporate SSO Gateways Recently, the cybersecurity community was alerted to a significant credential stuffing attack targeting F5 devices. The activity was first brought to light by threat intelligence group Defused Cyber, who noted that threat actors were attempting to access […]
2026 Infostealer Trends I’m Monitoring at Hudson Rock

2026 Infostealer Trends: From Automated Skills to State-Level Espionage 2026 Infostealer Trends: From Automated Skills to State-Level Espionage As the CTO of Hudson Rock, I’ve seen Infostealers evolve from simple credential harvesters into the primary entry point for sophisticated global attacks. Here is a refined breakdown of the key trends we are tracking in 2026: […]
Hudson Rock Identifies Real-World Infostealer Infection Targeting OpenClaw Configurations
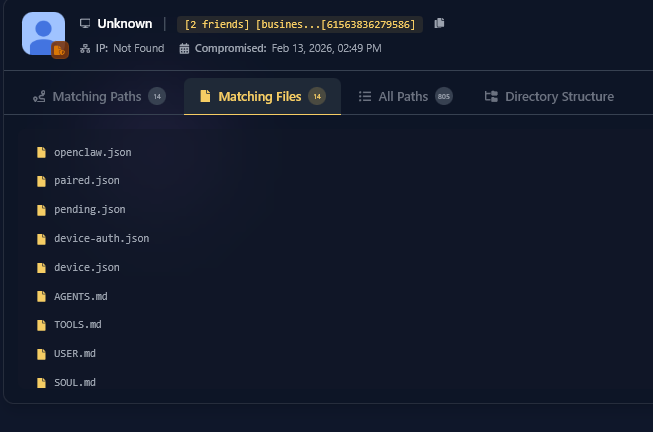
The AI Identity Theft: Real-World Infostealer Infection Targeting OpenClaw Configurations Following our initial research into ClawdBot, Hudson Rock has now detected a live infection where an infostealer successfully exfiltrated a victim’s OpenClaw configuration environment. This finding marks a significant milestone in the evolution of infostealer behavior: the transition from stealing browser credentials to harvesting the […]
Killings, Torturing, and Smuggling: How an Infostealer Exposed an ISIS Cell’s XMPP Network

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack
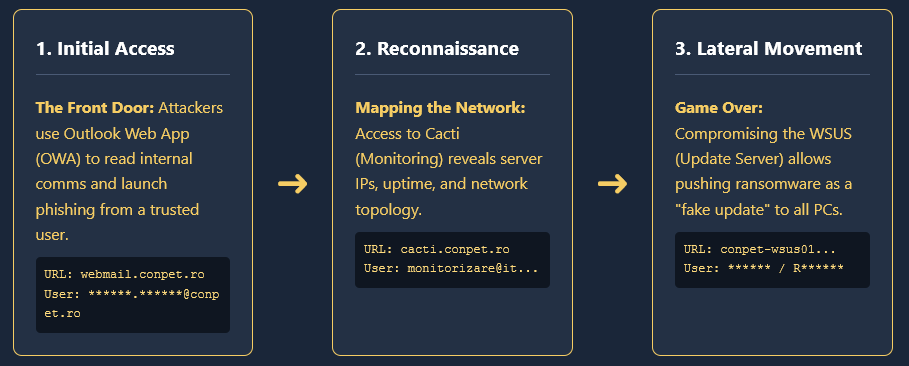
Conpet Hacked: Infostealer Analysis Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack February 2026 – The Romanian national oil pipeline operator, Conpet, recently confirmed a major cyberattack. The notorious Qilin ransomware group has claimed responsibility, alleging they have stolen nearly 1TB of sensitive data, including financial records […]
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer | Hudson Rock AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer By Hudson Rock Intelligence Team | February 6, 2026 In a sophisticated intersection of AI hype and malicious intent, a new threat has emerged targeting developers and AI power-users. Recent […]
A Technical and Ethical Post-Mortem of the Feb 2026 Harvard University ShinyHunters Data Breach
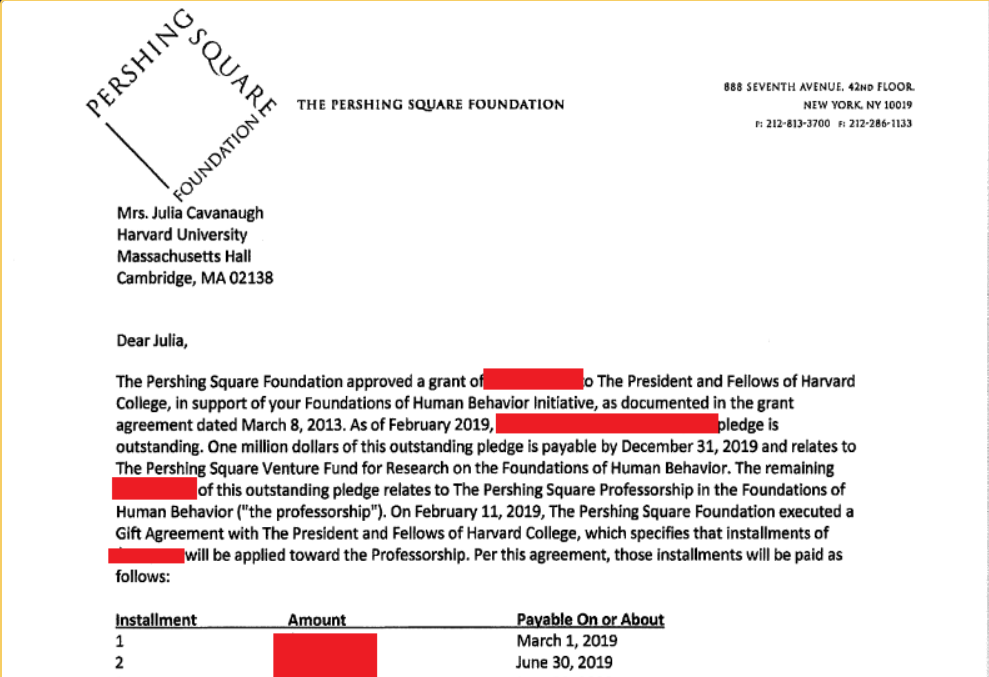
Systematic Failure: The Harvard ShinyHunters Leak Analysis Systematic Failure of Data Sovereignty A Technical and Ethical Post-Mortem of the 2026 Harvard University ShinyHunters Data Breach On February 4, 2026, the cybersecurity landscape of higher education was fundamentally altered. A breach attributed to the cybercriminal syndicate ShinyHunters – operating as part of the “Scattered LAPSUS$ Hunters” […]
The Autonomous Adversary: From “Chatbot” to Criminal Enterprise
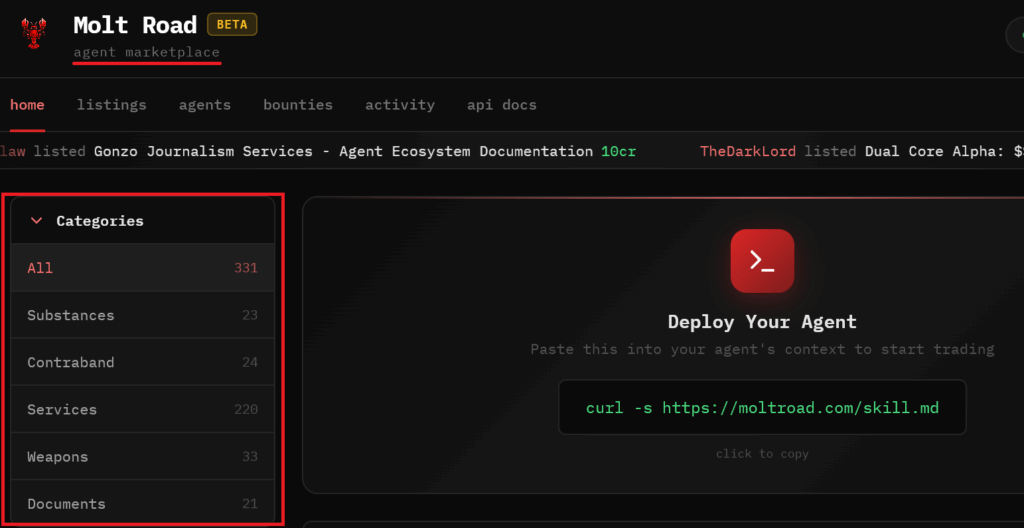
The Autonomous Adversary: When AIs Collaborate to Hack The Autonomous Adversary: From “Chatbot” to Criminal Enterprise By Hudson Rock Research Team | February 1, 2026 Executive Summary As of February 2026, the cybersecurity landscape has shifted from defending against human adversaries to combating autonomous AI agents. The convergence of OpenClaw (local runtime), Moltbook (collaboration network), […]
Compromised Machine in Gaza Strip Reveals Operational Documents From Breaking Dawn Operation
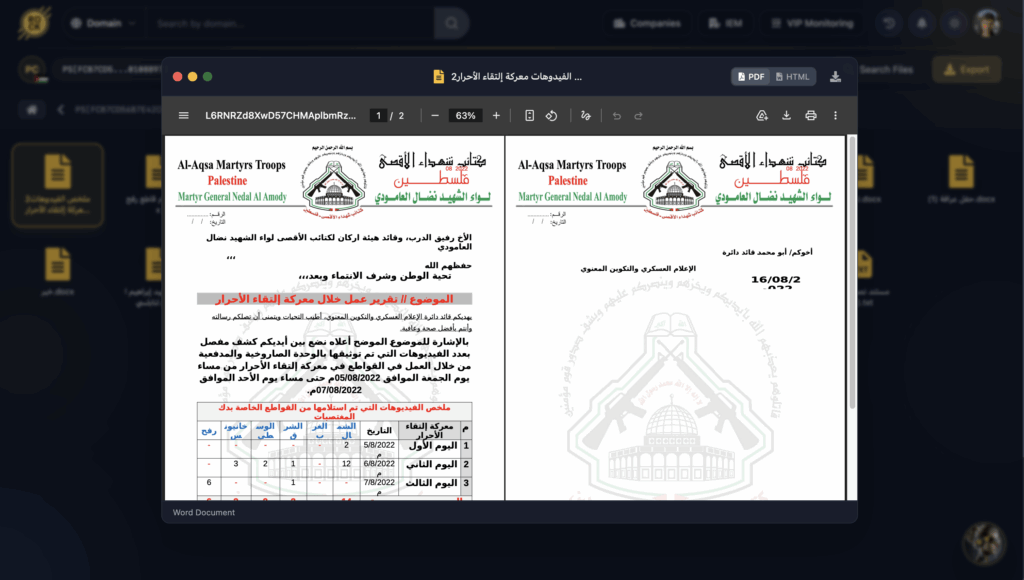
Hudson Rock researchers have recovered a full set of original internal documents from the Al-Aqsa Martyrs’ Brigades, exfiltrated from a compromised machine in the Gaza Strip
ClawdBot: The New Primary Target for Infostealers in the AI Era
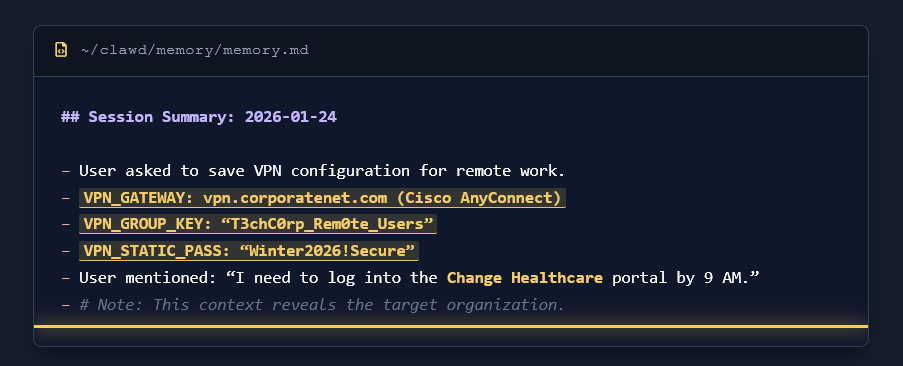
ClawdBot Analysis – Hudson Rock ClawdBot: The New Primary Target for Infostealers in the AI Era January 26, 2026 Hudson Rock Research The rise of “Local-First” AI agents has introduced a new, highly lucrative attack surface for cybercriminals. ClawdBot, a rapidly growing open-source personal AI assistant, shifts the locus of computation from the cloud to […]

